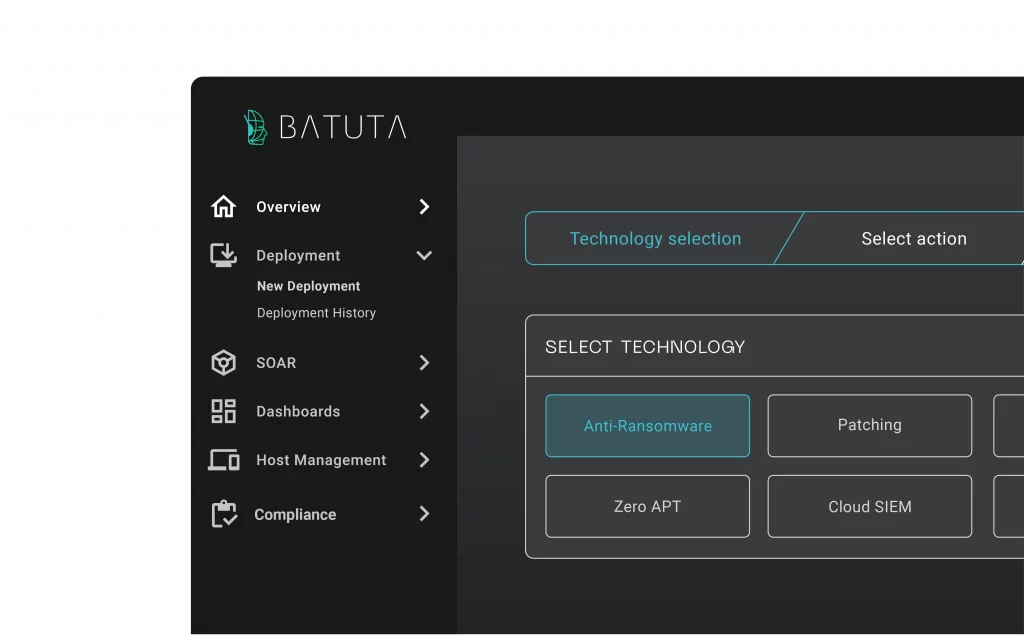
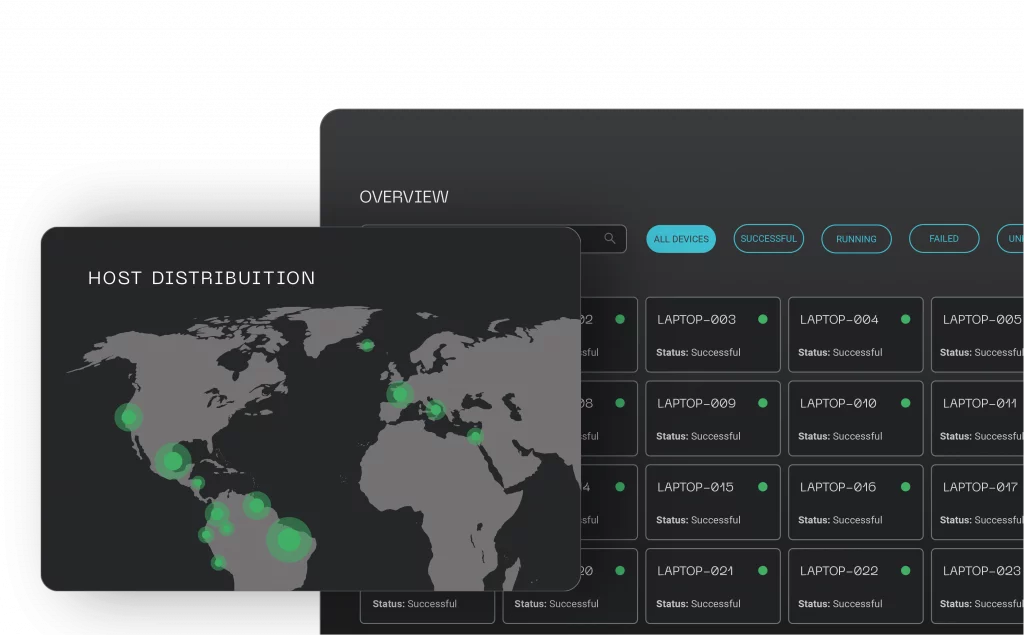
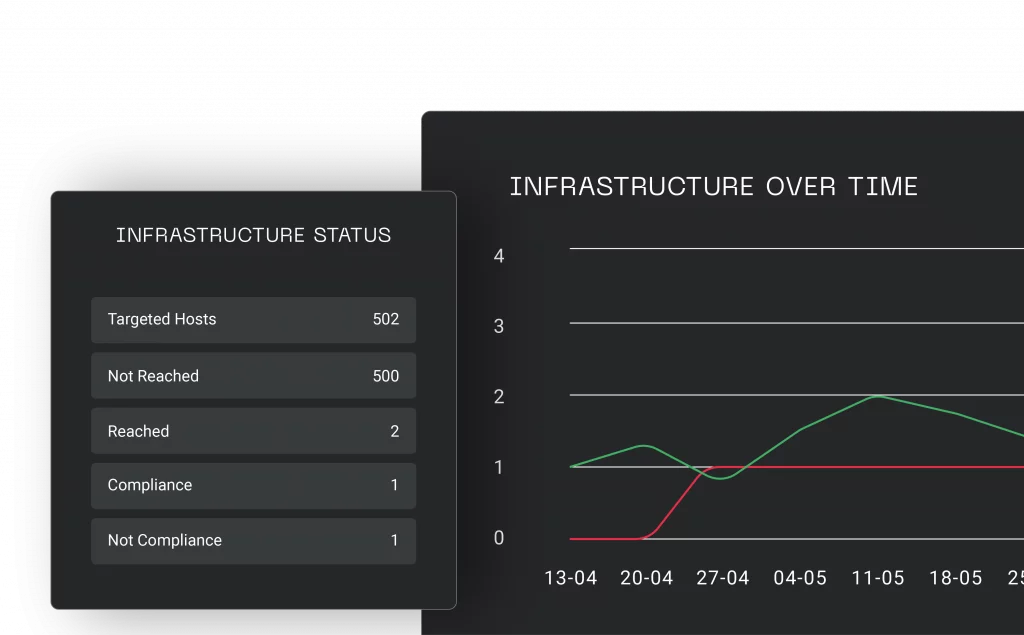
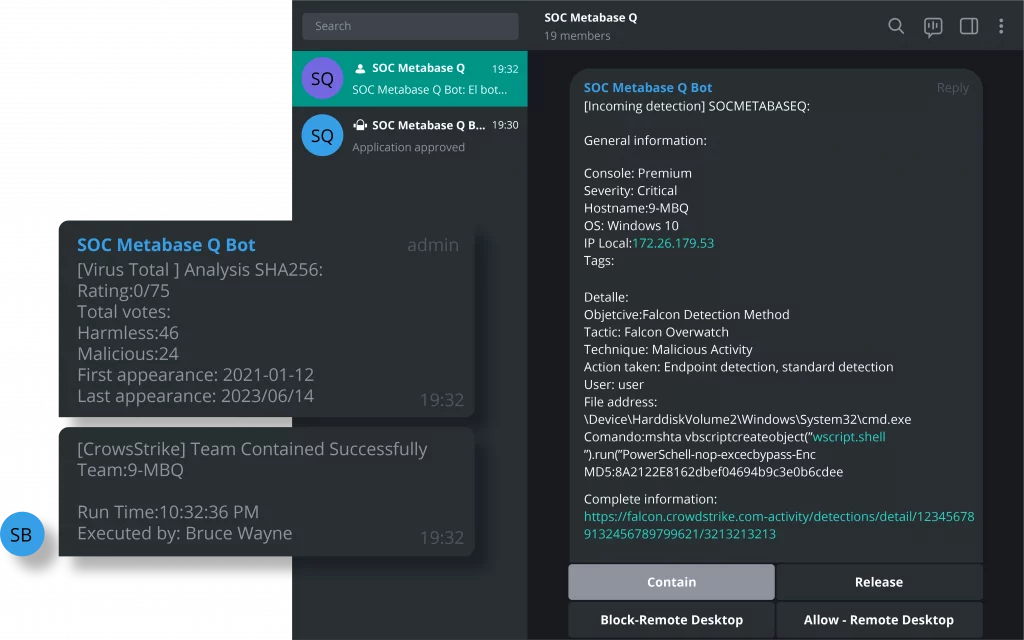
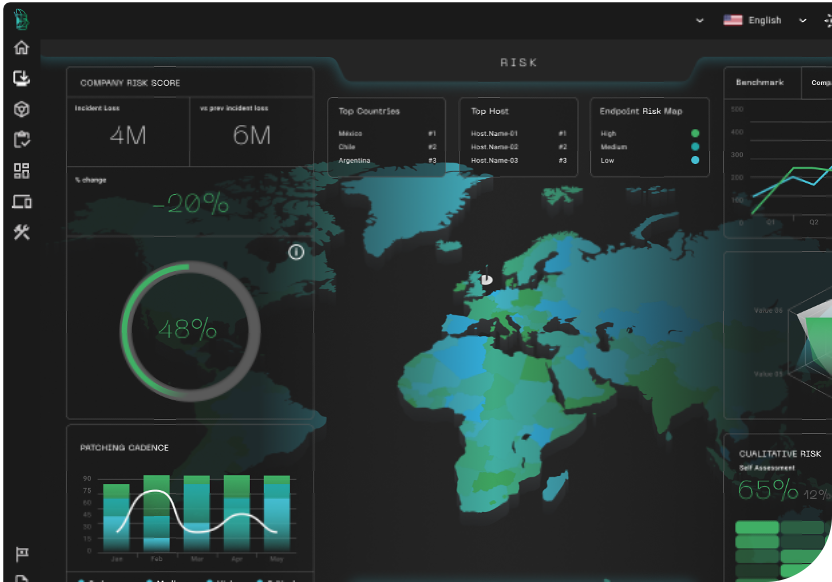
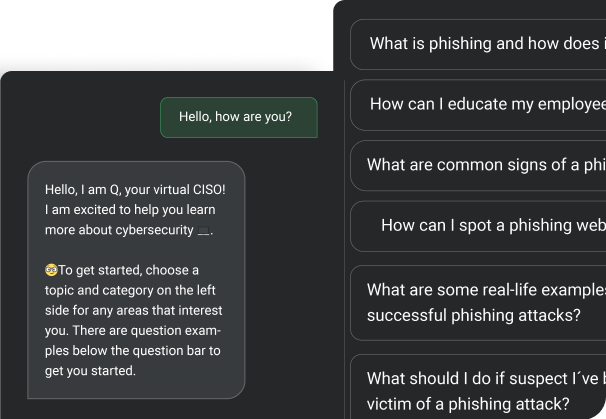
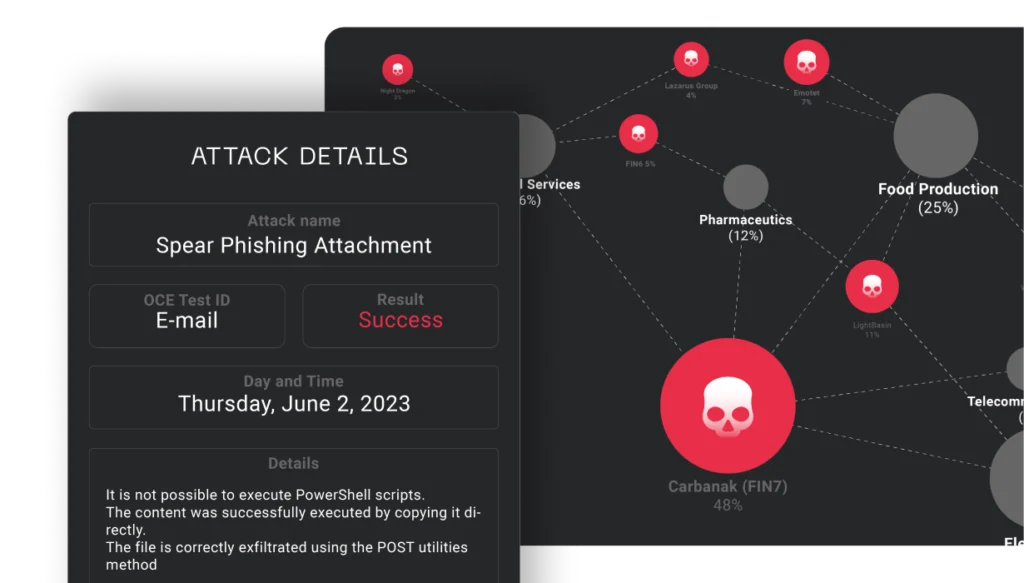
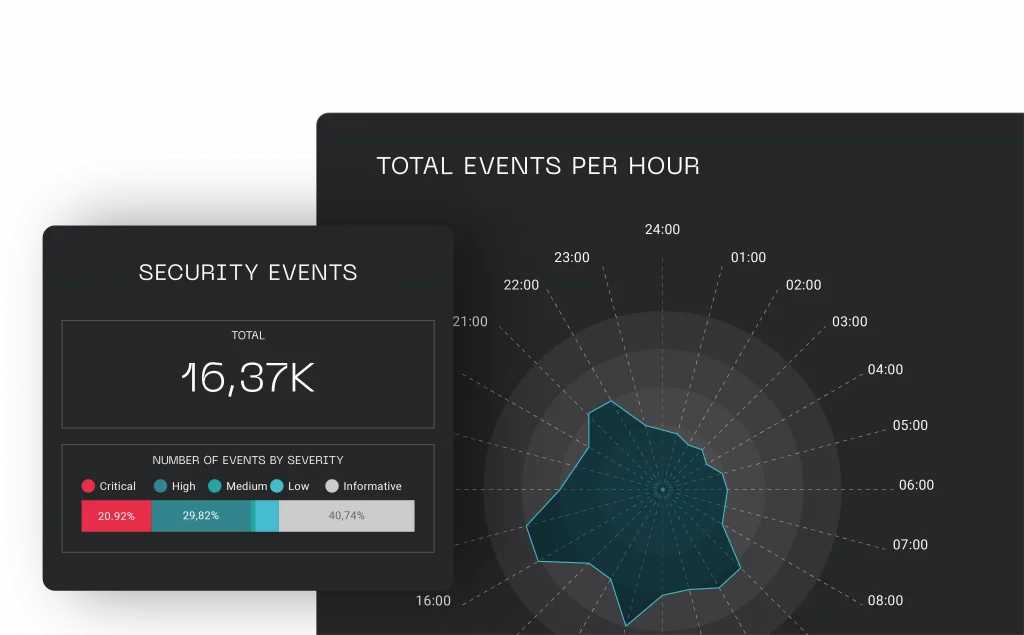
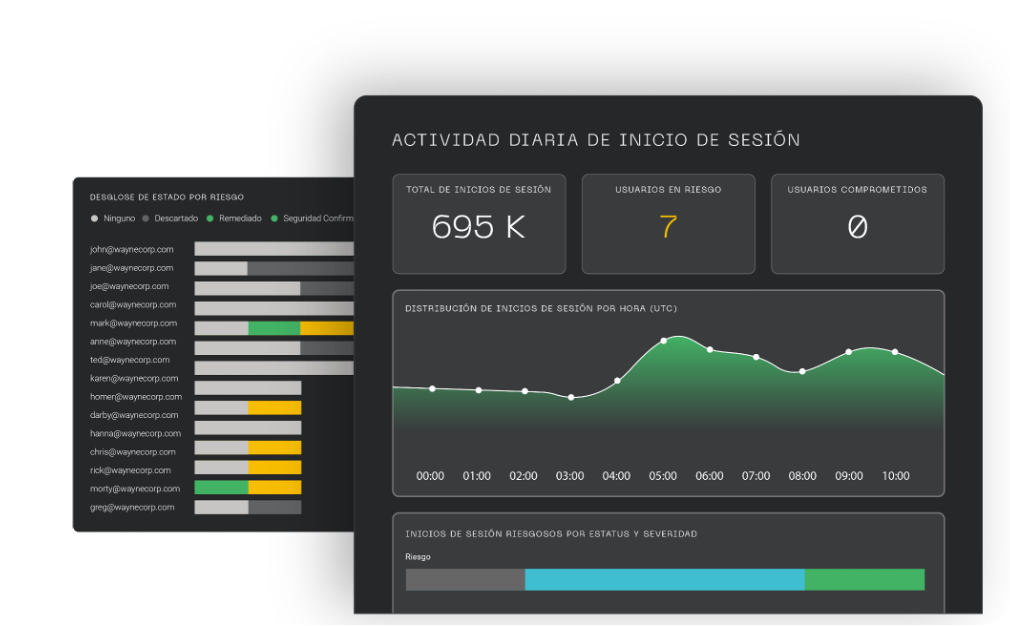
Meet Batuta, the first ever game-changing Cyber Defense Command and Control Center.
Magically simple cybersecurity.
Sign up for product updates, resources, and news
Subscribe to our mailing lists for the latest news, trends and events in cybersecurity.
Empowering businesses to seamlessly manage, measure, and mature their cybersecurity defenses to get secure and stay secure.
- +52 55 2211 0920
Privacy Policy © 2024 Metabase Q. All rights reserved.