Is Your Cybersecurity Working As You Think It Should?
Optimize existing cybersecurity technology investments, verify coverage, and gain central management and execution speed

Companies have purchased a multitude of cybersecurity technologies
It is very difficult to verify that they are properly deployed with complete coverage
Batuta Adds Clarity and Controls
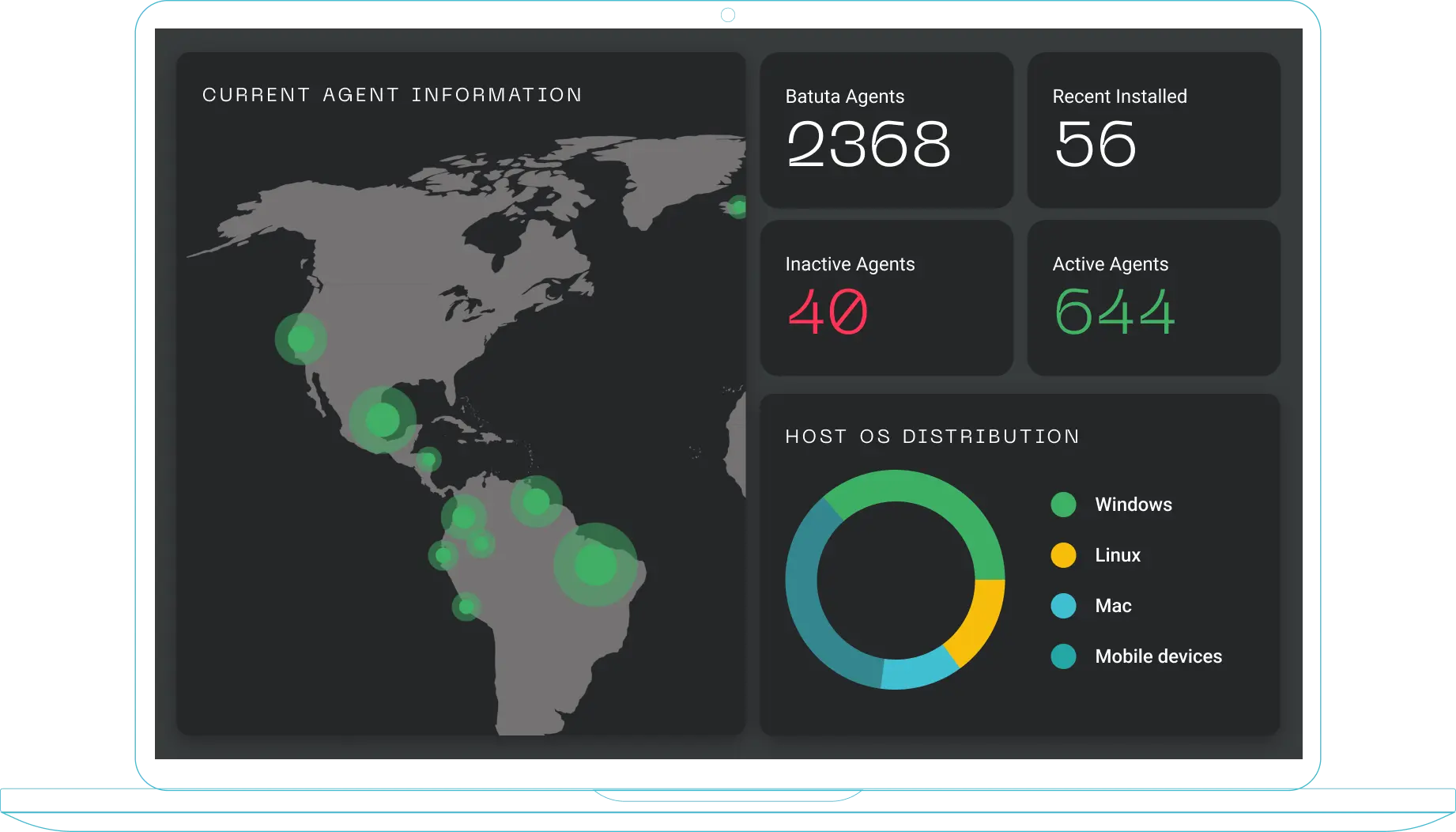
Batuta centralizes the management and control of your IT infrastructure and cybersecurity technologies and enables end-to-end cybersecurity visibility through API integrations, giving your company complete certainty that the technologies you've purchased are working as they should
The Batuta Advantage
Batuta utilizes a lightweight websocket agent that runs on user-level permissions without installation dependencies. The websocket connects to a central console via SSL tunnel and is capable of executing commands and scripts orchestrated from there. Unlike an EDR, it does not make behavior or signature-based decisions.
Perform rapid, scalable endpoint management across the entire lifecycle - from a single unified platform.
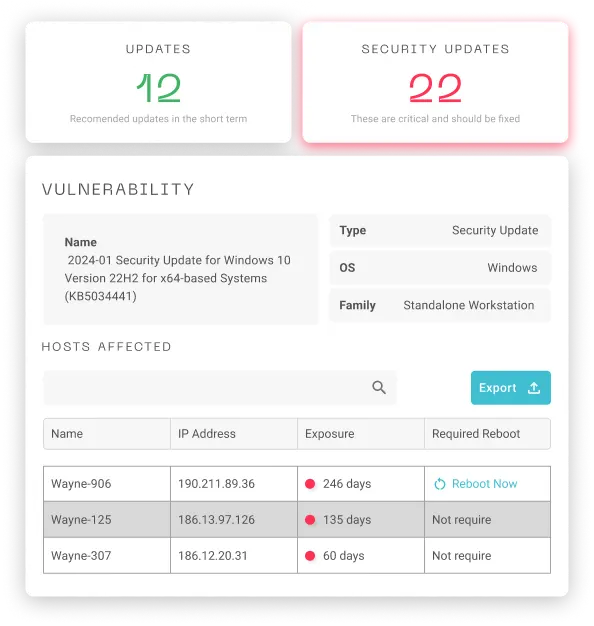
System patching and updating is one of the factors that improve a company's security posture, but it falls somewhere between IT and cybersecurity. Batuta bridges the gap and enables greater collaboration with dual functions for both teams.
Cybersecurity + IT
Batuta runs every Cybersecurity + IT workflows that relies on endpoint data
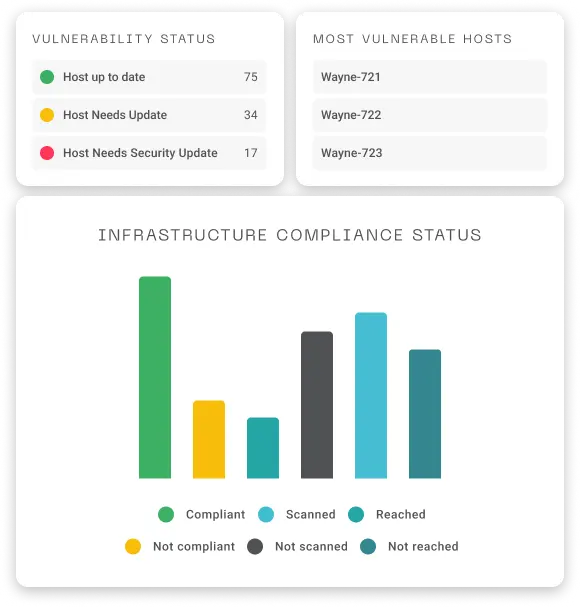
Compliance Across Fleet
The Batuta Modules
See how we've helped simplify processes, optimize systems and transform businesses and cybersecurity programs around the world
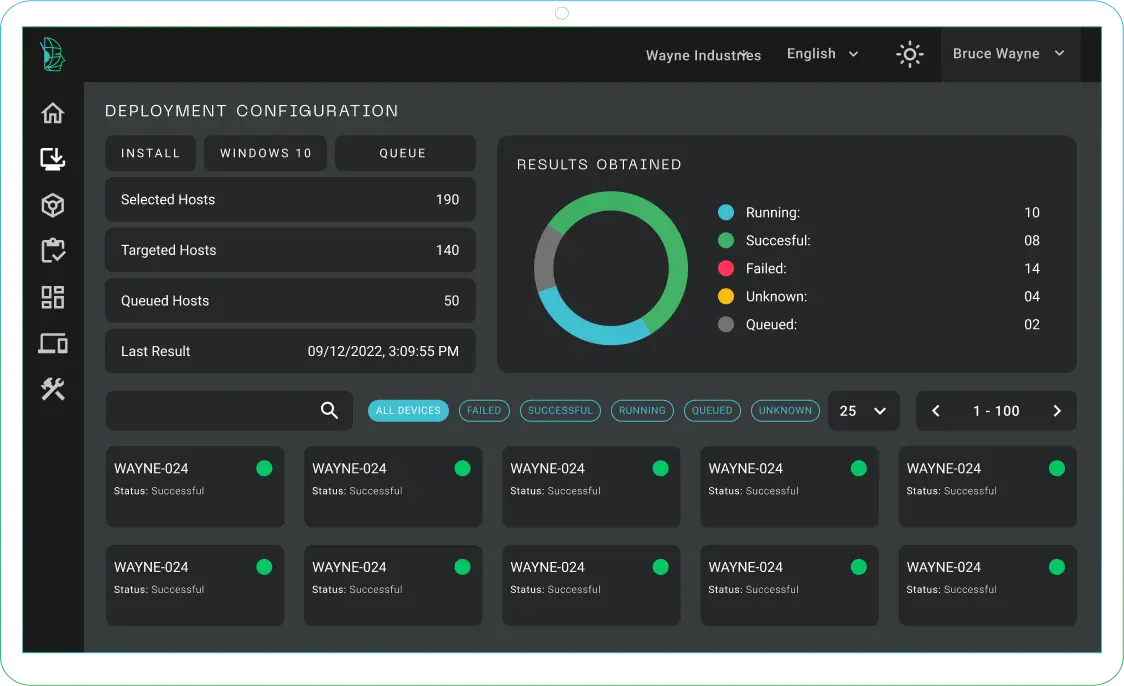
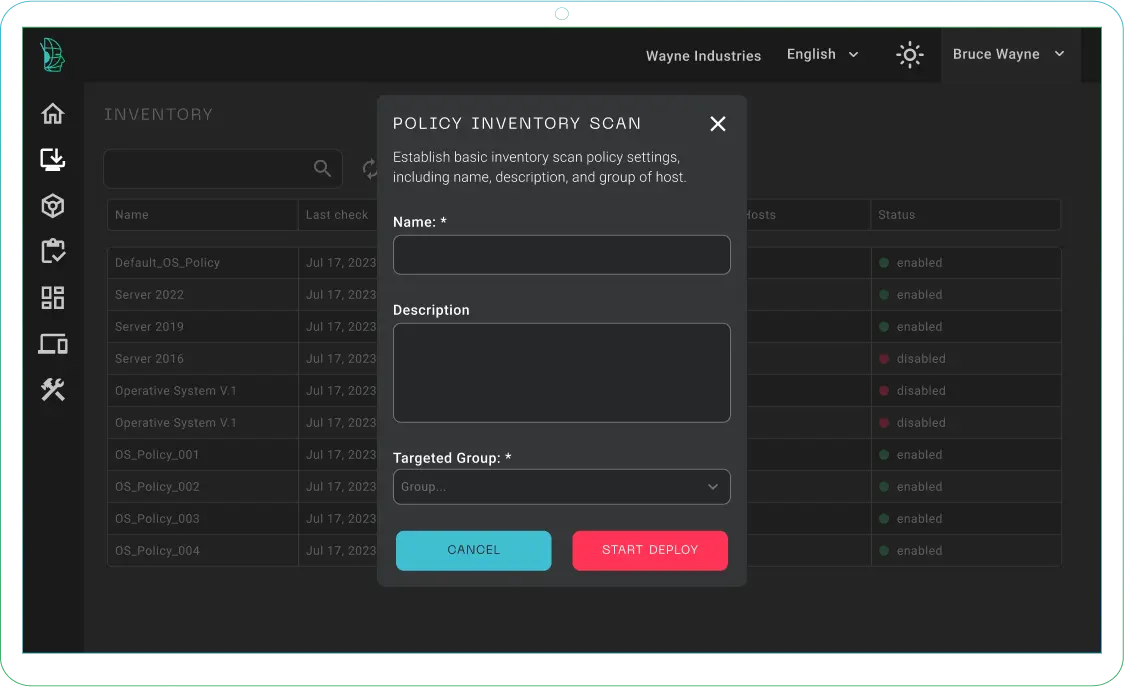
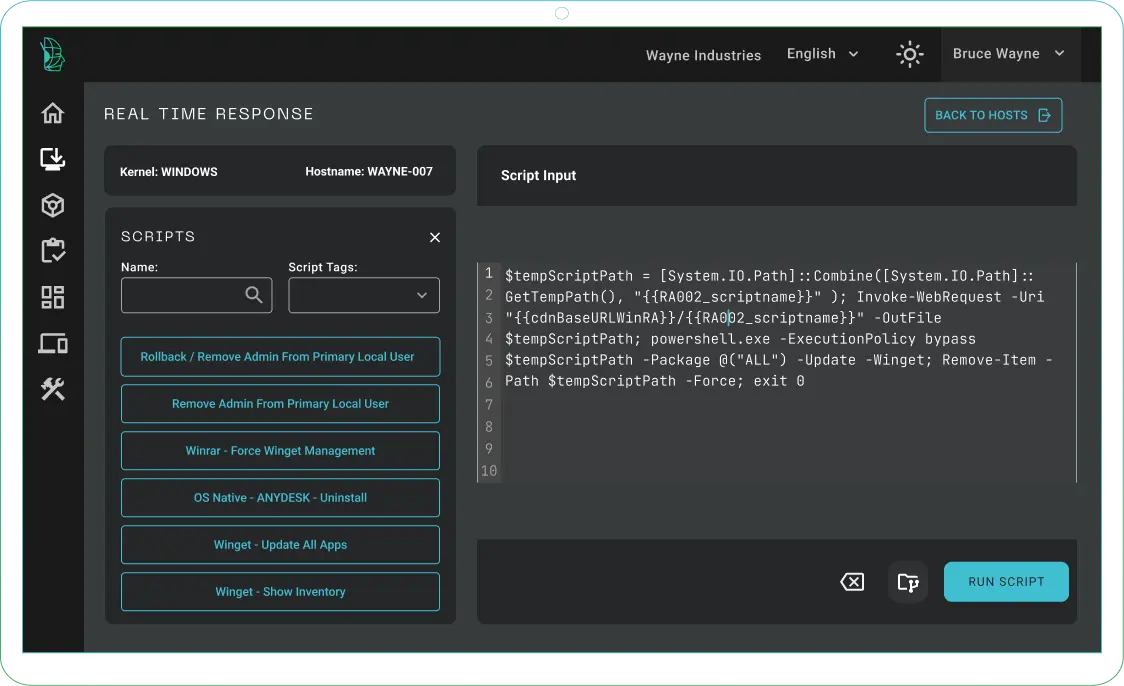
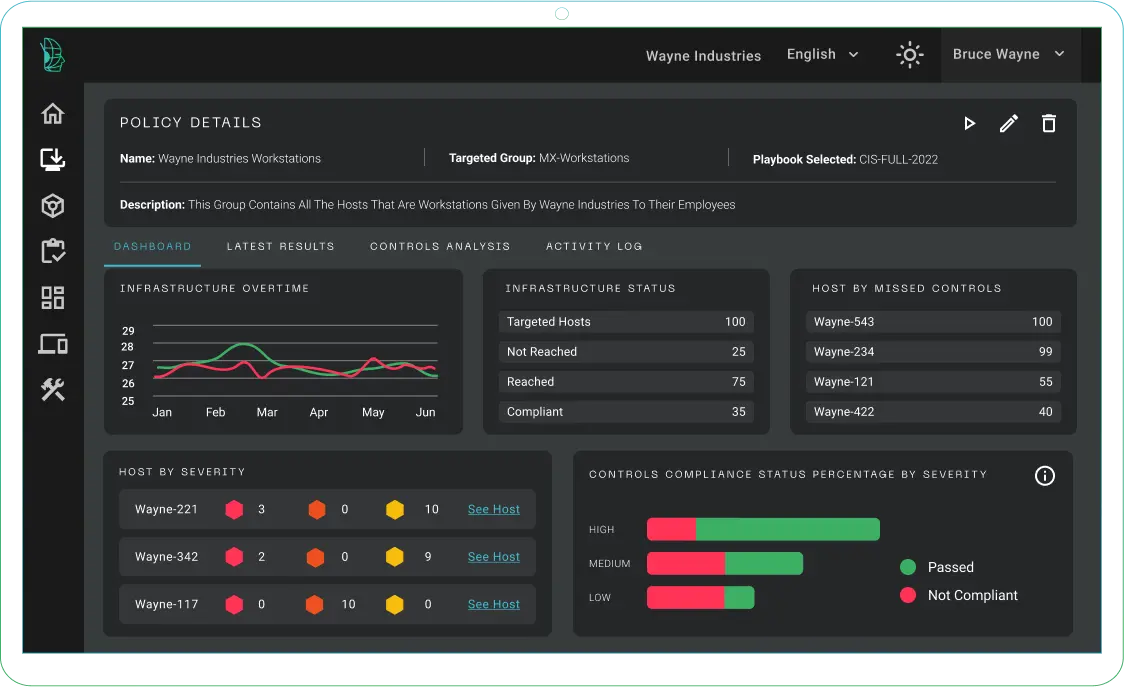
- Swift installations for accelerated cybersecurity operations
- Intuitive uninstallation process for effortless system maintenance
- Real-time status checks for reliable implementation
- Comprehensive hardware and software inventory for full visibility.
- Efficient asset tracking and management for organized operations.
- Powerful insights for informed decision-making.
- Scripts automate routine and critical tasks like software updates and security patches across all endpoints.
- Operational efficiency is boosted by reducing manual effort and streamlining processes.
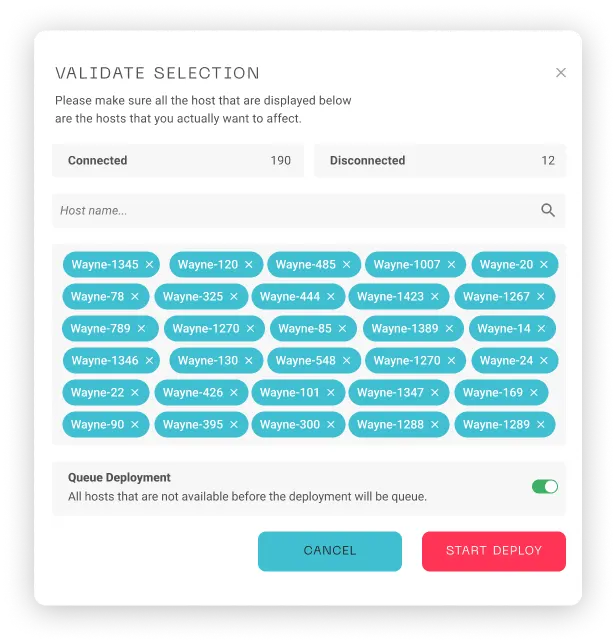
- Simultaneous execution speeds up deployment and remediation across your fleet.
- Real-time monitoring identifies and corrects deviations.
- Enforces high standards and reduces vulnerabilities.
- Tailored policies that evolve with security needs.

- Swift installations for accelerated cybersecurity operations
- Intuitive uninstallation process for effortless system maintenance
- Real-time status checks for reliable implementation

- Comprehensive hardware and software inventory for full visibility.
- Efficient asset tracking and management for organized operations.
- Powerful insights for informed decision-making.

- Scripts automate routine and critical tasks like software updates and security patches across all endpoints.
- Operational efficiency is boosted by reducing manual effort and streamlining processes.
- Simultaneous execution speeds up deployment and remediation across your fleet.

- Real-time monitoring identifies and corrects deviations.
- Enforces high standards and reduces vulnerabilities.
- Tailored policies that evolve with security needs.
We Give you The Power of Control
See how we've helped simplify processes, optimize systems and transform businesses and cybersecurity programs around the world.
-
Swift installations and intuitive uninstallations
-
Effortless maintenance
-
Real-time status checks
-
Efficient asset tracking and management
-
Rapid threat containment and mitigation
-
Threat prevention based on incident insights
-
Stakeholder trust reinforcement through transparency
Start Your Path to Proactively Reduce Risk Now
-
No Extra Management Overhead
-
Fast Time to Value
-
No Changes Required to Existing Infrastructure
-
Deploys in Minutes