
Car Hacking: Current Trend in Car Theft
December, 5, 2022
12 minutes read
Salvador Mendoza from Metebase Q’s R&D Team
Car Hacking: Current Trend in Car Theft
// Keyless entry system risks. Vol 1
// Research Summary
With inexpensive hardware and Software Defined Radio (SDR) open-source tools, malicious individuals can compromise vehicles’ security entry systems by exploiting their keyless system weaknesses. Most automobiles around the world rely on rolling code cryptographic algorithms to protect their entry systems. When a car owner presses the key fob to unlock button, a malicious user can intercept the signals and save them for future use. These intercepted instructions might be implemented to deceive the car owners and get access to their cars. The risk of these attacks is increasing enormously due to the easiness of accessing SDR hardware tools and inappropriate security implementations.
// Introduction
Whether it’s autonomous vehicles, increased connectivity, or electrified vehicles, technological innovation is now driven by software, which engenders inherent cyber risk. Most people are aware that many dangers are lurking on the Internet: a hacking attack on the company network or the private computer is possible at any time. But very few know that hackers could also be targeting cars – the more electronics they contain and the more networked they are, the greater the risk.
Cybersecurity is a very real concern that all automakers, suppliers, and users deal with daily. This is why Metabase Q is sharing this information.
Over the past years, there has been an increase of many different attacks against automobile access systems ––they go beyond someone popping the lock and stealing the stereo– where malicious actors are being capable of stealing cars in without having to force their entry.
How is it possible? How can someone steal a vehicle without having the owner’s original key fob and without forcing the car? Networking makes cars vulnerable, and the more they are digitally upgraded and connected to networks, there is a bigger opportunity for hackers to launch an attack. To understand their techniques, it is necessary to analyze the access controls car systems and how the attackers might bypass these security features.
By 2023, connected vehicles are expected to account for a quarter of all passenger cars worldwide . And connected vehicles will comprise nearly 86% of the global automotive market by 2025 , thereby the rising number of connected vehicles, coupled with vehicle-to-everything technologies (V2X), have increased vulnerabilities and entry points for hackers to leverage.
It is important to understand the threat landscape. Cybercrime, including automotive-related cybercrime, is more profitable than the global illegal drug trade, at $600 billion annually versus $400 billion . While COVID-19 slowed down many industries’ operations, cyberattacks were on the rise, being transportation one of the five most-targeted industries .
According to a USWITHC study, cyberattacks on connected cars have gone up by 99% since 2018. In the United Kingdom, in 2019 alone, 92% of car thefts were carried out with no keys. Then, in April 2020, two researchers hacked into a Ford Focus using an OBD-II connector and laptop, allowing them to control the brakes, change the car’s speed, access the infotainment system, and more. Attack vectors are how hackers gain access; a single incident can include multiple attack vectors. Upstream Security found that the three most common attack vectors were: 1) servers, 2) keyless entry systems, and 3) mobile apps. (Figure 1)
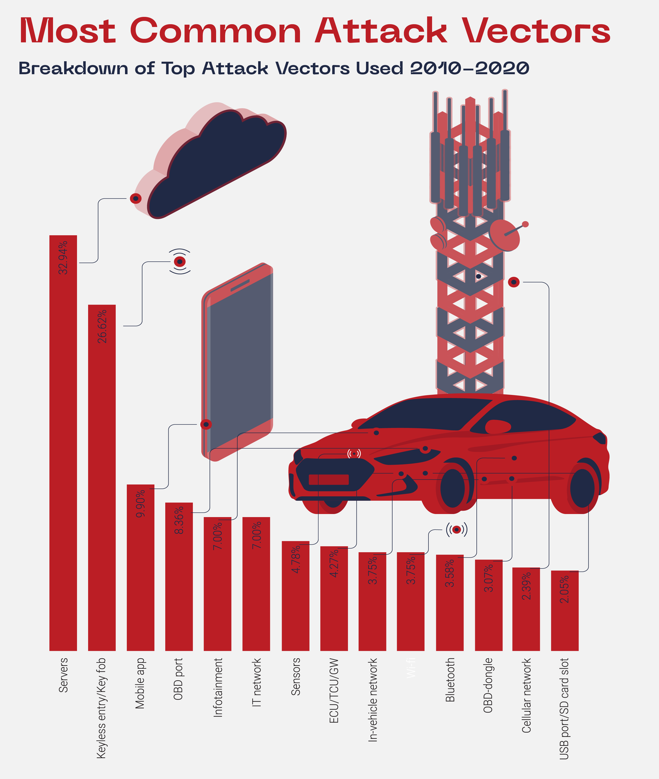
In this blog, we will focus on keyless theft (sometimes called relay attack) which is a way of stealing a vehicle without using the physical keyfob. The targeted vehicles are those with keyless entry and start systems, exploiting the technology to get into the car and drive it away. Several vulnerabilities in keyless entry systems were discovered in 2020 that enabled hackers to easily open locked vehicle doors.
In March 2020, researchers discovered that the remote keyless system on Honda’s HR-V 2017 sends the same RF signal for each door-open request . Then, in July 2020, a researcher found a vulnerability in Tesla Model 3’s NFC tag, allowing him to perform a relay attack by leveraging the signal of a legitimate NFC tag associated with the vehicle to open the door .
Unfortunately, keyless entry attacks are carried out by more than just researchers and white-hat hackers. In July 2020, a tech firm from Bulgaria sold devices resembling the old Nintendo Game Boys for £20,0004, these devices were used to unlock car doors by recording wireless key signals and acting as a responder that the car recognizes as an authorized remote . Remote attacks have consistently outnumbered physical attacks since 2010, accounting for 79.6% of all attacks between 2010 and 2020.
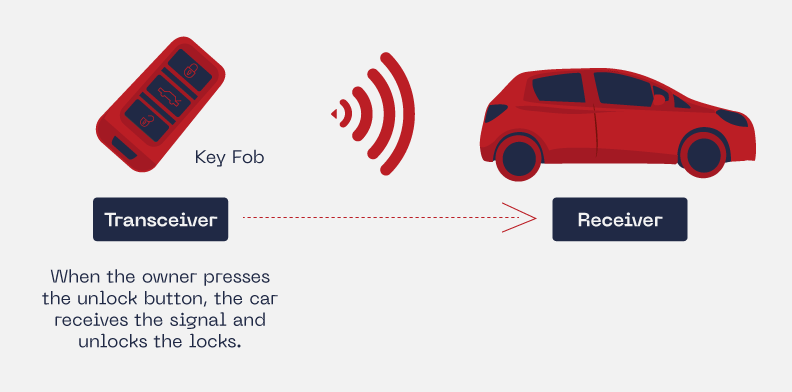
There are two different keyless systems: Active Keyless Entry System and Passive Keyless Entry & Start (PKES). For now, we will analyze the active keyless entry system (Figure 2), how it works and how malicious individuals take advantage of the weaknesses in this technology. In this blog, we will focus on the active keyless entry system implementing rolling code technology. Normally, an active keyless entry system will transmit a signal to indicate a specific command: unlock, lock, or open the trunk. But how is this signal transmitted and how could it be reused?

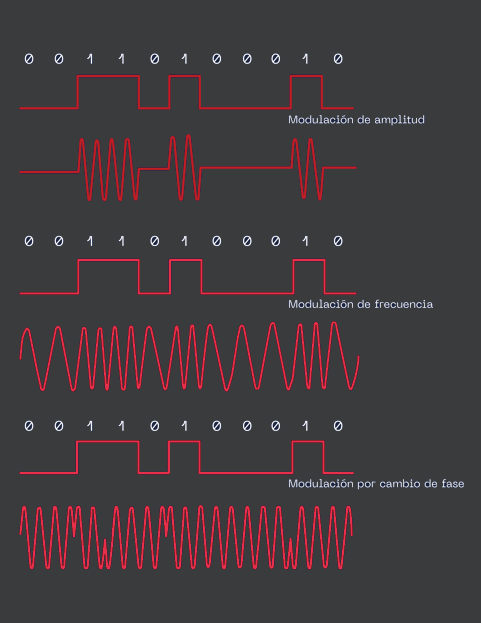
Usually, key fobs implement Frequency Shift Keying (FSK), Amplitude Shift Keying (ASK), or On-Off Keying (OOK) modulation techniques. Using a specific modulation will depend on the brand hardware specifications. But the most important factor between signals is how they encode the information being Manchester or bi-phasing the common scenario across the modulation’s world. The wave interpretation is crucial to understand how the information is traveling and the best way to decode it correctly. It will be extremely necessary to know the specific wave modulation to obtain the correct instruction for the key fob afterward.
// What is rolling code technology?
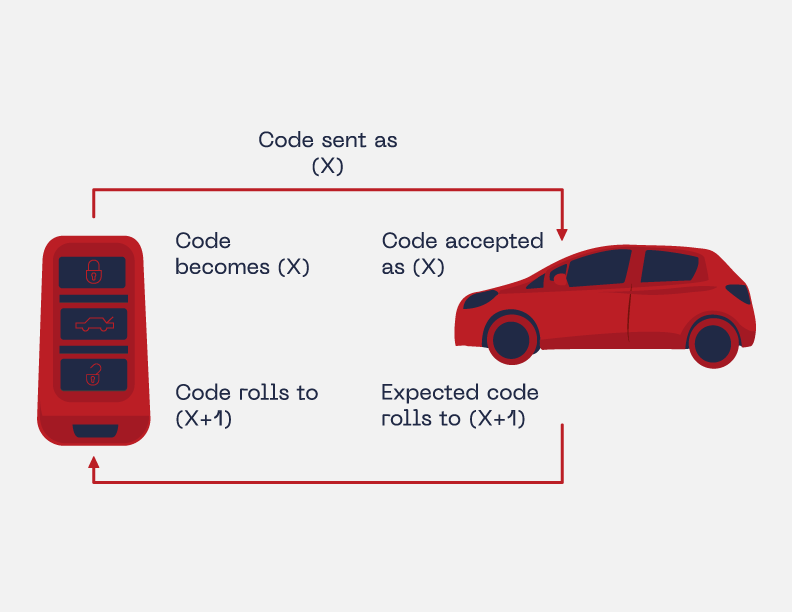
The rolling code cryptographic algorithm is widely implemented in different technologies such as garage door openers and car remote controls. The main function of the rolling code, also known as hopping code, is to offer special protection against replay attacks. This type of attack is a form of saving a valid signal transmission using special hardware and retransmitting it. Adding that retransmission might take place in a different location but behave like the original signal or instruction.
To protect against replay attacks, the rolling code implements different features:
Pseudorandom number generator (PRNG) or deterministic random bit generator (DRBG) generates consecutive random numbers using a special seed as an initial value. Meaning that every time a car owner presses the unlock remote control button, a new greater random number will be generated. By using this incremental random generation feature, the rolling code assures that if a malicious individual saved a previous signal transmission, the next generated number will be different and will avoid a possible replay attack using that previously saved signal, at least in theory.
// Active keyless entry systems
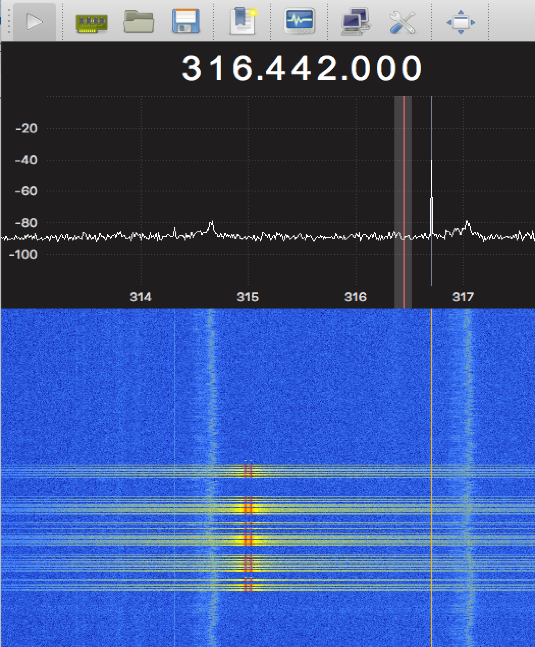
Active keyless entry systems are characterized by an active remote-control mechanism. Meaning that the owner must press the unlock key fob button to open the lock door system. The active key fob uses only one transmitter to establish the communication. The rolling coded signal travels in Ultra High Frequency (UHF). Normally, at 315MHz. The adequate distance to communicate properly between the key fob and the car may vary, depending on the key fob battery power; but it might work between 0 to 80 meters.
After the car’s system authenticates the key fob signal and the car is unlocked, the owner must insert the physical key in the ignition system to start the vehicle.
// Bypassing the rolling code technology
Some malicious individuals prefer rather than forcing the car entry system, to implement new technologies to enter the automobile; some of them prefer to steal valuable personal belongings from the automobile, and others decide to steal the car. In the old fashion way, they normally break the window glass, but with new technologies, instead of making noise, the new attackers prefer to do it quieter.
To bypass the rolling code technology, the malicious users must implement special hardware and software, normally known as Software Defined Radio
To understand the process of a successful attack against the rolling code technique, we must understand the normal process to unlock the automobile from the owner perspective:
- The owner presses the unlock button from the remote key fob device
- The car receives the signal and checks if the instruction is in range of the consecutive rolling code algorithm
- If it is, the system unlocks the car
At the unlock process, the car will interpret the signal and make some decisions internally without communicating anything to the key fob.
If the car is not within the key fob range, when the unlock button is pressed, that rolling code instruction is discarded and will not be used in the next interaction. When the user presses the unlock button again, a new rolling code is generated (the new code will be greater than the previous one). The car implements a verification list that corroborates if the transmitted rolling code is in a continuous range.
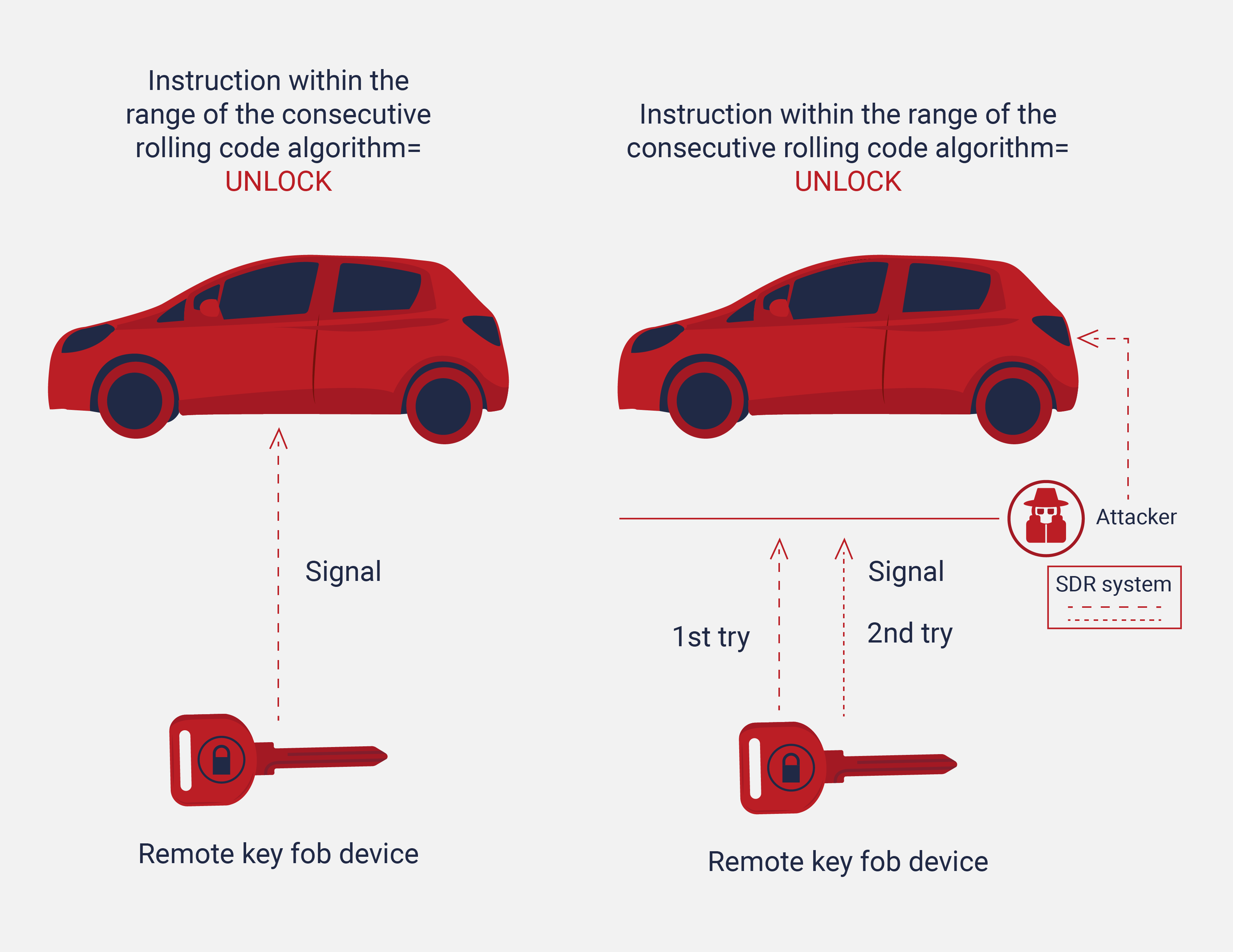
The approaching steps to be successful in this attack scenario might vary. But in general circumstances, a malicious user follows this procedure:
- The car owner presses the unlock button from the remote key fob device
- The attacker jams the communication between the car and the key fob but also intercepts the rolling code signal
- The owner presses the unlock button again thinking that the car did not receive the signal properly on the first try. At this point, the attacker continues jamming the communication but simultaneously intercepts the new instruction again
- With the new two fresh rolling code signals, the attacker released the first captured signal to unlock the car. The owner believes that the car was unlocked because he/she pressed the key fob button. But the reality is that the attacker deceives the owner by releasing the first saved signal that unlocked the car system
- At this point, the attackers have the last transmission in their SDR systems to be used to unlock the car in the future. Even after the owner locked the car properly
- The malicious users can use the last captured signal only if the car does not receive any new unlock rolling code signal from the key fob
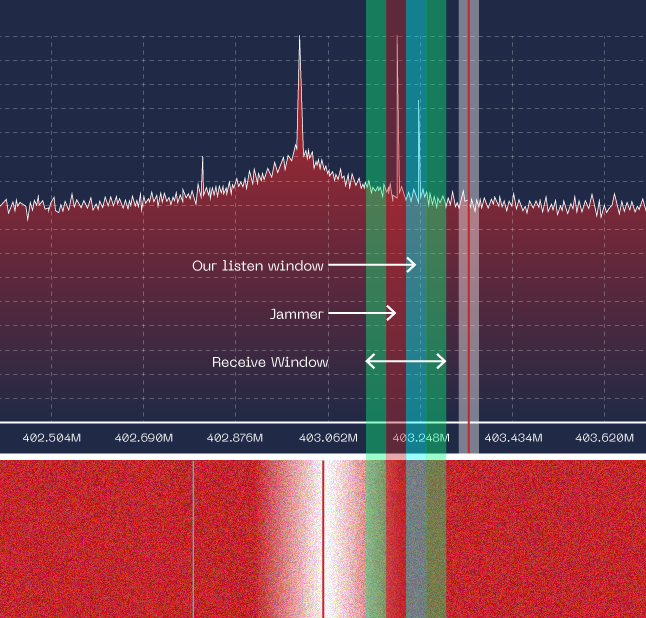
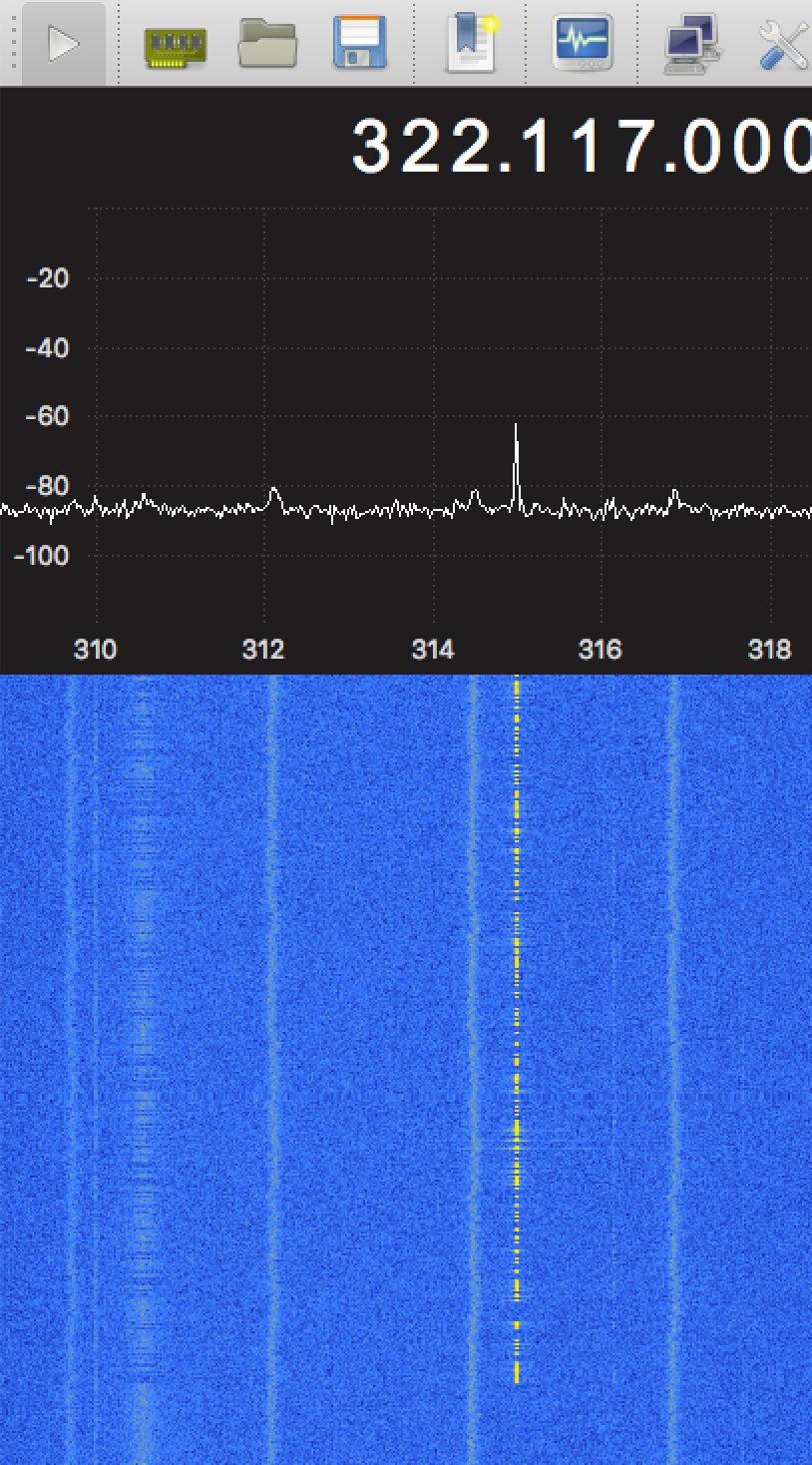
//Intercepting the signals and replay them
The malicious users must have two different SDR systems or radio technologies to achieve the rolling code attack: one to intercept the signal and the second to jam the communication between the car and the key fob.

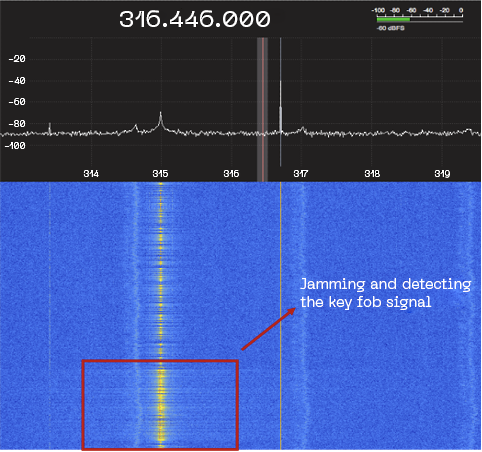
When the system starts the jam process, this motion can be detected in the waterfall radio frequency spectrum. The jam process consists in sending noise into a specific car receiver frequency to avoid proper communication with the key fob. It must be slightly above or under the normal frequency but will be enough to accomplish the jam task.
While the jamming is taking place, the second antenna is waiting to intercept the key fob signal to save it.
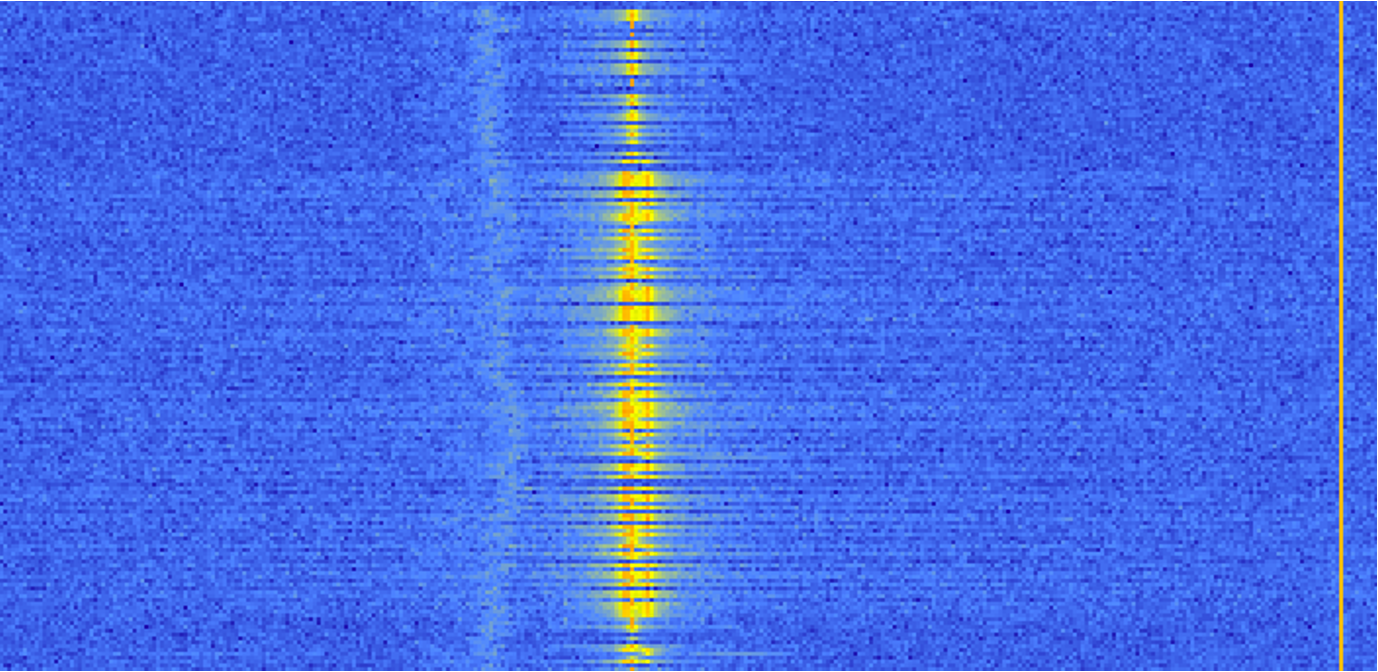
If we zoom in, we can notice both signals traveling almost together but slightly in different frequencies. The malicious individuals must narrow the signals from the key fob to avoid the noise from the jammer. The main point is to obtain the instruction from the key fob without getting garbage from the jammer signal:
// The roll jam attack
When malicious individuals obtain two consecutive instructions to unlock the car, they will be prepared to deceive the owner with these signals. Using an automatic system to send the first captured signal and keep the second rolling code to be used after the owner park and lock the car.
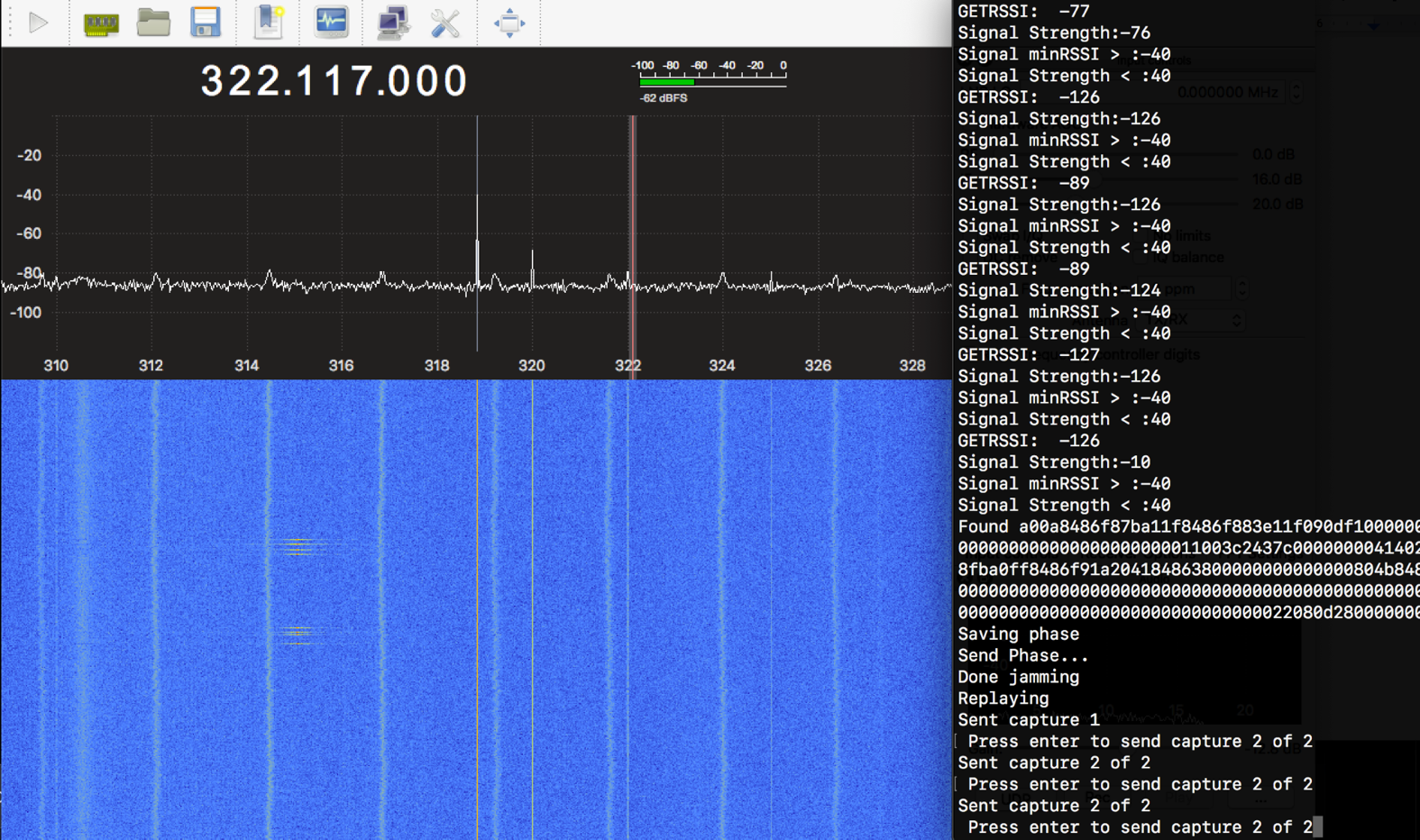
It is important to mention that this complete process occurs automatically. Implementing a programmed device that will do all the tasks underground. The main malicious goal is to make this process behave naturally. So, the car owner does not notice that was deceived by a rolling code jam attack.
In the next video, you can watch a POC of the modus operandi that has been detailed throughout the research document.
// Recommendations
To have better protection against rolling code and jamming attacks, companies should perform better methods of authentication by implementing different carrier frequencies, such as 4FSK or Frequency-hopping spread spectrum (FHSS). The main purpose is to transmit radio signals through many different frequencies occupying more sections of the radio spectrum. Decreasing the possibilities of signal interference by design. Making it necessary to establish a communication between both entities to interchange the authentication process must be a priority.
Adding that a combination of low and high frequencies hardware should improve dramatically the protection against jamming attacks. Also, adding mechanisms such as hashing or encryption in the key fob press command will decrease dramatically the replay or eavesdropping signals as well.
In the owner’s perspective, they must protect not only their physical key fob but its signal as well. Make sure that the key fob is working properly locking and unlocking the car on repeated occasions to corroborate that is working in a single try.





