Orchestrate your security posture through endpoint intelligence.
Batuta delivers unparalleled visibility through our lightweight agent, which provides real-time, reliable data directly from your endpoints—the foundation of true endpoint intelligence.
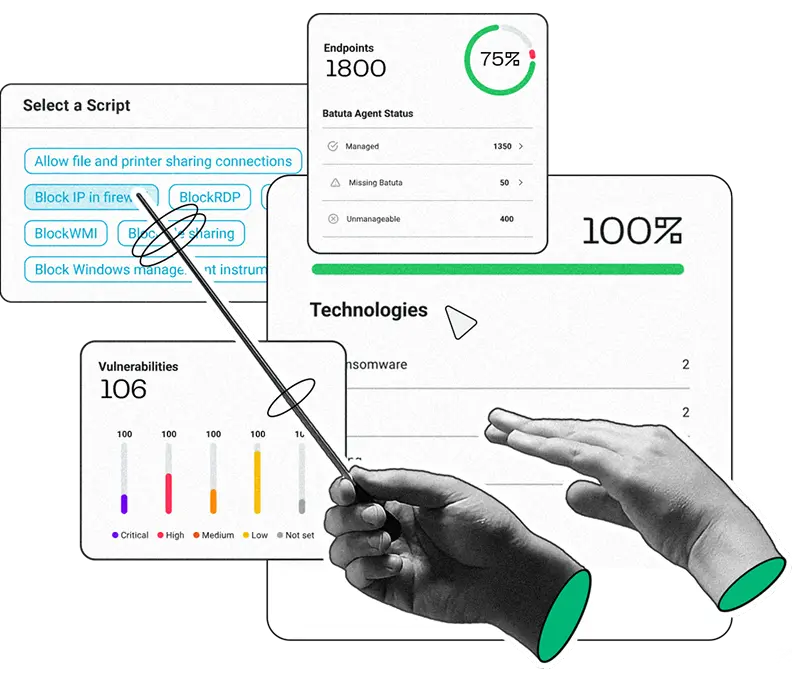
Your endpoints are the critical attack vector
Trusted by security teams to solve complex endpoint challenges
Get a Demo“Batuta is easy to use, easy to understand. It is rapid to implement and delivers quick wins.”
Reduced mean time to respond and recover from a ransomware attack.
“I often speak with CISOs about visibility gaps, supply chain, data overload, and tool sprawl. Batuta addresses these issues with proactive insights and efficient tool management.”
“Despite increased security spending, fundamentals are missing. Batuta offers visibility, control, and end-to-end cybersecurity certainty.”
Reduction in security and technology risk.
“Nowadays, it is one of the most used technologies in our organization for both monitoring and execution.”
An Endpoint Security Posture Management Platform



 Workstations
Workstations
 Servers
Servers
 Virtual Machines
Virtual Machines
Take the first step toward orchestrated endpoint intelligence.
Discover how Batuta simplifies endpoint protection, empowers your team with real-time insights, and strengthens your security posture through intelligent, data-driven decisions.
Rapid install/uninstall of endpoint software
Effortless maintenance
Real-time status checks
Efficient asset tracking and management
Rapid threat containment and mitigation
Stakeholder trust reinforcement through transparency





