By Salvador Mendoza from Metabase Q’s R&D Team
Metabase Q’s offensive security team, Ocelot, discovered a potential abuse of an inadequate issuer business practice to reset the PIN RETRY Counter (PRC) on Europay, MasterCard, Visa (EMV) chip contact cards. It would lead to a new attack called Pin Automatic Try Attack (PINATA). PINATA could brute force all 10,000 PIN combinations, from 0000 to 9999, in millions of physical EMV cards, until the correct PIN is found for certain cards issued by various banking institutions.
PINATA (PIN Automatic Try Attack)
As more smart payment systems, such as integrated circuit cards are incorporated, attackers are finding new ways to access the information stored on them EMV cards also known as Chip & PIN, or Chip contact cards, that have a comparatively secure verification method through a Personal Identification Number (PIN) now face a new threat. A compromised PIN might lead to greater fraudulent transactions due to the ability to evade the issuer antifraud algorithm mechanisms, because it will be impossible to differentiate between the owner of the card and the malicious individual.
Cardholder Verification Method (CVM) is a mechanism used to verify a proper transaction when a user tries to employ an EMV smart card. These verification values are prioritized by implementing an ordered list that is stored in the Integrated Circuit Card (ICC). The terminal or Point of Sales System (PoS) has to determine which CVM the card will perform. Following specific logic rules to process a transaction, the terminal and EMV smart cards share information to decide if the transaction will be authorized or if it will be declined. One of the most important stages is the verification process.
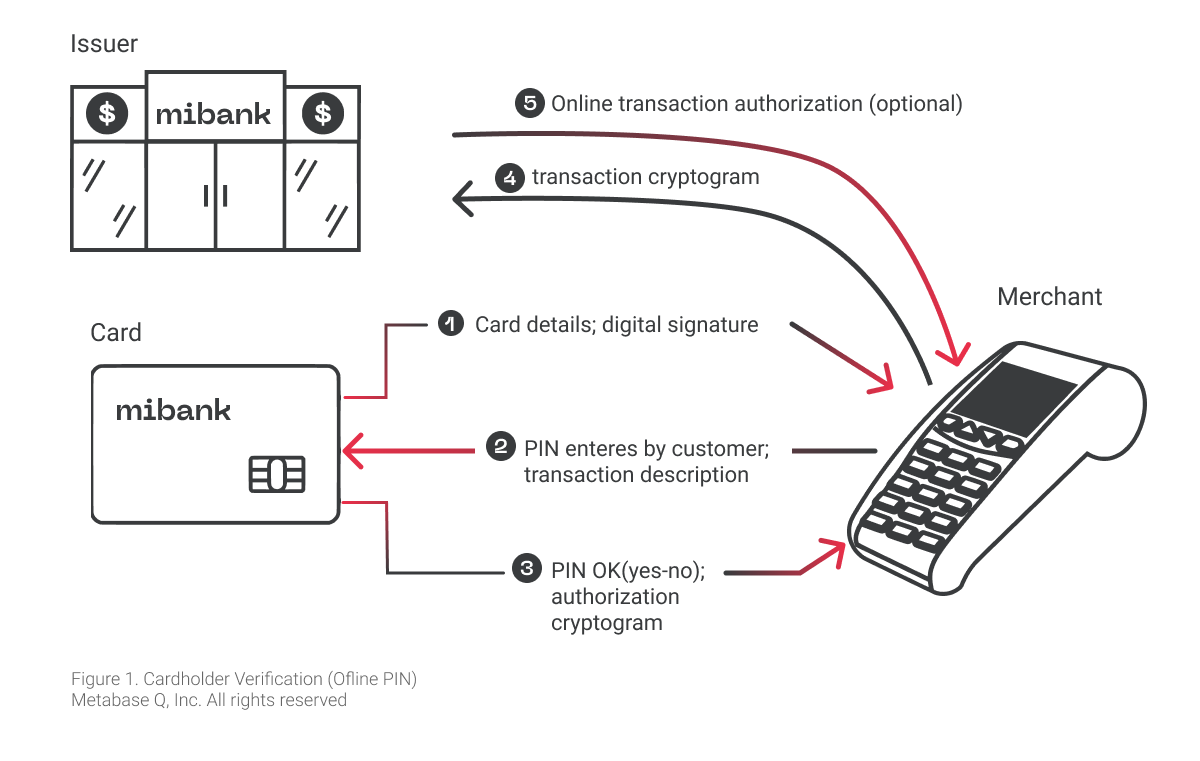
To follow the Cardholder Verification Method, the EMV smart card has to pass the card authentication. After this, the normal process starts reading data from the card’s PIN RETRY Counter (PRC), which indicates how many tries are available to process a PIN attempt to protect against a brute force attack. Normally, this counter is limited to 3 attempts, protecting any chance to identify a 4 digit PIN with 10,000 possibilities. If a client attempts 3 times in a row with an incorrect PIN, the EMV smart card will set this counter to zero and block any more attempts to the PIN mechanisms. The PIN RETRY Counter can only be reset through the assistance of the banking institution.
Ocelot, Metabase Q’s Offensive Security team, discovered that it is possible to brute force all 10,000 PIN combinations on millions of EMV cards. The PIN Automatic Try Attack (PINATA) takes advantage of a poor implementation of the CVM verification system and a compromising issuer practice to reset the PRC.
To carry out the attack, a malicious user can implement a Man-in-The-Middle (MiTM) device to control the terminal commands and the PIN and Chip card responses. At this point, the EMV card can reset the PIN RETRY Counter to try 3 more different PINs and repeat this loop until a correct PIN is found.
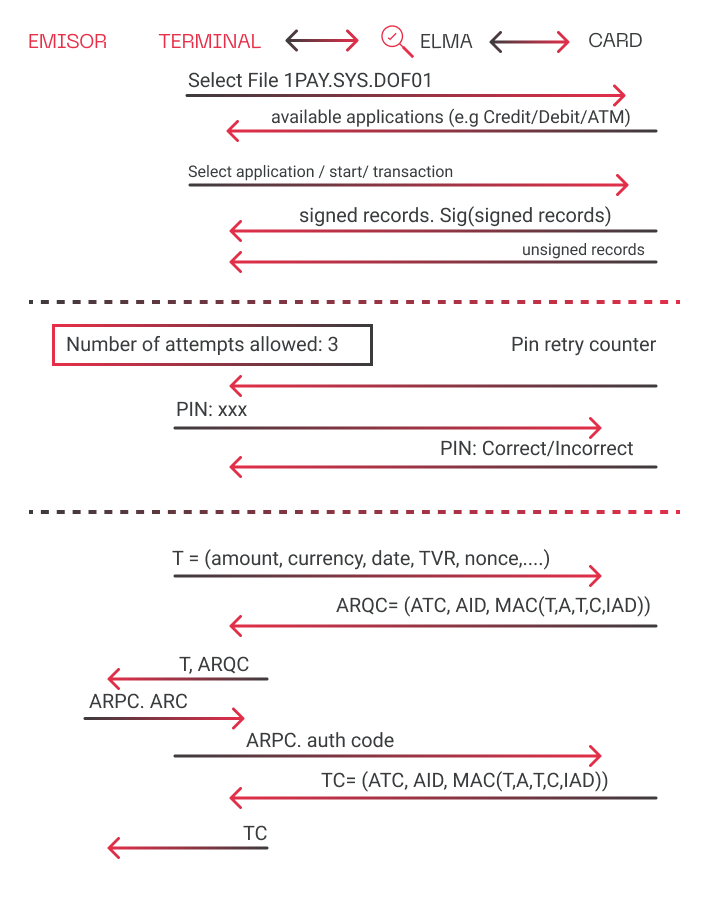
The PINATA method was discovered by Metabase Q’s Offensive Security Team, Ocelot, with the support of ELMA, a specialized proprietary tool that works as an advanced MiTM attack emulator for EMV contact technologies.
ELMA is a technology developed by Ocelot’s Research and Development (R&D) team, capable of controlling the whole communication between the terminal and EMV card. It processes commands and responses before they arrive at the respective destination, making it possible to alter the information in real-time. ELMA was used as a bridge between the card and the terminal to gain visibility of the transaction. To replicate the attack, the procedures in the transaction were automated.
Through advanced engineering methods and innovation, the latest version of ELMA not only facilitated the discovery of PINATA but allowed the team to be the first to create the attack, find and report the breach, and replicate the attack to identify the details of its operation.
About Metabase Q
Metabase Q protects organizations from financial and reputational losses with smarter cybersecurity. Through continuous audit and analysis, Metabase Q calibrates cyber defenses that deliver security effectiveness allowing organizations to grow and innovate unhindered by cyber threats. Financial institutions covering 80% of transactions in Mexico, 10 of the largest enterprises in Latin America as well as government agencies rely on Metabase Q to continuously protect their systems and data from cyberattacks. The Ocelot offensive cybersecurity team represents the best of the best, partnered together to transform cybersecurity in the region. Ocelot threat intelligence, research, and offensive skills power Metabase Q’s solutions.
To learn more about Metabase Q, the Ocelot offensive cybersecurity team and Security-as-a-Service visit https://www.metabaseq.com/.