By Metabase Q’s Ocelot Threat Intelligence Team
// Introduction
LAPSUS$ is a cybercriminal group focused on cyberextortion with one single main objective, money. Hence the money symbol in their name. It’s important to mention that their way of acting is not traditional, this group enjoys the attention, so they choose to announce all their activities for them to be seen by the public. They have even gone as far as launching surveys with questions about their next victims.
The group appeared in August 2021, when mobile telephone clients in the United Kingdom began receiving threatening text messages. Most cybercriminal groups who are dedicated to cyberextortion use ransomware, however, LAPSUS$ focuses on using a combination of stolen credentials, SIM swapping and social engineering to gain access to confidential files, and they monetize their operations through leaks announced on Telegram.
Where is LAPSUS$ from? Derived from diverse analyses conducted, there is a medium-high degree of confidence that the origin of the group could be Brazil since, at the beginning, their operations were focused on creating leaks against organizations and government entities in Brazil and Latin America.
On the other hand, this group has also been categorized for operating with different types of malware commodity and Malware as a Service. Recently, we learned that LAPSU$ is working with Redline Stealer, a malware observed in the Latin American region, which has mainly affected users in Mexico.
// Key Points
LAPSUS$ utilizes the Redline Stealer capabilities, especially the infostealer module, which allows them to steal valid credential to then use them to identify a remote access to a system. LAPSUS$ has the possibility to acquire those abilities due to the Malware as a Service business model, which is offered in the Deep Dark Web (DDW) (See Figure 1 and 2), allowing the group to focus on identifying new cyberextortion vectors. The Ocelot Threat Intelligence Team follows this group and other groups in both open and private forums, with the objective of monitoring new variants and/or new attack strategies in the region:
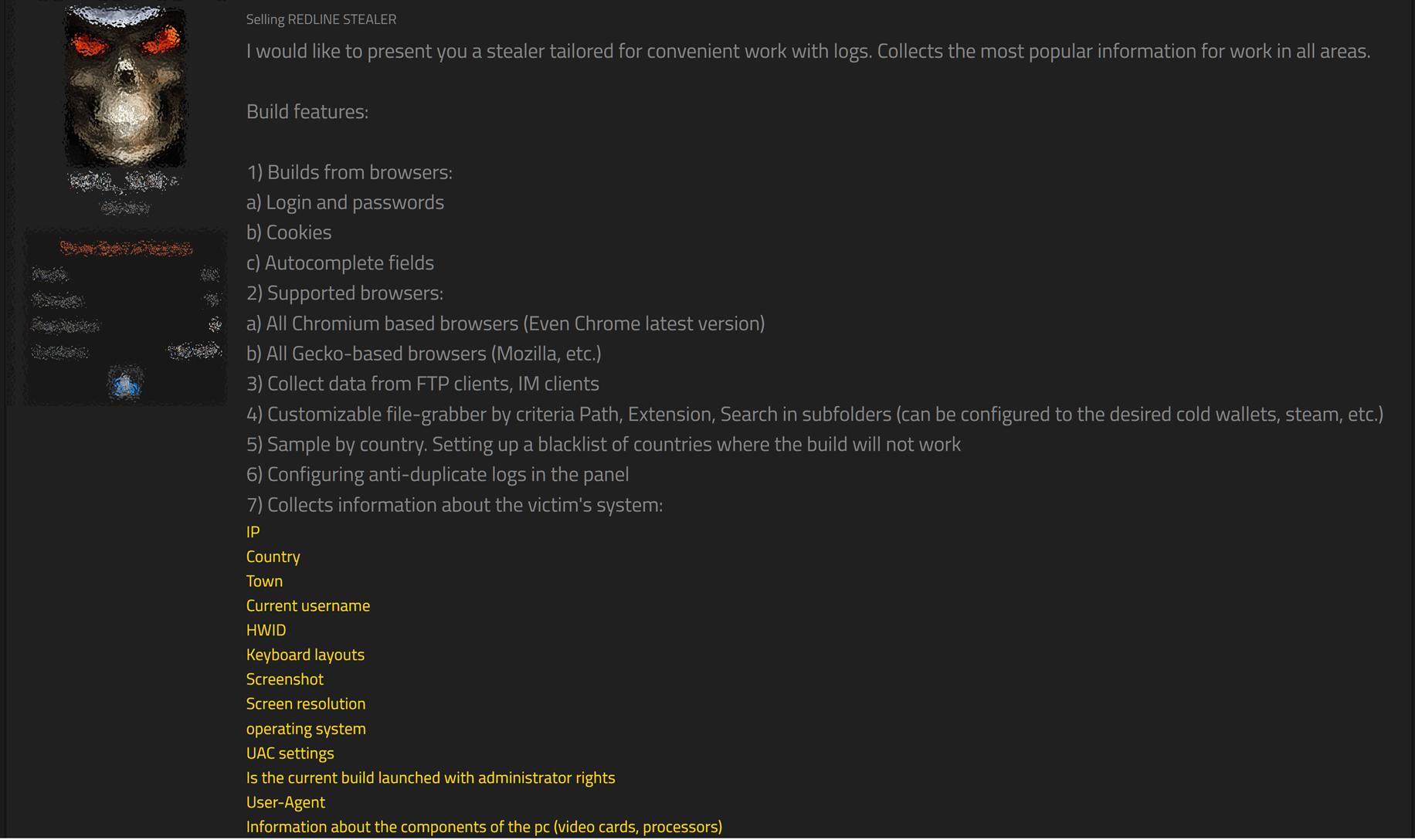
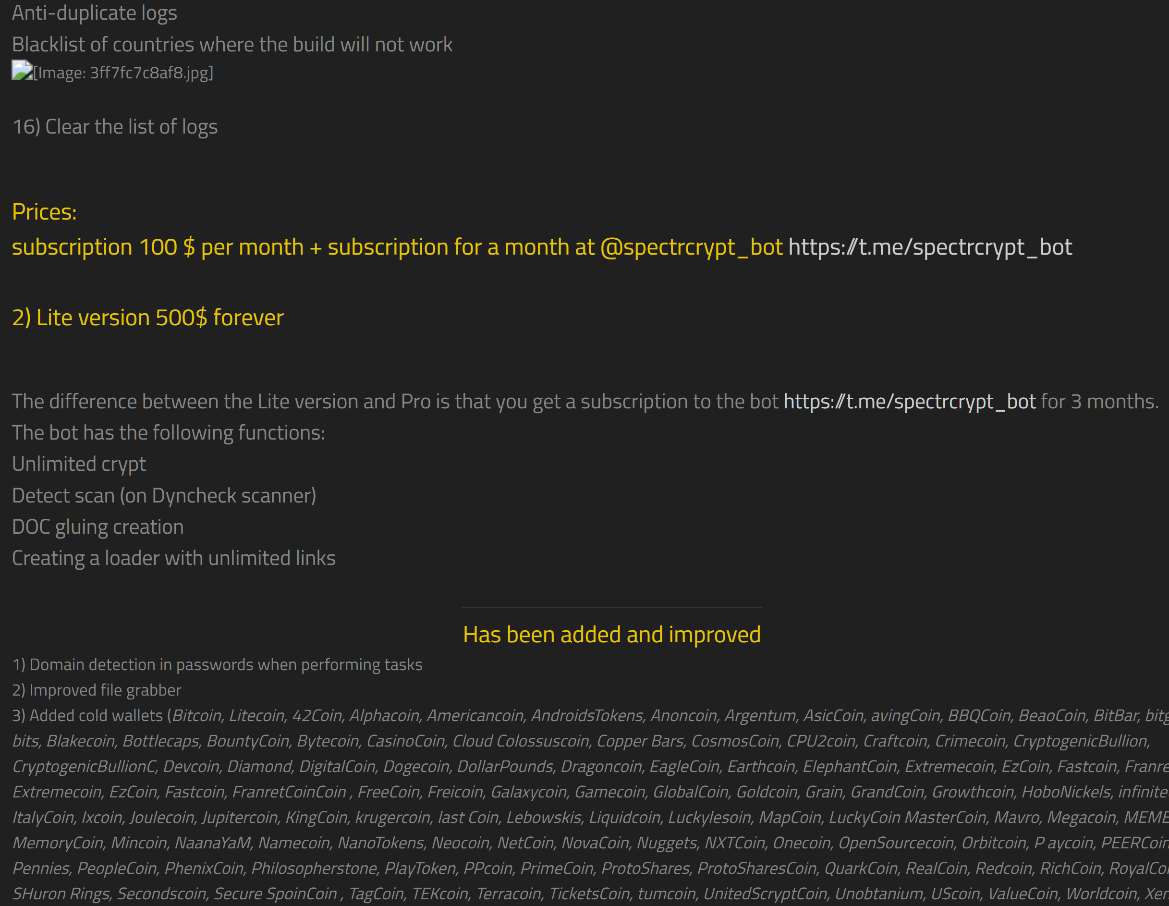
The Redline Stealer has a broad coverage regarding the compromised devices, which belong to different business sectors in Mexico. Due to the obtained visibility in underground forums and black markets, we identified Mexican organizations’ access credentials for sale, which are constantly reported to our clients.
The affected entities exist throughout the nation, as shown in the following screenshot, where access credentials from different states, such as Veracruz, Mexico City, Hidalgo, Sinaloa, Querétaro, and Nuevo León, are used on different sites, from the government, universities, social networks, online banking systems, cloud, entertainment, job boards, pornography, email accounts, and more, are for sale in the black market. The question for the audience would now be: does your organization have a policy to avoid the use of corporate credentials in personal sites?
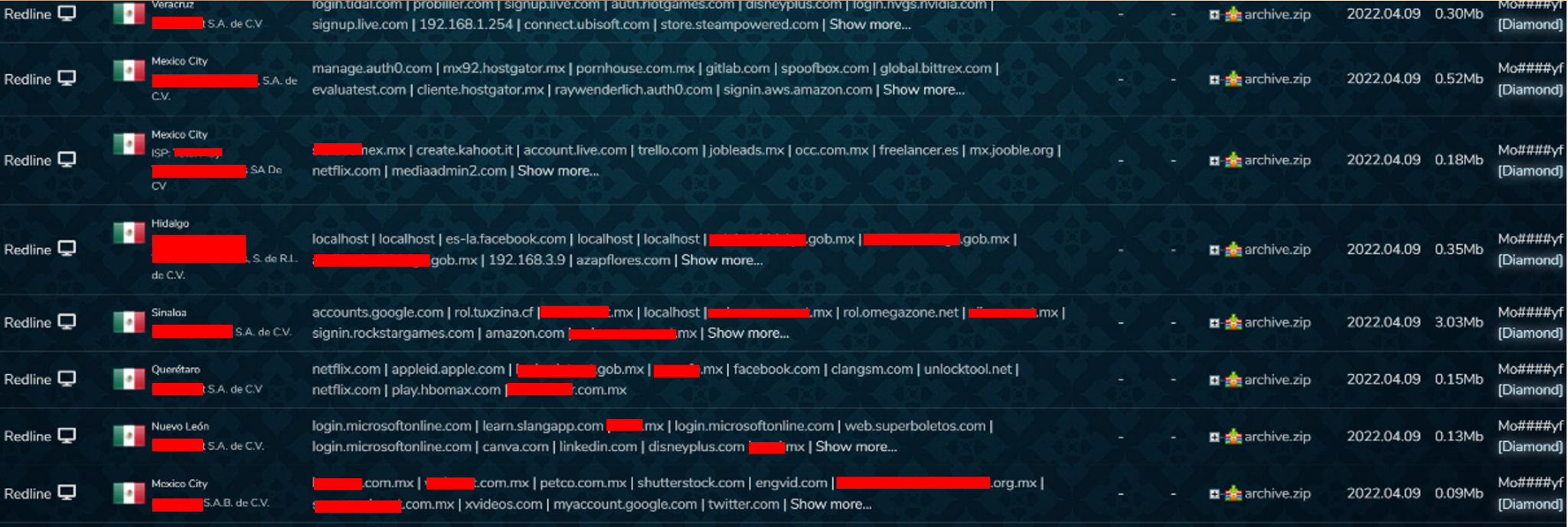
Redline has compromised users in Mexico and, by carefully observing the incidents, we identified that this is part of LAPSUS$ infrastructure. It would be expected for said group to continue its expansion in Mexican territory since the malware has proven to be effective to collect data and providing the capacity to get initial access to an organization through legitimate credentials obtained by the malware.
You can’t monitor what you can’t see. Therefore, as part of our intelligence service, we extract attack and compromise indicators from the pieces of malware in the region which allow our clients to establish a proactive monitoring, detection, and prevention strategy. The following is an example of identification of these types of indicators.
// Deobfuscating Redline Stealer
The sample captured by Ocelot consists of a .exe file with the name StartGame.exe:
When executing it, no visible action can be identified. This behavior can be used to make the user believe that the program has an execution problem while the file has released a series of malicious action in the background.
We identified that the executable has no ASLR protection, so all the referred addresses are always static throughout the execution, at the address 0x5c416c 0x5c416c, we have a routine that copies N bytes from an initial buffer at the address 0x5c416c 0x20000, adding 0x92 to the original value. This simple instruction is in charge of decoding the first shellcode in memory, trying to evade the detection by some antivirus that solely focus on the static analysis of the sample.
Finally, the shellcode is invoked in the memory direction of 0x5c4241 with the instruction jmp 0x20000:
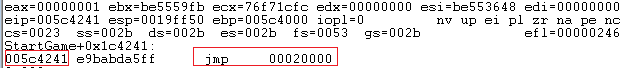
During the execution of the first shellcode, the dynamic loading of some Windows modules not present at loading time is performed, a classic behavior of the malware hiding APIs to be executed:
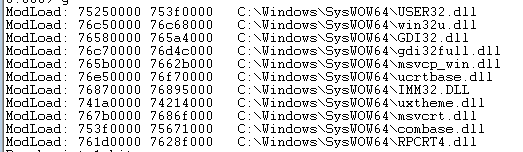
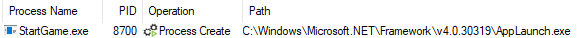
The execution continues until the call to the second shellcode at the address 0x51a68, which is in charge of starting the legitimate .NET program: AppLauch.exe but which will later be injected to load a third shellcode using the classic APIs: VirtualAllocEx, WriteProcessMemory and ResumeThread, for this task.
Within the second shellcode at the 0x1845fe address, we see that memory is reserved in the AppLaunch process.exe via VirtualAllocEx where the last shellcode will be injected, achieving execution of the same via SetThreadContext, who changes the context of the thread to be executed in memory and saves in the EAX register the new entry point of the shellcode, which is finally executed via ResumeThread API, again, known old techniques.
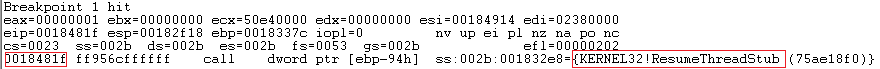
Within the already infected AppLauch.exe process, the malicious behavior continues, and it is, from this process, where the communication with the C2 is done, using the WinSock2 network module from Windows.
We can also observe that it performs the query of system parameters, to profile the victim and create a unique identifier via MachineGuid.
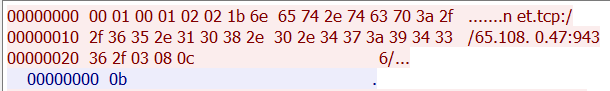
We can see that AppLaunch.exe connects to the IP 65.108.0.47 port 9436, using the .NET Message Framing protocol or MC-NMF, a protocol for bidirectional exchange of SOAP-type messages .
Figure 10 shows the message sent to the server for the start of communication (in red), and the response from the server “0b” (in blue) confirming that Redline Server is ready to exchange information.
The details of the communication of this protocol have already been described above by Blackberry colleagues in:
https://blogs.blackberry.com/en/2021/10/threat-thursday-redline-infostealer-update
There is also official documentation:
Once the third stage shellcode is executed, the known behavior to steal credentials can be observed.
// Motivation / LAPSUS$ Impact
- Source code theft
- Credential theft
- Theft of sensitive data and leaks in public places
- Elimination of critical cloud resources and internal systems
- Manipulation and modification of websites
- Ransom demand to prevent theft of stolen data
// TTPs / LAPSUS$ Capabilities
// LAPSUS$ Infraestructure
- 54.203.159[.]179
- 185.56.83[.]40
- 108.61.173[.]214
- 198.244.205[.]12
- 51.89.208[.]22
- lapsus-group[.]com
The LAPSUS$ arsenal does not only depend on Redline, these are other utilized families
- Mimikatz – SHA256: 9d123f8ca1a24ba215deb9968483d40b5d7a69feee7342562407c42ed4e09cf7
- Quasar RAT – SHA256:065077fa74c211adf9563f00e57b5daf9594e72cea15b1c470d41b756c3b87e1
- Mimikatz – SHA256:2f578cb0d97498b3482876c2f356035e3365e2c492e10513ff4e4159eebc44b8
- Bladabindi/njRAT – SHA256:a0aa66f6639e2b54a908115571c85285598845d3e52888fe27c6b35f6900fe56
- WannaCry – SHA256:a7c3ce181e5c3956bb6b9b92e862b6fea6d6d3be1a38321ebb84428dde127677
/// Conclusion
Derived from the follow-up from the adversary, there is a medium-high degree of confidence that the group continues to operate under the modality of double cyberextorsion. This derives from the method they use to publish the compromised information of their victims since, like Big Game Hunting (ransomware) campaigns, they pressure victims to pay a certain amount of money in BTC and, thus, prevent all the compromised information from being published in cyberspace.
On the other hand, it is observed that this group has achieved significant intrusions coming from the recruitment of insiders’ threats in very large companies, so it is believed that this group has the support of some other cybercrime group. Now the Ocelot Threat Intelligence team is exploring this hypothesis.
Finally, this group’s relationship with other commodity malware campaigns has been observed, such as RedLine Stealer, so it is believed, with a medium-high degree of confidence, that the adversary will continue to acquire capabilities, since they operate under the MaaS model and, it is likely that new samples enabled as LAPSUS$ infrastructure will be observed. The Ocelot Threat Intelligence team is following up on latent and emerging malware campaigns affecting the region to try to identify their relationship with adversaries that we follow.
In Ocelot Threat Intelligence Service we proactively identify threats that are impacting companies in the Latin American region, allowing them to take preventive actions before being exposed by attackers, we achieve this by having undercover agents in private forums of restricted access, which gives us such visibility and, at the same time , we also monitor the brand, the key VIPs of the organization, apocryphal sites, malware campaigns, attribution to identify the actors behind the campaigns to end the problem at its root.
// How does Ocelot Threat Intelligence work?
// OCE-TI-01: Phishing & Suspect Sites
It corresponds to the analysis in various sources in which the Ocelot Threat Intelligence team has visibility trying to identify phishing sites, spam campaigns, banking Trojans and / or ADs purchased by adversaries to place apocryphal sites in the main search engines.
// OCE-TI-02: Metadata
Derived from the identification of documents hosted on our clients’ sites, the Ocelot Threat Intelligence team can identify data within the data in such files, some data could reveal relevant information that could be used by adversaries during their reconnaissance phase.
// OCE-TI-03: Brand Monitoring
It corresponds to the identification of profiles, accounts, usernames, pages and blogs in open and closed sources that use the name and brand of a client without authorization and that promote some product and service to enable some type of fraud or attack vector in cyberspace. This service includes vip monitoring of senior executive positions.
// OCE-TI-04: Data Leaks
It corresponds to the analysis of related sources to collect leaks of information from third parties that publish corporate email accounts, given that they were used to register on external sites which were affected at some point, and, for this reason, the username and password are compromised.
It also includes the identification of public repositories that expose potentially sensitive and confidential information. Finally, it includes the identification of Pastebins-type hosted sites that reveal credentials of users of organizations extracted from some misconfigured system, exposure by mistake or even some intrusion.
// OCE-TI-05: Deep Web & Darknet Monitoring
It corresponds to the analysis of closed sources such as; underground forums, cybercrime forums and black markets, in which adversaries and people who are dedicated to illicit activities publish and market information from various organizations, the Ocelot Threat Intelligence team has the ability to perform infiltration tasks in these sources and proactively identify each time relevant data is published.
// OCE-TI-06: Malware
Analysis and monitoring of malware campaigns that could be related to the infrastructure of one of our clients, as well as malicious artifacts that use the name of a client to deliver known or targeted malware as part of a local campaign, or even that infects legitimate software of the company for economic purposes. A detailed writeup of the malware is delivered with their respective attack indicators (IOAs) and indicators of compromise (IOCs) that serve our customers to take proactive measures.
// OCE-TI-07: Relevant Adversaries
It corresponds to the monitoring of the adversaries of the region and, which are relevant to the different sectors in which our clients participate, the Ocelot Threat Intelligence team works on the constant profiling of the top of adversaries to provide the detail of their TTPs (Techniques, Tactics and Procedures).
This linked to the APT Simulation service, we can replicate new techniques in the network of our customers through the creation of malware in our laboratory for the measurement and immediate strengthening of security controls in processes, people, and technology.
Do you want to evaluate how your Blue Team would response to a Redline infection in your organization? Contact us!
// OCE-TI-08: VIP Monitoring
It corresponds to the analysis in various sources in which the Ocelot Threat Intelligence team has visibility trying to identify personal information both information that should not be public and that information generated by the online activity of the entity.
// OCE TI-09 Tracking BINs in Cyberspace
Goal
The objective of the OCE-TI mentioned is to provide visibility of the BIN (Bank Identification Number) of the products (Cards) of different financial institutions, filtered in different sites of the superficial, deep web and even in the Darknet.
// Background
Since the jargon of cybercrime dedicated to Carding (illegally generating, obtaining, managing, marketing and using information and bank card numbers) changes constantly, to prevent Threat Intelligence services from profiling them, searches by syntax have to be constantly being redesigned. However, BINs remain a research method in which the financial institution behind a product can be identified. That is why this OCE-TI is added as a service to the catalog having its research methods, techniques, and sub-techniques
// OCE-TI-10: On-demand interaction
With our undercover agents, we interact directly with actors at the request of our clients to extract first-hand information that allows them to make decisions proactively.